This article covers,
what happened to 8chan and the name change to 8kun
When will it be back online?
The clear bias of Cloudflare, who hosted their servers
How the creators of Cloudflare worked on Project Honey Pot. . . why was that the name of the an operation, "Honeypot" associated with what lies beneath the blackmailing of government officials and others in a place of prominence with sex perversions, scandals and those including pedophilia? What's in a name and Are there Any Coincidences?
See which operations and groups Honey pot has been associated with and how it involves not only child sex trafficking but cases of SRA (satanic ritual abuse) which is consistently denied, even though there is evidence or distracted from by various mainstream media sources.
Operation Brownstone and Brownstar, what they mean and how they have become synonymous with blackmail.
See information leading into a connector article in how Hugh Hefner was used as a CIA asset including info on Jayne Mansion and other starlets of that era and what Really was known about he and Hefner's photographer and himself early on.
What various sources are stating,
Controversial site 8chan is back online for now and has a new name: 8kun
8chan is back online, but this time, under a new name. 8kun has taken over as the controversial image board’s new name.
After being down since August 5 due to the El Paso mass shooter’s involvement with the site, 8chan’s Twitter account tweeted Sunday, October 6, a video promoting the site’s new name and logo. The new logo is a snake in the shape of an 8.
8Chan also tweeted, “If you were previously a Board Owner on 8chan, please email us at admin@8kun.net with your shared secret if you are interested in migrating your board to 8kun.”
Before I finish this story, this is the latest info on this new site,
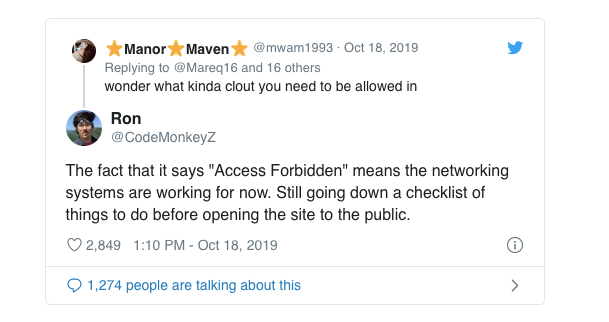
Jim Watkins has info on his YouTube channel and his son Ron Watkins (Codemonkey) I believe has a twitter . Codemonkey is in charge of the technical. They were hoping to have the 8kun.net online by the 17th (Thursday) and they did have it live for about 20 minutes but it went offline and has not been available to the public since. On Friday, when people asked about the odd error message they received when trying to access the website, Ron replied with this tweet.
Now it is not my intention to bad mouth anyone, but can't help but notice some obvious signs that this platform has some points to be disCerning about. Not unexpected as the chans Always have. They are just like any other place on satan's platform where you go to where you need, but stay away from the garbage and seediness.
I'm not sure if others have pointed this out, perhaps they have, but the elephant in the room is their logo. . .a snake eating the tail, ouroboros. So very satanic. That's all I will say as I understand people need a platform that allows free speech in order to communicate effectively. Now keep in mind, I do Not know their story behind Why they chose their logo. I do wish they would do what gab did, where they became independent when the hosting site for them tried to take away their free speech and they allow all, but not porn or threats of violence.
Unfortunately 8Kun's new host routs through China and they Are fooling themselves if they don't realize China has been linked to Google as they did China's search engine dragonfly for them.
They did migrate the boards of everyone who requested and I really appreciate that!
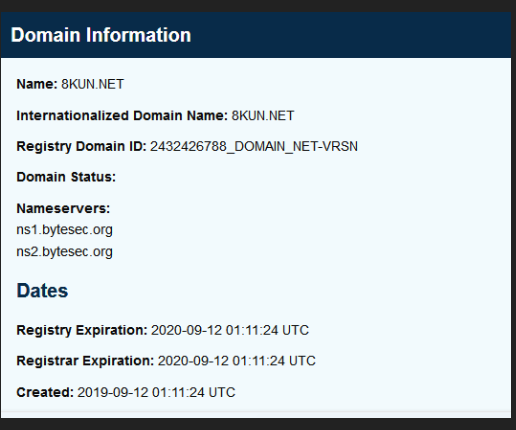
The previous suffix used, “chan,” refers to a child in Japanese, while the new “kun” suffix is usually referred to a young man.
