The origins of the National Security Agency can be traced back to April 28, 1917
- three weeks after the U.S. Congress declared war on Germany in World War I.
A code and cipher decryption unit was established as the Cable and Telegraph Section which was also known as the Cipher Bureau. It was headquartered in Washington, D.C. and was part of the war effort under the executive branch without direct Congressional authorization.
it was relocated in the army's organizational chart several times. On July 5, 1917, Herbert O. Yardley was assigned to head the unit. At that point, the unit consisted of Yardley and two civilian clerks. It absorbed the navy's Cryptanalysis functions in July 1918. World War I ended on November 11, 1918, and the army cryptographic section of Military Intelligence (MI-8) moved to New York City on May 20, 1919, where it continued intelligence activities as the Code Compilation Company under the direction of Yardley.
Black Chamber
After the disbandment of the U.S. Army cryptographic section of military intelligence, known as MI-8, in 1919, the U.S. government created the Cipher Bureau, also known as Black Chamber.
The Black Chamber was the United States' first peacetime cryptanalytic organization.
Jointly funded by the Army and the State Department, the Cipher Bureau was disguised as a New York City commercial code company; it actually produced and sold such codes for business use.
Its true mission, however, was to break the communications (chiefly diplomatic) of other nations. Its most notable known success was at the Washington Naval Conference, during which it aided American negotiators considerably by providing them with the decrypted traffic of many of the conference delegations, most notably the Japanese.
The Black Chamber successfully persuaded Western Union, the largest U.S. telegram company at the time, as well as several other communications companies to illegally give the Black Chamber access to cable traffic of foreign embassies and consulates.
Soon, these companies publicly discontinued their collaboration.
Or did they?
Despite the Chamber's initial successes, it was shut down in 1929 by U.S. Secretary of State Henry L. Stimson, who defended his decision by stating, "Gentlemen do not read each other's mail."
During World War II, the Signal Intelligence Service (SIS) was created to intercept and decipher the communications of the Axis powers. When the war ended, the SIS was reorganized as the Army Security Agency (ASA), and it was placed under the leadership of the Director of Military Intelligence.
On May 20, 1949, all cryptologic activities were centralized under a national organization called the Armed Forces Security Agency (AFSA). This organization was originally established within the U.S. Department of Defense under the command of the Joint Chiefs of Staff. The AFSA was tasked to direct Department of Defense communications and electronic intelligence activities, except those of U.S. military intelligence units.
Perhaps this was a Good Thing?
However, the AFSA was unable to centralize communications intelligence and failed to coordinate with civilian agencies that shared its interests such as the Department of State, Central Intelligence Agency (CIA) and the Federal Bureau of Investigation (FBI).
In December 1951, President Harry S. Truman ordered a panel to investigate how AFSA had failed to achieve its goals. The results of the investigation led to improvements and its redesignation as the National Security Agency.
The National Security Council issued a memorandum of October 24, 1952, that revised National Security Council Intelligence Directive (NSCID) 9. On the same day, Truman issued a second memorandum that called for the establishment of the NSA.
The actual establishment of the NSA was done by a November 4 memo by Robert A. Lovett, the Secretary of Defense, changing the name of the AFSA to the NSA, and making the new agency responsible for all communications intelligence.
Since President Truman's memo was a classified document, the existence of the NSA was not known to the public at that time. Due to its ultra-secrecy the U.S. intelligence community referred to the NSA as "No Such Agency"


Did much if it get to where it is today concerning Intellectual Property? You decide with disCERNment!
@artistiquejewels/hillary-clinton-more-than-meets-the-eye-patents-intellectual-property-planes-a-crashing-mysterious-dying-oh-my-allegedly-of
In the 1960s, the NSA played a key role in expanding U.S. commitment to the Vietnam War by providing evidence of a North Vietnamese attack on the American destroyer USS Maddox during the Gulf of Tonkin incident.
A secret operation, code-named "MINARET", was set up by the NSA to monitor the phone communications of Senators Frank Church and Howard Baker, as well as key leaders of the civil rights movement, including Martin Luther King Jr., and prominent U.S. journalists and athletes who criticized the Vietnam War.
