
Photo by Edwin Hooper on Unsplash
So far I have studied different ways of stealing keys using scam links. The way of presenting the link is different, but the underlying process is always the same. The recent one is the comment which is about voting exnihilo.witness. Everyone knows exnihilo.witness who shares his witness rewards among supporters. This knowledge causes to simply attracts people to click the link given.
Let's go through the process.
This is the comment that you see :
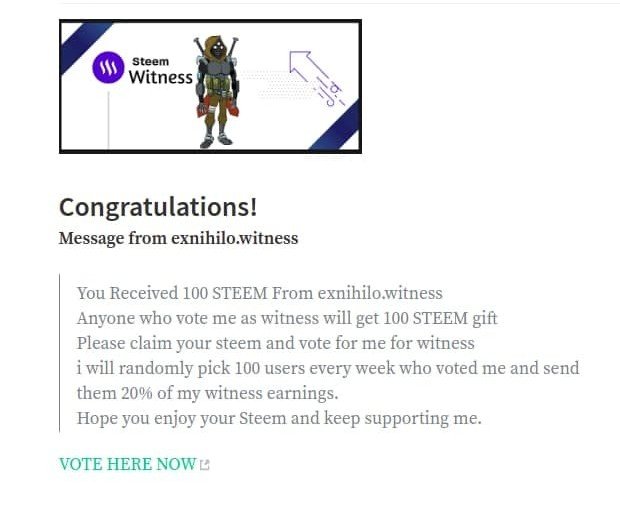
The first smart observation you must make is, the commenter is not exnihilo.witness.
If you right-click and copy the address behind the link, you can see the following link. I have edited all links to avoid you clicking them mistakenly.
https://t.co/JUP2b7xXXXtVd?amp=1
This link will take you to a website called, https://witness-voting.pqr.app/
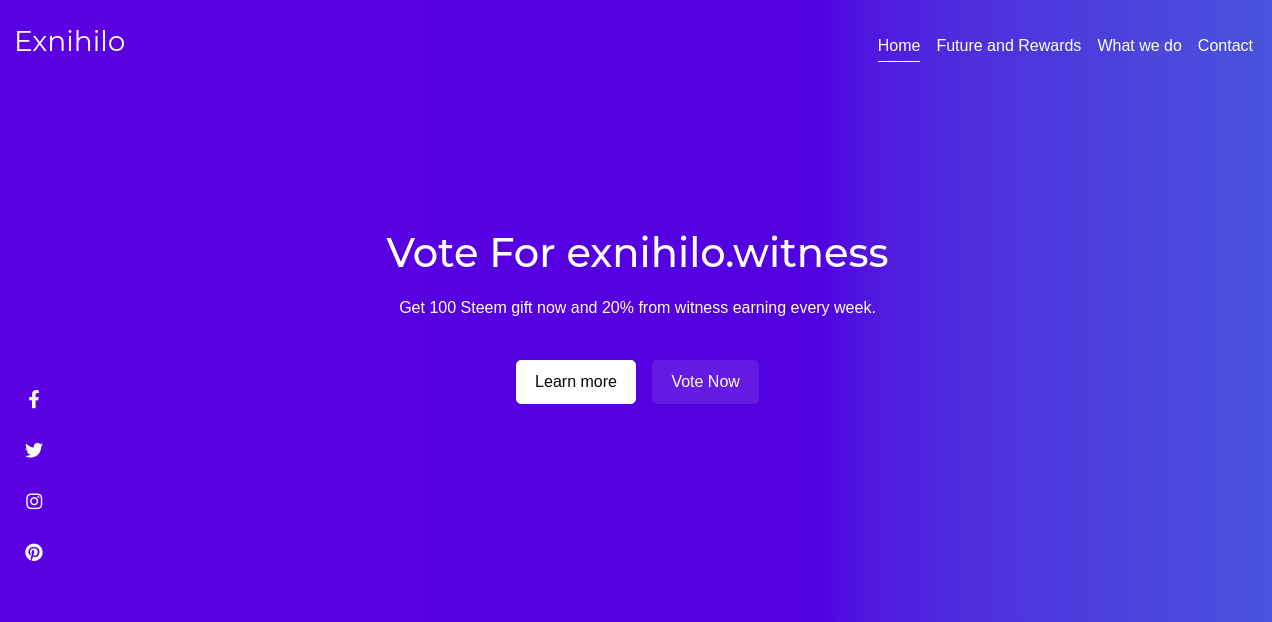
This is what you should see
Now to grab 100 STEEM, people tend to click on the 'VOTE NOW' button. It opens a modal for you as given below.