According to CNET, the new 8kun site was registered as a Tucows domain on September 7.
“We only heard about 8kun.net being registered this morning as news outlets reported it, so we are looking into it,” said Tucows spokesperson Reg Levy, adding that as they find out more information, they would let Digital Trends know.
Also reported by Techspot, see link in sources below.
Jim Watkins, the owner of 8chan, had said the site would return after he spoke with the US House Committee on Homeland Security, which he did last month when testifying about 8chan’s role in the mass shootings. In a statement to the committee, he said: “8chan encourages vigorous debate, discussion, and changed opinions as a result of interacting through its image boards. Unlike platforms like Facebook or Twitter, there are no “speech police” to shut down poorly formed opinions, popular conspiracy theories, or hateful monologues.”
Interesting. ..Are Platforms Responsible for content posters drop? What about Free Speech? Who is culpable?
Why weren't Facebook and Twitter questioned about "possible threats posted" on their sites? Or if they were, why was it just a front because they continue to decide Who gets Free Speech and doesn't. Is that Really Free Speech?
Cloudflare cut off 8chan from its hosting support after the August shootings, saying in an August 5 blog post, “The rationale is simple: they have proven themselves to be lawless and that lawlessness has caused multiple tragic deaths.”
So They're responsible for independent citizen's actions? Really? Yet other platforms who are controlled by globalists bear Zero onus? As usual a Bunch of hypocrites!
So let's just take a look at Cloudfare,
- Cloudflare, Inc. is an American web infrastructure and website security company, providing content delivery network services, DDoS mitigation, Internet security, and distributed domain name server services.
It's important to remember,
A DDoS attack is short for "Distributed Denial of Service", and is the bigger brother of simpler denial-of-service attacks. The point of these exercises to take down a website or service, typically by flooding it with more information than the victim website can process.
- Cloudflare's services sit between a website's visitor and the Cloudflare user's hosting provider, acting as a reverse proxy for websites.
A type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client, appearing as if they originated from the proxy server itself. Unlike a forward proxy.
Quite often, popular web servers use reverse-proxying functionality, shielding application frameworks of weaker HTTP capabilities. In this context, "weaker" means limitations in ability to handle excessive load, and limitation in handling the entire variety of request formats that can adhere to HTTP(S) 1.x, HTTP(S) 2.x, or requests which may be hard to detect.
So can buffer incoming requests or transform one request into multiple requests and then synthesize the responses.
- Cloudflare has faced several controversies over its stance on providing technical support to online hate groups and terrorists—support it has defended based on the principle of free speech.
Okay, so What's the deal? Why are they flinching and caving NOW?
Why would they heel to a blatant radical progressive agenda that calls free speech "hate speech" though there is evidence msm changed the profile of the El Paso shooter and Google under their owned site YouTube took down footage showing actual evidence of what took place in the mosque shooting in New Zealand?
Are they part of the cabal, a globalist agenda?
One has to wonder as. . .
Created in 2009 by Matthew Prince, Lee Holloway, and Michelle Zatlyn, who had previously worked on Project Honey Pot. Cloudflare was launched at the September 2010 TechCrunch Disrupt conference. It received media attention in June 2011 for providing security services to the website of LulzSec, a black hat hacking group.
I get into what honey pot represents later, but let's break this down.
- Tech Crunch Disrupt conference,
According to AdAge who talked about the top 5 trends at this conference which remember got Cloudflare launched.
Important to not it took place in a former Merrill Lynch office. ..hmmm, you don't say!
Here then were the trends that spoke loudest to me according to Judy Shapiro
Tech Trend #1: Social media is quickly becoming the newly evolved direct marketing engine. Many of the new companies at the conference were focused on gathering and acting on social media data. This disproportionate focus was noted by not a few tweets who wondered what's up with that. My tweet response: "#tcdisrupt -- social media is about data mining because social media is really one big direct marketing engine."
