
Hello All,
Welcome to Steemit Crypto Academy Season 3, My self @stream4u, I am from India, and one of your crypto professors. I welcome you all to my class.
Previously we learned about the Blockchain and understood how it works, in that same we have also seen how a block performs in a blockchain and then what happens when data gets changed in one of the blocks in Blockchain. In the last course, we also see how hashes work with Blockchain and their major roles. Hope the previous course and then summary on it was cleared to everyone.
| One request, the way you engaged and commenting on Course posts, it will be good if you do the same on Summary posts also so that we will come to know that you understood about your submitted homework task, after all, Summary posts for you so that you can understand the overall about homework tasks and accordingly improve better in the next courses. We publish Summary Post every Monday. |
Now let's start with our new course for this week. In this course, we will go more in deep and see about CryptoGraphy.

Before I explain CryptoGraphy let me give you one example first then you will understand it in a better way. You all know Warren Buffett, why he has not used a computer or email conversation?
In past, Warren Buffett has sent one private email to his friend but after sending that email the Government has tracked/cached that email and then go through it, the email contains a private message about one of the big Companies, in next few days that information which Warren Buffett has sent privately to his friend was published in the newspaper and then Warren Buffett was shocked, after that he never send the emails.
Now, what if there is a system through which you can send your message privately and only that person can read/receive it which who you want to send without any drop in the middle, here CryptoGraphy works for you.
In technical terms, CryptoGraphy is the system that provides you a secure platform where you can communicate directly with the destination person in the presence of Third-Party services, and your communication will not drop, it will only remain in between the source and destination party.
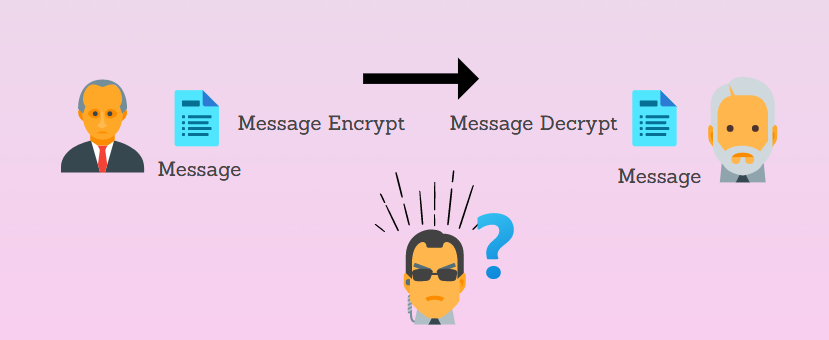
In this process, the encryption and key method are used to transform input in the encrypted format then based on keys functionality the message can be decrypted. The pain text which humans can read changes into the computer language which we call as encryption then only that person can read it who has a required key, after using this key the message change from encrypt to decrypt which mean again into the plain text.
Key Points
Sensitivity - Data privately rotate in between and the destination, no one can understand this data.
Trustworthiness - The data cannot be alerted/modify.
Non Rejection - The sender can not deny once the data has been sent.
Validation - Sender and receiver can verify each other identification and the source/destination for the information.

Cryptocurrencies are built on key cryptography, this concept uses a Private key that you can not disclose with anyone and it is only with you which you need to secretly store, then a Public key which you can share with other people, also it helps for the identification.

Not only the Public key and the Private key, cryptocurrencies also use another concept that is Address which use to send/receive the fund, and in the same, you can also see the balance fund.
- Public Key
It is one of the core parts of a blockchain that uses =d in multiple places to verify that the message is created into the Blockchain. Further, wallet creation and then sign the transaction which is depending on the Public chain. With the help of the public key, the public address gets generated by the hashing function. Public address similar to wallet address uses to send and receive the fund.
- Private Key
The private key gives you full control over your waller and assets in it, only a private key can use to send assets to the destination address. The wallet generates the Private key for you and then while sending funds some software automatically signs that transaction with your private key.