However, the project turned out to be controversial, and an internal review by the NSA concluded that its Minaret program was "disreputable if not outright illegal".
n the aftermath of the Watergate scandal, a congressional hearing in 1975 led by Senator Frank Church revealed that the NSA, in collaboration with Britain's SIGINT intelligence agency Government Communications Headquarters (GCHQ), had routinely intercepted the international communications of prominent anti-Vietnam war leaders such as Jane Fonda and Dr. Benjamin Spock.
People were appalled by that as they should be, but where are the appalled today when platforms attempt to censor information?
The Agency tracked these individuals in a secret filing system that was destroyed in 1974.
Following the resignation of President Richard Nixon, there were several investigations of suspected misuse of FBI, CIA and NSA facilities.
The investigation uncovered NSA's wiretaps on targeted U.S. citizens.
In 1986, the NSA intercepted the communications of the Libyan government during the immediate aftermath of the Berlin discotheque bombing. The White House asserted that the NSA interception had provided "irrefutable" evidence that Libya was behind the bombing, which U.S. President Ronald Reagan cited as a justification for the 1986 United States bombing of Libya.
In 1999, a multi-year investigation by the European Parliament highlighted the NSA's role in economic espionage in a report entitled 'Development of Surveillance Technology and Risk of Abuse of Economic Information'. That year, the NSA founded the NSA Hall of Honor, a memorial at the National Cryptologic Museum in Fort Meade, Maryland. The memorial is a, "tribute to the pioneers and heroes who have made significant and long-lasting contributions to American cryptology". NSA employees must be retired for more than fifteen years to qualify for the memorial.
