For those of you who have been living under a rock the Intel Management Engine is a separate processor on Intel motherboards that has access to your RAM and network to allow remote administration of your computer in business environments. Totally not the NSA's wet dream or anything. The irony of course is it seems to have been used by the Chinese in the South China sea dispute.
Malware Uses "Obscure" Intel CPU Feature to Steal Data and Avoid Firewalls
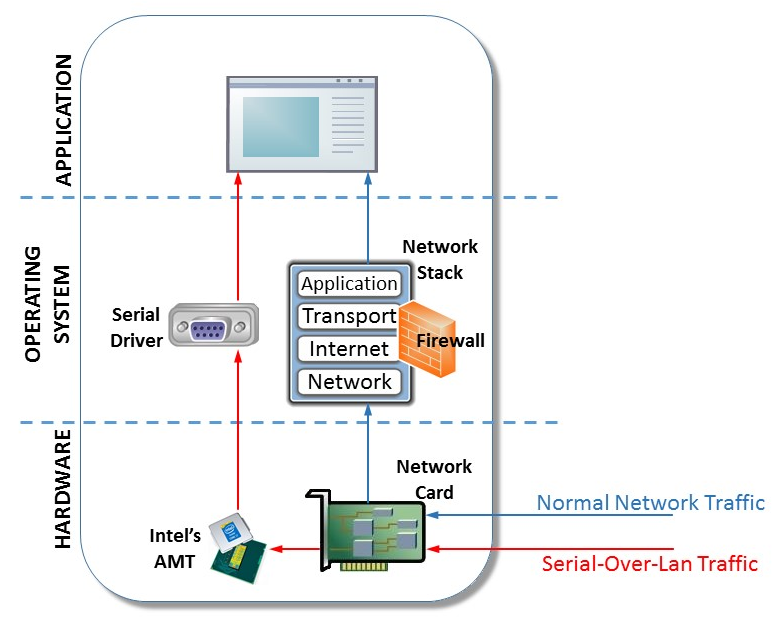
Microsoft's security team has come across a malware family that uses Intel's Active Management Technology (AMT) Serial-over-LAN (SOL) interface as a file transfer tool. Because of the way the Intel AMT SOL technology works, SOL traffic bypasses the local computer's networking stack, so local firewalls or security products won't be able to detect or block the malware while it's exfiltrating data from infected hosts.
Intel AMT SOL exposes hidden networking interface
This is because Intel AMT SOL is part of the Intel ME (Management Engine), a separate processor embedded with Intel CPUs, which runs its own operating system.
Intel ME runs even when the main processor is powered off, and while this feature looks pretty shady, Intel built ME to provide remote administration capabilities to companies that manage large networks of thousands of computers. In the ME component stack, AMT provides a remote management feature for Intel vPro processors and chipsets. The AMT SOL is a Serial-over-Lan interface for the Intel AMT remote management feature that exposes a virtual serial interface via TCP. Because this AMT SOL interface runs inside Intel ME, it is separate from the normal operating system, where firewalls and security products are provisioned to work. Furthermore, because it runs inside Intel ME, the AMT SOL interface will remain up and functional even if the PC is turned off, but the computer is still physically connected to the network, allowing the Intel ME engine to send or receive data via TCP.
Cyber-espionage group uses Intel AMT SOL for their malware
The good news is that Intel AMT SOL comes disabled by default on all Intel CPUs, meaning the PC owner or the local systems administrator has to enable this feature by hand. The bad news is that Microsoft discovered malware created by a cyber-espionage group that abuses the Intel AMT SOL interface to steal data from infected computers. Microsoft can't say if these state-sponsored hackers found a secret way to enable this feature on infected hosts, or they just found it active and decided to use it. The feature has been spotted with malware deployed against organizations and government agencies in South and Southeast Asia. The group that deployed this malware is only known under a codename given to it by Microsoft researchers — PLATINUM. Microsoft says it first spotted this group in 2009 and the group has historically targeted that region of the globe since its appearance.
PLATINUM is known for sophisticated hacks
PLATINUM is by far one of the most sophisticated hacking groups ever discovered. Last year, in a previous Microsoft report, the OS maker said the group was installing malware by abusing hotpatching — a mechanism that allows Microsoft to issue updates that tap into active processes and upgrade applications or the operating system without having to reboot the computer. Security researchers have talked about how crooks could use hotpatching to install malware in the past [1, 2], so Microsoft wasn't extremely surprised that somebody finally used it in live attacks. On the other hand, using Intel AMT SOL is something that has never been seen before, and PLATINUM's malware is the first to use it. This only strengthens Microsoft's theory that this group is made up of highly-trained and well-funded individuals, usually assembled as part of nation-state cyber-intelligence units.
Intel AMT SOL used because of its stealth features
Cyber-espionage groups, in general, are primarily interested in remaining hidden, so AMT SOL's firewall bypassing effect was the main reason the group decided to implement it. Fortunately, Microsoft says it was able to identify clues in the malware's operation that would allow its Windows Defender ATP security product to detect it before it accesses and initiates the AMT SOL interface. This provides companies with a warning that they might have been infected with the group's malware. When contacted by Microsoft, Intel said the PLATINUM group wasn't using any vulnerability in the Intel AMT SOL interface, but this was another classic case of bad guys using a technology developed for legitimate purposes to do bad things. Details about PLATINUM's targets and attacks are available in a report Microsoft released yesterday.
This post was brought to you by: http://8ch.net/tech/res/756500.html