Now, let's take an example to understand how and where Public, Private keys CryptoGraphy are used in transactions.
Person A wants to send x amount/message to Person B.
Person A first publishes his Public key which Person B knows. Then with the help of Private Key Person A sing the message/send assets while doing this the Digital Signature added to this particular transaction, the Digital signature confirms that Person A is a sender or message creator, after it is processed from the Person A. Person B on the other hand can use the Public Key of Person A to receive the message.
Digital Signature.
Just like we sign on the hard copy, document the Digital Signature is also quite same which process with the help of Private key. Digital Signature is a very critical part of CryptoGraphy.
The Digital signature confirms that the author who signs the transaction has an individual Private Key. Depending on the Private key, every transaction gets a different Digital Signature.
Digital Signature depending on the two functionality.
- Sign - Transaction that we want to sign and the Private key, this help to produce is unique Digitale Signature to the Transaction.
Transaction -> Private Key -> Digital Signature
- Verify - The Digital Signature and the Public Key produce the output based on whether the digital signature is authenticated or not.
Transaction -> Public Key -> Digital Signature
When a transaction is signed by the author the transaction goes into the pool which is further processed by the miners. As mentioned above the Public key can be shared, here miners authenticate the transaction with the Public key of the sender, once this has been verified they process a transaction in the next block and then the money/transaction send from one wallet to another wallet.
It is impossible to find a Private key from a Public key, similarly, it is impossible to find a Public key from a Private key.
Now let's see how Cryptocurrency Wallets CryptoGraphy works and the Public-Private key role in this. Let's take an example of the real world which is BANK to understand what the wallet is and how the Public-Private key relates to it.
The Wallet address is similar to your Bank account number which you can share with anyone, then those who want to send you money can send it to your bank account number.
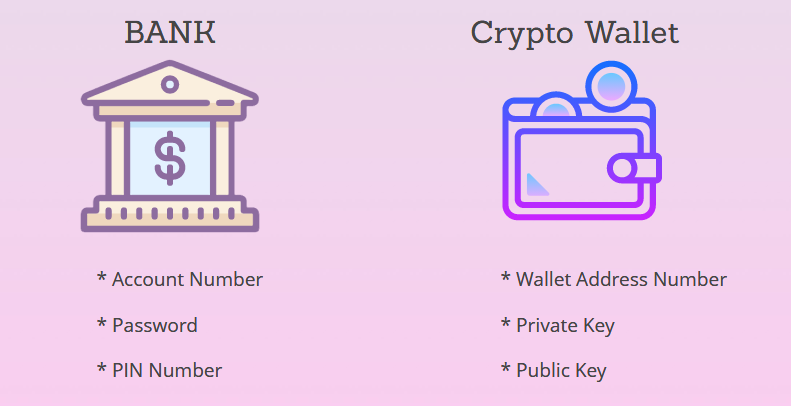
Crypto wallet address is similar to your Bank account, there will no issue if you share the Wallet address with others, actually it needs to share so that the other person can able to send you the assets.
The two cryptocurrency wallet addresses are never the same just like a bank account, which means no one can get your fund. But by Bank account, we can get the owner identification which is not the case in Cryptocurrency Wallets CryptoGraphy.
Example of Bitcoin address: 18LxzvGcJzSjDYJdYCHTe1G3i9ZGD26t9
We can see here the long length of the number, the combination of numbers ad characters, such an address can not be the same with another crypto wallet. Since Blockchain maintains transparency so that we can see how much fund this address has and how many transactions made yet, but as mentioned like BANK account we can not see the identification of the owner from the Crypto wallet address.
Similar to the Bank account when you want to login into your account and send funds you will need to use your password, this password we can not share with anyone to make sure that funds are secure in the account.