Tech Trend #2: Mobile, social, commerce and proximity-based marketing will be mash-ups in new integrated ways that curate user experiences. If you are following the storyline so far, this next trend is the next logical step. The conference exhibited an abundance of ideas around how to execute this new Interaction Engine, especially in the areas of merging social media with commerce and content. We also saw ventures focused on harnessing the intelligence or market potential of social networks.
Tech Trend #3: New space will emerge for a systems approach so all these interactive technologies can operate within an integrated, marketing "Interaction Engine" model. The current state of new technology in this space reminds me of CRM before CRM became CRM, circa 1998. I was at Lucent at the time, and there were lots of disparate technologies to manage sales, support, service and call centers.
Lucent Technologies, Inc., was an American multinational telecommunications equipment company headquartered in Murray Hill, New Jersey, in the United States. It was established on September 30, 1996, through the divestiture of the former AT&T Technologies business unit of AT&T Corporation, which included Western Electric and Bell Labs.
Lucent means "they shine" in Latin. The name was applied in 1996 at the time of the split from AT&T.
- . .there's 3 sixes (as above so below so 9 inverted is 6)
The name was widely criticised, as the logo was to be, both internally and externally.
This same linguistic root also gives Lucifer, "the light bearer" (from lux, 'light', and ferre, 'to bear'), who is also a character in Dante's epic poem Inferno. Shortly after the Lucent renaming in 1996, Lucent's Plan 9 project released a development of their work as the Inferno OS in 1997. This extended the 'Lucifer' and Dante references as a series of punning names for the components of Inferno.
One source inside Lucent says that the logo is a Zen Buddhist symbol for "eternal truth", the Enso, turned 90 degrees and modified. Another source says it represents the mythic ouroboros, a snake holding its tail in its mouth.
Tech Trend #4: The deconstruction of major hubs as trust purveyors in favor of a "trust layer" delivered via social networks. It's hardly surprising that one of conferences undercurrent topics was Facebook and its recent controversy over privacy. While much of the debate centered on whether FB went too far, I was more interested in the larger, emerging trend where "Judy Consumer" is starting (very slowly to be sure) to shift away from the "mega-hub" sites as her trusted portal in favor of self-created, trusted portals based her social interactions and networks.
So they had already eroded privacy and were making that a "norm."
More dramatically, though, the anti "mega-hub site" sentiment spilled out with a fury when, in barely a few weeks, Facebook went from social media darling to devil. This backlash helps explain why four NYU kids over at The Diaspora Project tripled the amount they wanted to raise since people wanted to express their anti-FB sentiment.
Tech Trend #5: The continued, embarrassing lack of women in the startup, tech entrepreneur world. The conference's lack of women entrepreneurs was noticed early on and that theme carried forward throughout. Heck, most of the women there were either staffers or part of startup teams and there were barely a handful of women over the ancient age of (er ... dare I say) 40. The count was zero for women-led ventures (in a few instances, women were co-founders).
Cloudflare hosted the site of LulzSec (Sabu a member)
Lulz Security, commonly abbreviated as LulzSec, was a black hat computer hacking group that claimed responsibility for several high profile attacks, including the compromise of user accounts from Sony Pictures in 2011. The group also claimed responsibility for taking the CIA website offline. Some security professionals have commented that LulzSec has drawn attention to insecure systems and the dangers of password reuse. It has gained attention due to its high profile targets and the sarcastic messages it has posted in the aftermath of its attacks. One of the founders of LulzSec was computer security specialist Hector Monsegur, who used the online moniker Sabu. He later helped law enforcement track down other members of the organization as part of a plea deal. At least four associates of LulzSec were arrested in March 2012 as part of this investigation. British authorities had previously announced the arrests of two teenagers they allege are LulzSec members T-flow and Topiary.
Facing a sentence of 124 years in prison, Monsegur (originally from Puerto Rico) became an informant for the FBI, working with the agency for over ten months to aid them in identifying the other hackers from LulzSec and related groups. LulzSec intervened in the affairs of organizations such as News Corporation, Stratfor, UK and American law enforcement bodies and Irish political party Fine Gael.
Monsegur entered a guilty plea to 12 criminal charges, including multiple counts of conspiracy to engage in computer hacking, computer hacking in furtherance of fraud, conspiracy to commit access device fraud, conspiracy to commit bank fraud and aggravated identity theft, but became an informant rather than serve out the full sentence.