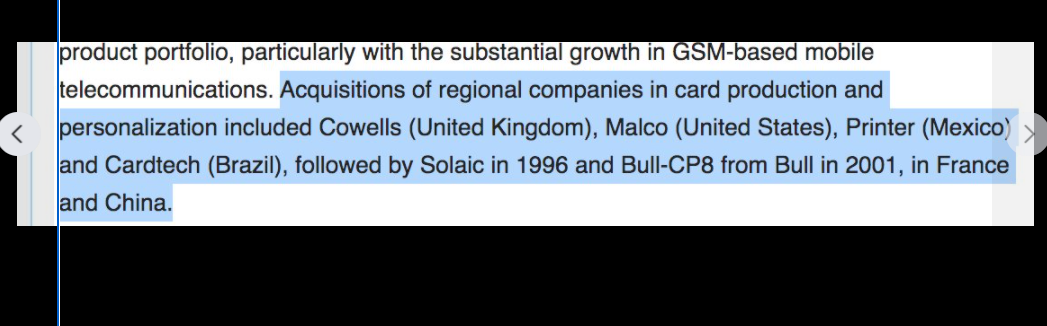
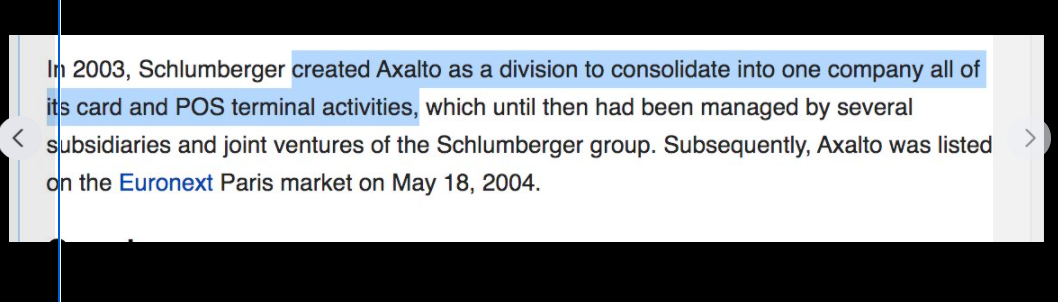
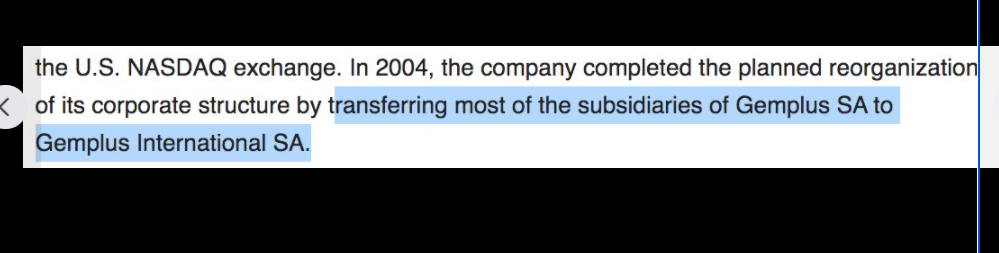
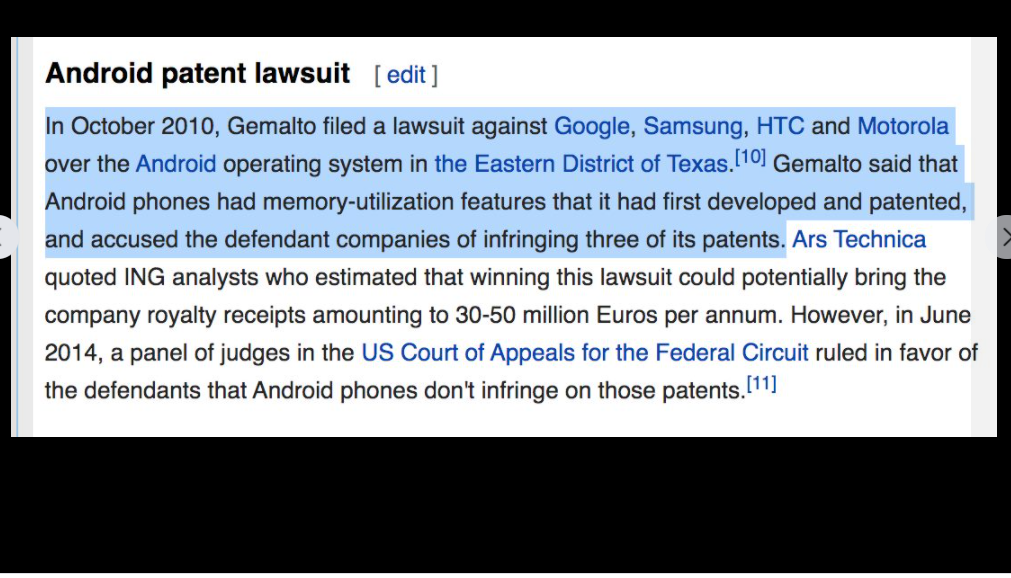
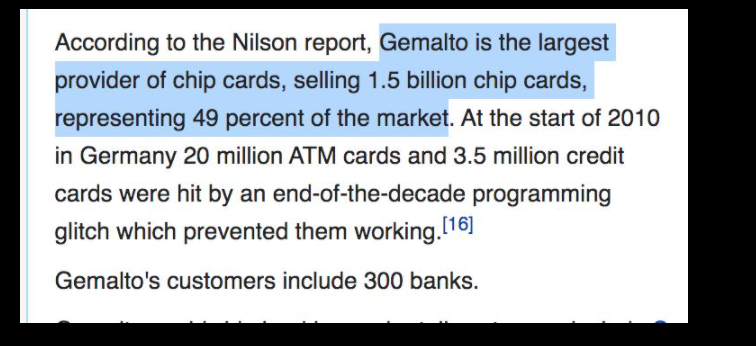
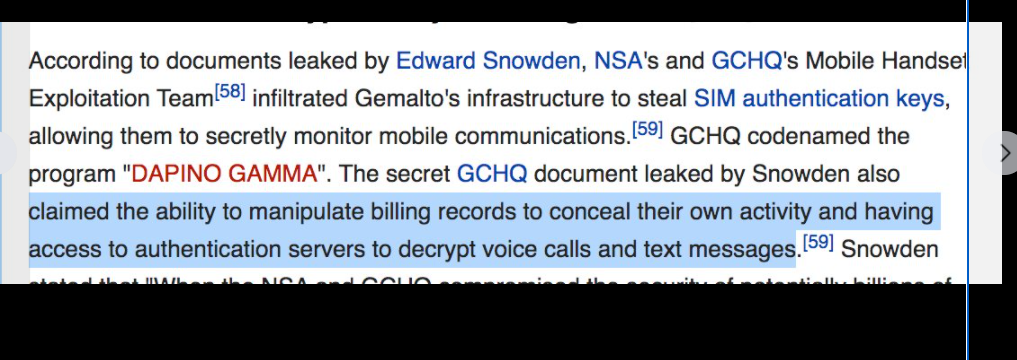
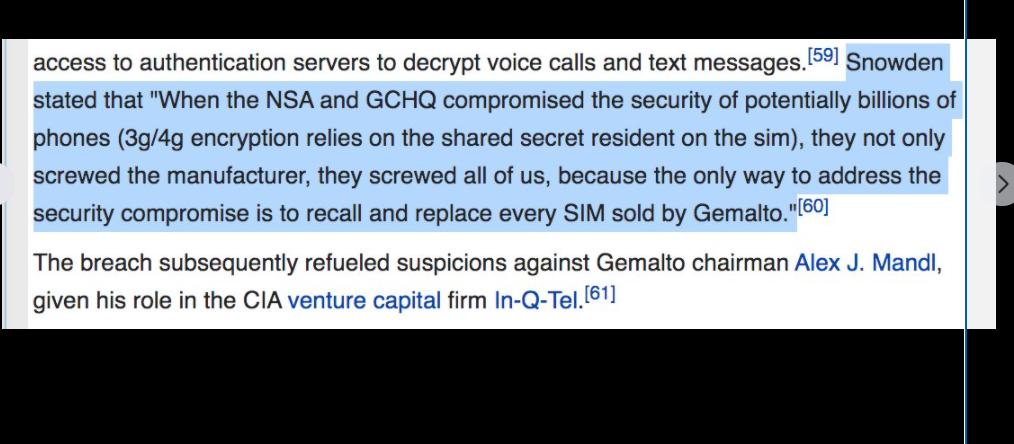
In-Q-Tel, formerly Peleus and In-Q-It, is an American not-for-profit venture capital firm based in Arlington, Virginia. It invests in high-tech companies to keep the Central Intelligence Agency, and other intelligence agencies, equipped with the latest in information technology in support of United States intelligence capability.
See their investments inside of here by flipping through the Frame Photos all Fully sourced!
It's Going to be BIBLICAL!
How long before Mathematically Impossible?
Facebook Frames Tunnel just found between Mexico and CA with quite the system and What is the Deal with 3M.
How do they Link into What Bob Dylan Knows? How about his latest release Murder Most Foul 17 min. long. Coincidence? #ThereAreNoCoincidences
https://www.facebook.com/melissa.mcgarity.14/posts/10220452639120536
Hear a deep dive report here while working or doing chores,
3M MASKS, CO'S THEY OWN PHARMA RIKER LABS, DIGITAL AUDIO INCLUDING LENNON, FINGERPRINT ID, SECURITY
NSA's infrastructure deteriorated in the 1990s as defense budget cuts resulted in maintenance deferrals. On January 24, 2000, NSA headquarters suffered a total network outage for three days caused by an overloaded network. Incoming traffic was successfully stored on agency servers, but it could not be directed and processed.