The Private key is similar to your Bank account and this also cant be shared with anyone. The private key allows you to control your fund into the Crypto wallet and the same use to send the fund to other wallets. The private key is linked to the specific crypto wallet.
The public key is the mathematically generated number that gives an extra security layer to make sure it should not get hacked.
Private Key: 03ff350d29213775158a608b51e3eE898e507fe47f2d2e8c674de
Public Key: 90b1ebcfc12a11dfc5161abaa8169469fe1601d531
These are the examples of Public and Private key, it is not possible for a human to understand it but computer system can understand that it is linked to each other.
Another example like a credit or debit card, when we purchase something with the help of a credit or debit card we need to enter a PIN number which is security for credit or debit cards. When we entered and the transaction was made, the fund does not physically move from your account number to the store. This is what the similar is Cryptocurrency Wallets CryptoGraphy, with Private key you confirmed the transaction then you can use another wallet number to transfer the fund which is the only way to send crypto assets in two wallets.
To understand the background functionality of Keys CryptoGraphy we will be going to use a below Demo made by Anders Brownworth.
Blockchain Demo: Public-Private Keys and Signing
So there are 4 sections we have under this Demo that are Keys, Signature, Transaction, Blockchain. Here, we will be demonstrating 2 sections Keys and Signature. In Homework Task you will be explaining these 2 sections again as per your understanding and practical, also the rest of all sections will be under Homework Task on which you will be explained according to your researching and practice on this Demo.
KEY's
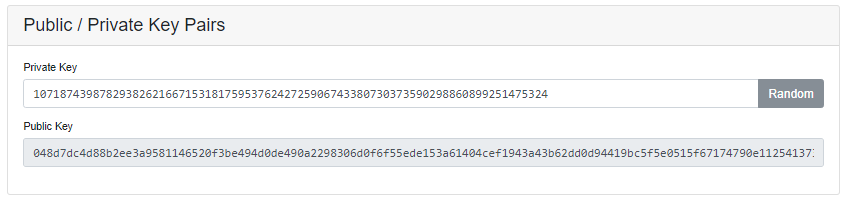
In this section, we can see how the Public key is linked to the Private key and how the Public key generates which is linked to the Private key.
When I click on the Radom so it will provide me the random numbers for the Private and Public keys. When I tried to manually type Private key it will provide me a different Public key that linked to the custom Private key.
So I simply try to put value 1 as a Private key and it generated a Public key which is linked to the Private key. I can not share my Private key which is 1 but I can share my Public key.
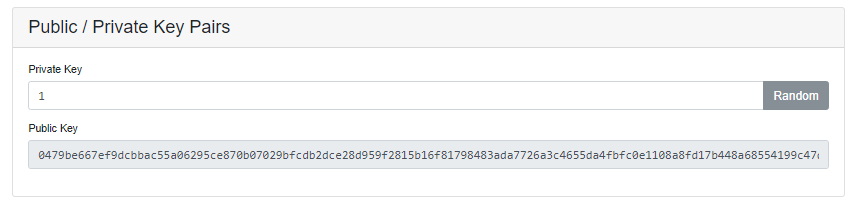
Public Key: 0479be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798483ada7726a3c4655da4fbfc0e1108a8fd17b448a68554199c47d08ffb10d4b8
For humans is it difficult to know the Private key from this Public key but computer systems know that the Private Key 1 is linked to this Public key.
Signature.
Note down that I put my private key as 1, now to get the signature value for my message/transaction, I will put some data as I enter "Steemit Crypto Academy" into the message.