Monsegur served 7 months in prison after his arrest but had been free since then while awaiting sentencing. At his sentencing on May 27, 2014, he was given "time served" for co-operating with the FBI and set free under one year of probation
Information Monsegur provided also resulted in the arrest of two UK hackers: James Jeffery and Ryan Cleary
Cloudflare stated that it will "continue to abide by the law" and "serve all customers", further explaining "our proper role is not that of Internet censor.
In 2014, Cloudflare introduced an effort called Project Galileo in response to cyberattacks against vulnerable online targets, such as artists, activists, journalists, and human rights groups.
So in other words...they Do Choose whom to protect!
Many of these "mass shootings" have been found to Not be what MSM attempted to say they were. A great deal of evidence exists which some local news stations covered, but MSM Refused! Very Telling wouldn't you say?
- In 2019, Cloudflare announced that 600 users and organizations were participating in the project.
I'll Bet they did! So once again, controllers deciding who is Protected and who is Not. Sort of like the radical ideology of YouTube, owned by Google deciding whose content is seen and whose is buried!
I believe we can all see where Cloudflare is coming from!
Let's take a look at the Project the creators of Cloudflare came from
Remember. . .
Cloudflare was created in 2009 by Matthew Prince, Lee Holloway, and Michelle Zatlyn, who had previously worked on Project Honey Pot.
REALLY?
Project Honey Pot is a web-based honeypot network. It uses software embedded in web sites. It collects information about the IP addresses used when harvesting e-mail addresses in spam, bulk mailing, and other e-mail fraud. The project also solicits the donation of unused MX entries from domain owners.
Interesting they Dare to use a "Project" name notorious for being associated with the Sickest of crimes and predatory actions not just involving adults, but children.
For example,
In 2017, Dutch police used honeypot techniques to track down users of the darknet market Hansa.
If you search around you will see evidence that Hugh Hefner was used as an operative for the C_a for blackmail in what is known as compromising those in positions of power of influence in the "Honey Pot."
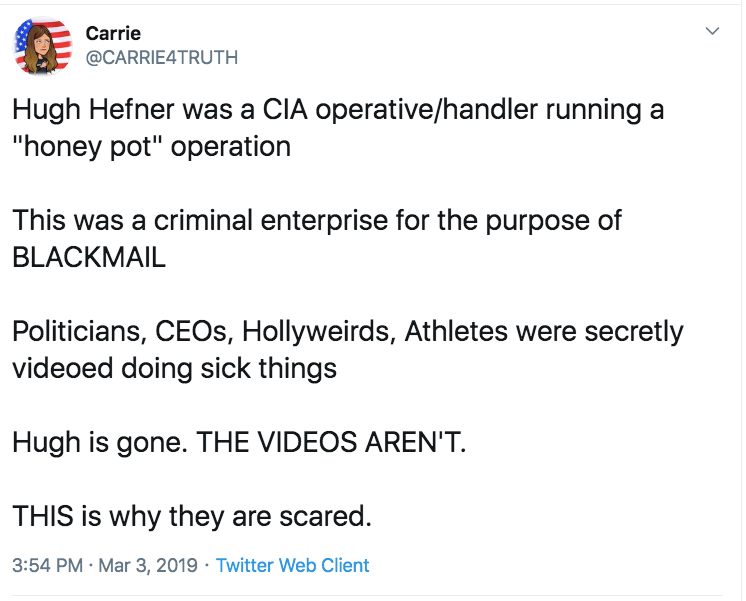
According to Gum Shoe News,

“People Magazine” spent a million dollars (a lot of money back then) investigating all of America’s orphanages and found the stories were true – identifying Bush (Snr), Cheney and Sununu as paedophiles. The story was never told by “People Magazine”. The journalist Veterans Today writer Stew Webb spoke to on many occasions in the late 1980s and early 1990s said he was never allowed to publish.
It is alleged Children from orphanages in Nebraska being flown around the United States by top Republican officials in order to engage in child sex orgies with America’s ruling elite. Vox News:
‘It is a fact that during the 1980’s, child sexual services were provided by top Republican officials… to the President of the United States at the time, George H.W. Bush. …It is a tale of child sex, murder, espionage, blackmail, and huge payoffs. And all the players are involved. From the White House to the CIA to the media barrons to the Republican elite – right down to the orphanages where they procured their victims.’