The agency carried out emergency repairs at a cost of $3 million to get the system running again. (Some incoming traffic was also directed instead to Britain's GCHQ for the time being.) Director Michael Hayden called the outage a "wake-up call" for the need to invest in the agency's infrastructure.
In the 1990s the defensive arm of the NSA—the Information Assurance Directorate (IAD)—started working more openly; the first public technical talk by an NSA scientist at a major cryptography conference was J. Solinas' presentation on efficient Elliptic Curve Cryptography algorithms at Crypto 1997.
The IAD's cooperative approach to academia and industry culminated in its support for a transparent process for replacing the outdated Data Encryption Standard (DES) by an Advanced Encryption Standard (AES).
Cybersecurity policy expert Susan Landau attributes the NSA's harmonious collaboration with industry and academia in the selection of the AES in 2000—and the Agency's support for the choice of a strong encryption algorithm designed by Europeans rather than by Americans—to Brian Snow, who was the Technical Director of IAD and represented the NSA as cochairman of the Technical Working Group for the AES competition, and Michael Jacobs, who headed IAD at the time.
Brian Snow
- In his early career Snow was a mathematics professor at Ohio University, where he helped develop the college's computer science department.
- In 1971 he started working at the NSA. During the 1970s and 1980s he designed cryptographic components and secure systems.