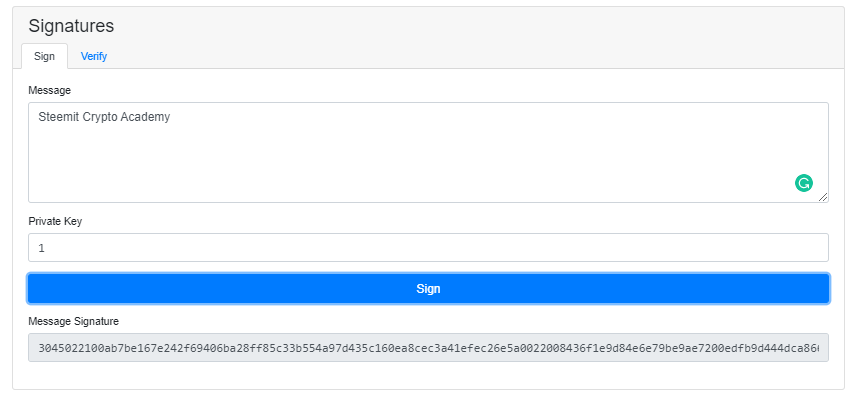
What we see here, the Private key is needed to process the transaction/message, and by singing it generates and provides Digital Signature to my message/transaction.
As mentioned above in the Sign section we can see here that, Transaction -> Private Key -> Digital Signature
Let's verify this transaction now, check the above public key.
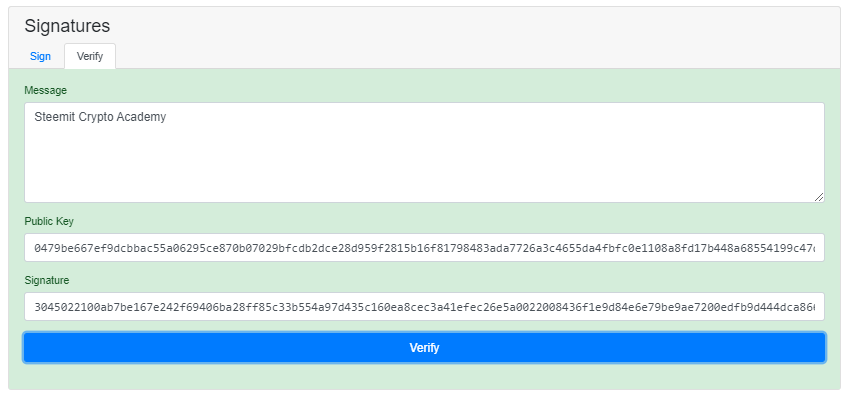
Here, I used the Public key of the sender and the Digital signature for the message. Everything is valid, clicking on Verify the transaction will get verified.
As seen above in the verify section, Transaction -> Public Key -> Digital Signature.
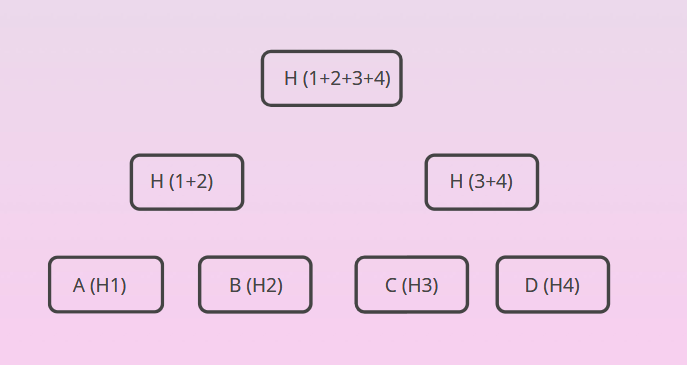
While checking the transaction in Blockchain Explorer did you see Merkle root in the details, check below.
To understand Merkle Root and Merkle Tree let's first understand what was the problem in the Blockchain that Merkle Tree solved.
The Blockchain is made with a thousand of Blocks, each Block has thousands of transactions and each transaction has a unique ID, here you can imagine how much memory and computing power gets utilized.
The solution is Merkle Tree which provides us the details about all transactions in a block. With the help of Merkle Tree, we can use only small data as needed while processing and verification of any transaction. It reduces computing power, memory, and also provides higher security.
How It Works?