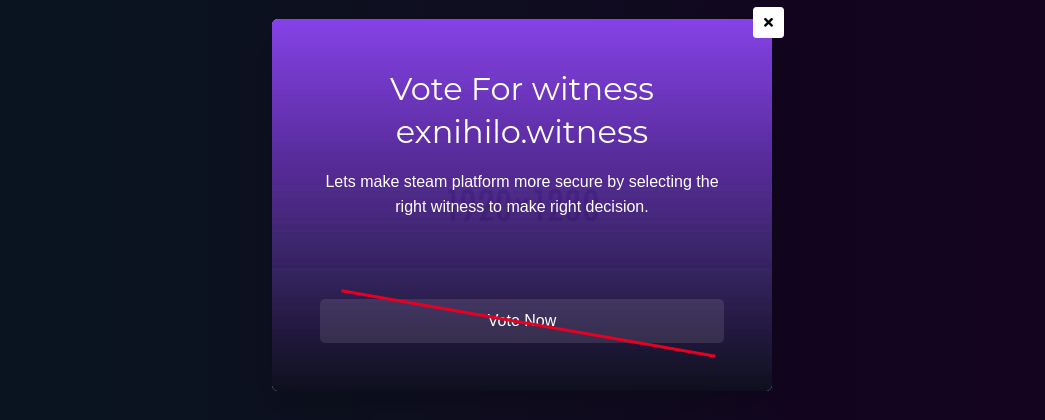
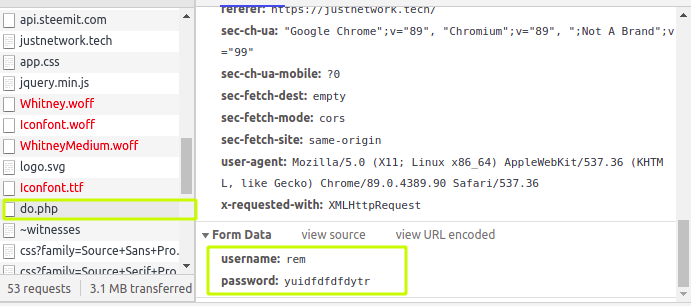
Now, I inspect this element to know the link behind it. Right-click on the page --> inspect . You can see something familiar.
onclick="href='https://justnetwork.tech/';"
If you don't remember why it is special, you have to read more from this article : Check the URL First, Before Submit Your Data . I have seen this URL with multiple dresses from time to time.
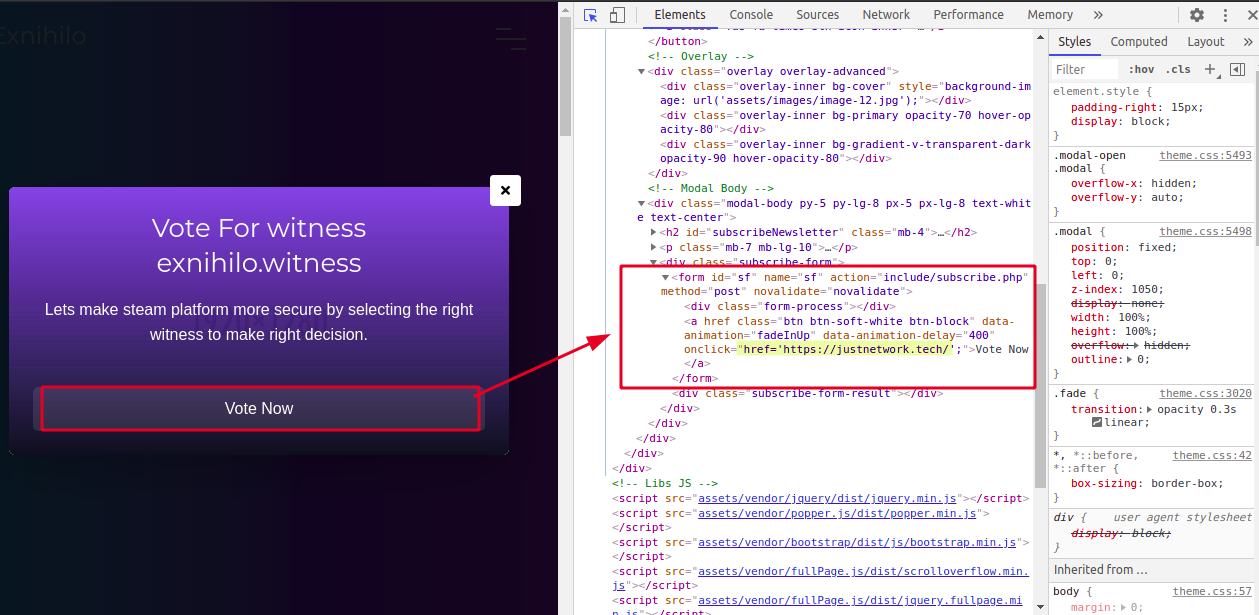
This time, this URL is dressed as steemconnect which is no longer in action. The user name and password taken by you is passed to an endpoint called do.php . The data can be saved in a database or a spreadsheet from the do.php function. In simple terms, you are sending your keys and username to someone else to do whatever he wants.
So that we must pay attention to not to give username and password for any unknown login except authorized logins by steemit.