Former Republican Senator John Decamp was involved in a documentary called “Conspiracy of Silence” that exposed a network of religious leaders and Washington politicians who flew children to Washington D.C. for sex orgies. It was to air May 3, 1994 on the Discovery Channel. It is alleged, at the last minute, the rights to the documentary were purchased by unknown persons who had ordered all copies destroyed – and it was never aired.
Tried to use their Prison Planet link but it has been removed. Did a few reports on the Franklin Coverup a couple years back so here is one if you're not familiar,
Franklin Cover up part 3 Johnny Gosch ritualistic abuse victims Pedophile rings

Here is an article with sources on the Finders here,
This is Just the tip of the iceberg, but describes some.
Webb from Veterans Today writes (January 12 2015):
‘George HW Bush is a known evil pedophile, who ran a Congressional Blackmail Child Sex Ring during the 1980s known as “Operation Brownstone and Operation Brownstar”, and later to become known as “The Finders or The Franklin Coverup”.
…(the children were given) Coke or Pepsi with the VOODOO DRUG in it,
The caretakers (of the children) did not suspect a thing until 6 months later when their children were sitting in front of the TV watching the News and waiting for dinner, when many would jump up and point to the TV and say “He put his thing in me”.’
Accomplices – The Media and The Courts
What has become of the system? Have media barrons and judges been entrapped doing terrible and illegal acts, so are forced to protect the elite? Are they just scared for their lives?
So what happens when a victim tries to expose this lot?
Alicia Owens
Alicia Owens accused various people of sexual abuse in Omaha and was one of the victims of the Franklin Cover up. She told the court ‘elaborate tales’ of sexual abuse (just like the abuse victims are telling the Royal Commission in Australia). There was a financial scandal which eventually included sexual-abuse allegations, with claims of a supposed pedophile ring and rumors of satanic activity. But the court did not believe Owens. They punished her with a LONG jail sentenced for perjury (and two bad cheques). FranklinCaseOrg reports Owens was paroled in 2000 after serving 4 1/2 – three years before her release date.
This punishment of a sex abuse victim with jail was surely a deterrent for other victims.
Many of the links in Gum Shoe News for this particular article get a 404 Error so will provide other content links in sources.
Ted Gunderson worked long and hard in trying to expose this evil,
Ted Gunderson - The Franklin Coverup Investigations

According to a Reddit article from 2017,
Operation Brownstone and Operation Brownstar -- CIA's Network Abuse of Minors in Blackmail Leverage Arbitrage ('nambla' backronym)
Operation Brownstone
The CIA embroils politicians in sex scandals involving minors and then surreptitiously records it. They then use this as blackmail leverage to puppeteer the politician. They do this with business executives, activist leaders, celebrities and other public figures including news anchors. If they go against the CIA, their reputation is destroyed by a doxx and other scandalous revelating (Brian Williams, Dennis Hastert, Bill Cosby, etc). Now these people are not innocent. They did something bad, but there is an intelligence incentive to do this, which in some cases may very well blur the line between criminality and entrapment.
People such as Epstein and Alephantis, who have unusual amounts of political power, whose aquisition cannot be explained or is ill-gotten by some mean beyond simply money or 'social networking' (no one is that likeable), are very likely people working as contractors or within the agencies to blackmail people. They are more like private eyes who found very powerful dirt on other very powerful people.
Here is more information on this activity, which is synonymous with "brownstown operations", which has come to mean blackmail leverage.
When he mentions Alephantes. .. he is talking about the infant lover Alefantis whose name literally means Just that. I have done a few reports on him and in sources I'll put in the article related to just some of what went on with the bands at his "pizza place" from a Rachel Chandler article (child procurer of children for Epstein through the elite circles and talent agencies).