- Several cryptographic systems employed by the U.S. government and military have used his algorithms for such purposes as nuclear command and control, tactical voice communications, and network security.
Neal Koblitz and Alfred Menezes have written that Snow was a strong supporter of the transition from RSA to Elliptic Curve Cryptography (ECC) as a public key cryptographic technology:
...ECC started to get strong support from the NSA's Information Assurance Directorate (IAD) during the time when Snow was the technical director and Mike Jacobs was the head of IAD.
It's important to note. . .
- IAD (Information Assurance Directorate ) is the defensive arm of the NSA
- SIGINT (Signals Intelligence) is the offensive arm
Cybersecurity policy expert Susan Landau attributes the NSA's harmonious collaboration with industry and academia in the selection of the Advanced Encryption Standard (AES) in 2000 — and the Agency's support for the choice of a strong encryption algorithm designed by Europeans rather than by Americans — in part to Snow, who represented the NSA as cochairman of the Technical Working Group for the AES competition.
After the terrorist attacks of 11 September 2001, the NSA believed that it had public support for a dramatic expansion of its surveillance activities. According to Koblitz and Menezes, the period when the NSA was a trusted partner with academia and industry in the development of cryptographic standards came to an end when, as part of the change in the NSA in the post-September 11 era, Snow was replaced as Technical Director and could no longer effectively oppose proposed actions by the offensive arm of the NSA:
Who runs "academia" where they charge vast amounts to get their education filled with a Rockefeller Foundation curriculum?
What corporations, foundations, institutes and charities funded by the elite sitting in high places of control like Facebook, Twitter and corporate owned media run and steer Industry?
So Snow was opposing strict standards to keep the United States safe and Not have foreign interference? Interesting how he is touted as a hero by progressives.
In the aftermath of the September 11 attacks, the NSA created new IT systems to deal with the flood of information from new technologies like the Internet and cellphones.
ThinThread, Trailblazer and Turbulence
ThinThread contained advanced data mining capabilities. It also had a "privacy mechanism"; surveillance was stored encrypted; decryption required a warrant. The research done under this program may have contributed to the technology used in later systems.
ThinThread was cancelled when Michael Hayden chose Trailblazer, which did not include ThinThread's privacy system.
ThinThread prototype that protected privacy and Trailblazer awarded contract to develop a program that didn't protect citizen's privacy. Interesting!
Why No Privacy and Whose idea?
The "change in priority" consisted of the decision made by the director of NSA General Michael V. Hayden to go with a concept called Trailblazer, despite the fact that ThinThread was a working prototype that claimed to protect the privacy of U.S. citizens. ThinThread was dismissed and replaced by the Trailblazer Project, which lacked the privacy protections. A consortium led by Science Applications International Corporation was awarded a $280 million contract to develop Trailblazer in 2002.
Trailblazer Project ramped up in 2002 and was worked on by Science Applications International Corporation (SAIC), Boeing, Computer Sciences Corporation, IBM, and Litton Industries.
Some NSA whistleblowers complained internally about major problems surrounding Trailblazer. This led to investigations by Congress and the NSA and DoD Inspectors General. The project was cancelled in early 2004.
A group of former NSA workers—Kirk Wiebe, William Binney, Ed Loomis, and Thomas A. Drake, along with House Intelligence Committee staffer Diane Roark (an expert on the NSA budget)—believed the operational prototype system called ThinThread was a better solution than Trailblazer, which was just a concept on paper at the time.
They reported to the DoD Inspector General office in 2002 about mismanagement and the waste of taxpayer money at the NSA surrounding the Trailblazer program. In 2007 the FBI raided the homes of these people, an evolution of President Bush's crackdown on whistleblowers and "leaks" after the New York Times disclosed a separate program [NSA warrantless surveillance controversy].
In 2010, one of the people who had helped the IG in the ensuing investigation, NSA official Thomas Andrews Drake, was charged with espionage, part of the Obama administration's crackdown on whistleblowers and "leaks".
The original charges against him were later dropped and he pleaded to a misdemeanor.
See sources for more information on the NSA Warrantless Surveillance Controversy.
Turbulence started in 2005. It was developed in small, inexpensive "test" pieces, rather than one grand plan like Trailblazer. It also included offensive cyber-warfare capabilities, like injecting malware into remote computers.