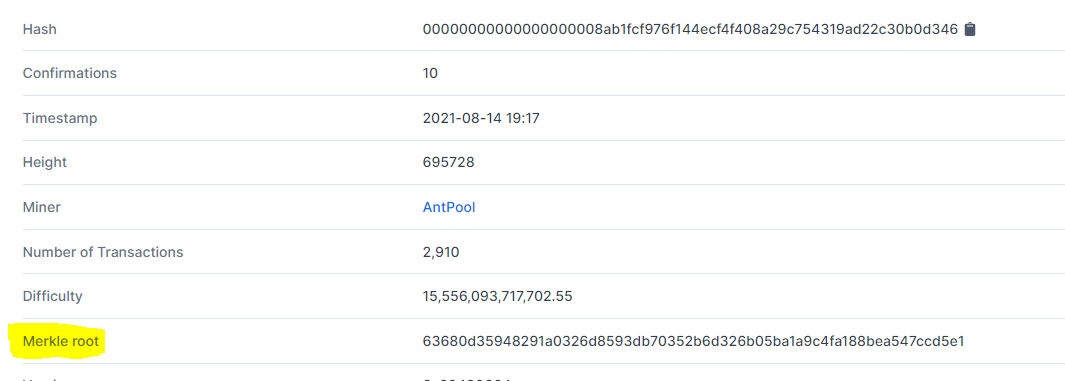
The Merkle Tree records all transactions in a block. The Merkle Tree continually calculates the hashing till the last one left which call as Merkle Root. In the above diagram, the top block is known as Merkle Root. The Merkle Root can be read from bottom to top.
The node has a hash of transaction data and the non-node has the same previous hash like if it is an odd number of Block then the last hash will be duplicate.
In the above diagram A, B, C, D are the transaction with their Hash value 1,2,3,4. The first two blocks' hash values will give results 1,2 and similarly, the next two blocks give results 3,4, then again hashed to generate the last hash which is 1234 that known as Merkle Root.
In this way, the Merkle Tee reduces the time, disk size, power and helps to find the specific transaction quickly.

Hope you liked this course as we see the inside view of CryptoGraphy, here we learned how CryptoGraphy works in Cryptocurrencies with their Keys, wallets, and transactions.
While making a Homework Task kindly make sure that this is the Advance Level course hence before start to work on this Homework Task, I will request first to understand the questions and accordingly work on it, research more, study, and understand it first then prepare a task with the details and own words.
You also need to focus on a presentation while working on a Homework Task, make sure you submit the homework task with a good presentation, try to use markdowns to highlight the important note in your task.
The title for the Homework Task will be in the format, Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u] - Let's Open The CryptoGraphy.
Below are the questions which you need to explain through your Homework Task.
- Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
- Explain the Public Key CryptoGraphy.
- Explain the Private Key CryptoGraphy.
- Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
- Explain what is Symmetric and Asymmetric cryptography?
- How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
- What is the Merkle trees and What its importance in blockchain?
- Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical. (Do study well for this topic)
9 Conclusion. (The overall understanding of CryptoGraphy)

Make sure you submit your Homework Task in the Steemit Crypto Academy community.
Users having a reputation of 60 or above, and having a minimum SP of 500(excluding any delegated-in SP) are eligible to partake in this Task.
All information contained in a Homework Task should be your own as plagiarism will not be tolerated.
Use images from copyright-free sources.
Add tag #stream4u-s3week8 & #cryptoacademy in your Homework Task and should be in the first two tags. Tag correctly otherwise the Task will not get visited in a sequence and on time.
Add me as @stream4u somewhere in your Homework Task.
This homework task will run from 16 August 2021 To 21 August 2021 Till Time- 11:59 PM UTC, make sure to submit before the time ends.
For any concerns, doubts, questions on homework tasks, you can ask me in the comment section below before making Task.
Thank You.
@stream4u
Crypto Professors : Steemit Crypto Academy