Posted byu/browneyeofprovidence
2 years ago
Operation Brownstone and Operation Brownstar -- CIA's Network Abuse of Minors in Blackmail Leverage Arbitrage ('nambla' backronym)
Operation Brownstone
The CIA embroils politicians in sex scandals involving minors and then surreptitiously records it. They then use this as blackmail leverage to puppeteer the politician. They do this with business executives, activist leaders, celebrities and other public figures including news anchors. If they go against the CIA, their reputation is destroyed by a doxx and other scandalous revelating (Brian Williams, Dennis Hastert, Bill Cosby, etc). Now these people are not innocent. They did something bad, but there is an intelligence incentive to do this, which in some cases may very well blur the line between criminality and entrapment.
People such as Epstein and Alefantis, who have unusual amounts of political power, whose aquisition cannot be explained or is ill-gotten by some mean beyond simply money or 'social networking' (no one is that likeable), are very likely people working as contractors or within the agencies to blackmail people. They are more like private eyes who found very powerful dirt on other very powerful people.
Here is more information on this activity, which is synonymous with "brownstown operations", which has come to mean blackmail leverage.
George Webb explains Brownstone operations
Corbett Eye Opener: The Real Hastert Scandal

Possible LASK link to diplomats

https://underthegrayline.wordpress.com/tag/operation-brownstone/
@azra/day-68-where-is-eric-braverman-or-long-island-serial-killer
http://shermsays.blogspot.com/2009/07/early-brownstone-operation-sex-and.html
You can find more info related to this 1987 NYT article in the Finders steemit link above.

From FBI Vault
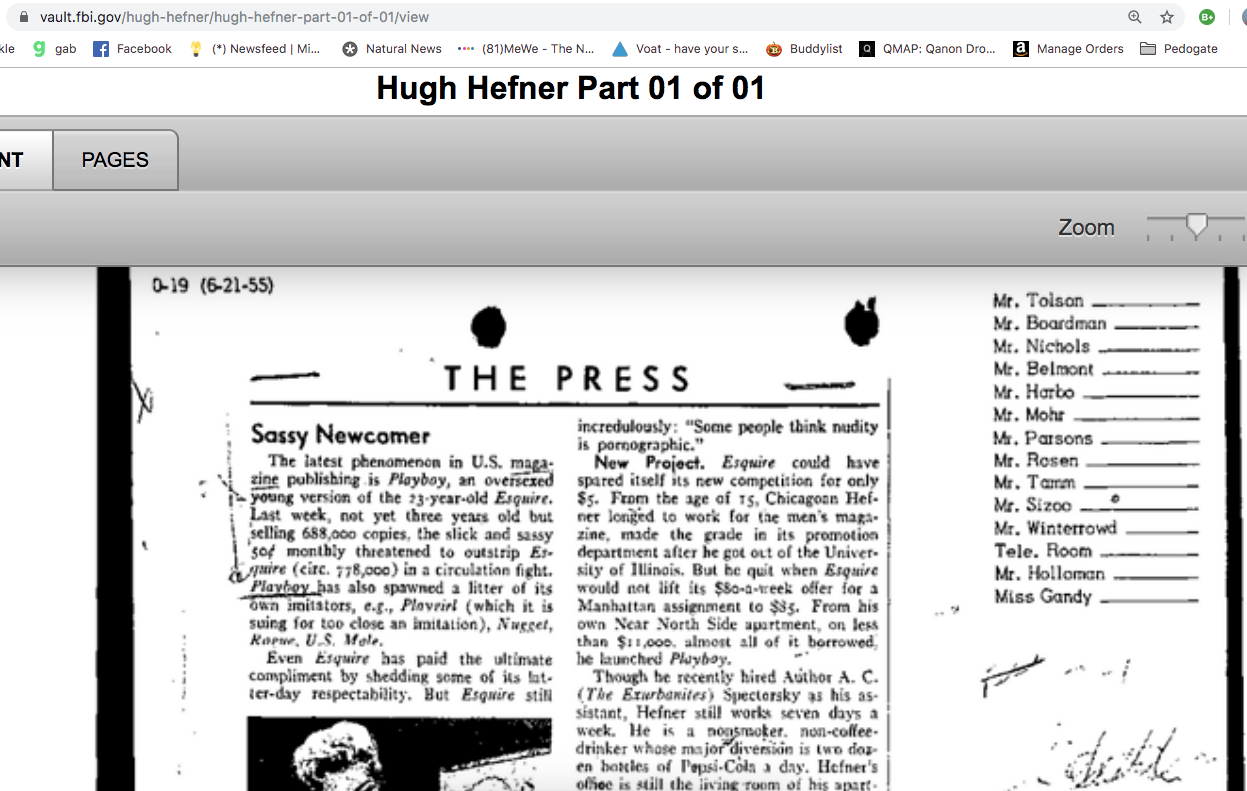
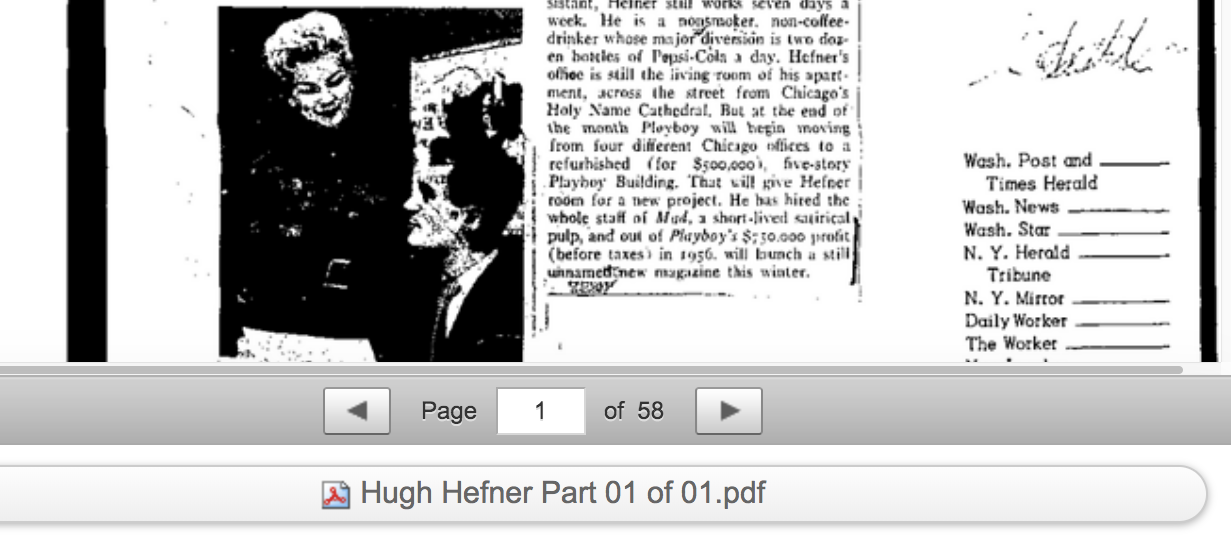



Notice, Jayne Mansfield
American film, theater, and television actress. She was also a nightclub entertainer and a singer, and one of the early Playboy Playmates. She was a major Hollywood sex symbol during the 1950s and early 1960s while under contract at 20th Century Fox. She was also known for her well-publicized personal life and publicity stunts, such as "wardrobe malfunctions".
She became the first major American actress in a Hollywood film to have a nude scene in Promises! Promises! (1963).
See a deeper dive on this including the FBI vault on playboy in this article,



See more on this in a connecting article here,
Sources,
https://www.digitaltrends.com/news/8chan-is-back-online-rebranded-as-8kun/
https://www.techspot.com/news/82279-8chan-relaunching-under-new-name-8kun.html
https://gumshoenews.com/2015/02/06/paedophiles-in-power-a-conspiracy-of-silence-and-cover-up-in-us/
https://www.veteranstoday.com/2015/01/09/is-any-story-evil-enough/
https://www.nytimes.com/1987/02/08/us/inquiry-spreads-on-6-children-and-cult.html
http://wootva.com/2019/10/08/8chan-growing-up-as-8kun-qanon-return-is-immanent/
https://vault.fbi.gov/hugh-hefner/hugh-hefner-part-01-of-01/view
https://maps.roadtrippers.com/stories/jayne-mansfield-bar
https://adage.com/article/digitalnext/trends-marked-techcrunch-disrupt-conference-2010/144174