Congress criticized Turbulence in 2007 for having similar bureaucratic problems as Trailblazer.
It was to be a realization of information processing at higher speeds in cyberspace.
Turmoil program is NSA’s global passive SIGINT apparatus. TURMOIL is a “high-speed passive collection systems intercept [for] foreign target satellite, microwave, and cable communications as they transit the globe." Presumably all this collection is related to Internet data (DNI), rather than other forms of SIGINT.
NSA collects using TURMOIL through a variety of sources. One of those is the RAMPART-A program, which provides foreign third-party “collection against long-haul international leased communications through special access initiatives with world-wide SIGINT partnerships.
The Internet links that are tapped through RAM-A have “access to over 3 Terabits per second” of data, and “every country code in the world is seen at one or more RAMPART-A collection accesses”.
In other words, friendly communications companies provide access to their backbone links, and those “partners work the fiber projects under the cover of an overt Comsat [communications satellite] effort."
It is likely that the other RAMPART projects, such as “RAMPART-M for access to undersea cables” and “RAMPART-T for land-based cables, in cooperation with CIA” contribute to the TURMOIL collection platform.
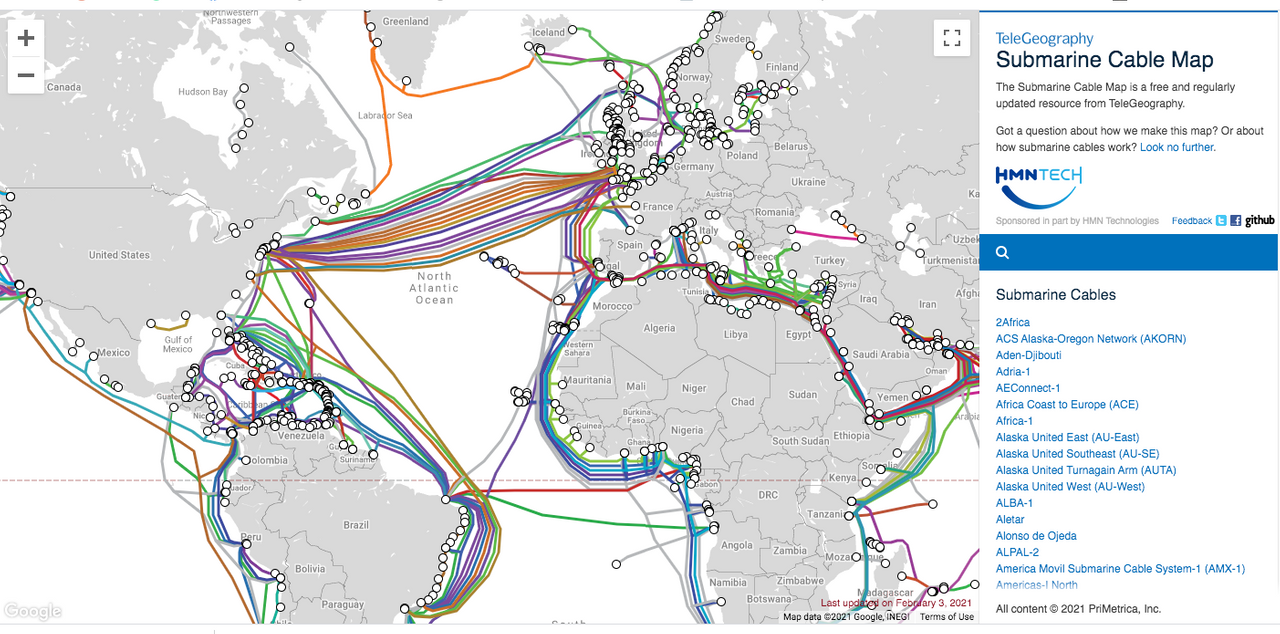
One other specific program that contributes to TURMOIL is the MUSCULAR program, in which the NSA tapped the fiber optic links of Google and Yahoo’s datacenters.
MUSCULAR and another cable-tapping program called INCENSER are part of the WINDSTOP project, rather than RAMPART, access to which occurs through a second party, reported to be GCHQ . There are likely several other cable-tapping programs that contribute to TURMOIL.
A unique aspect of the TURMOIL program is that it operates on the packet level, rather than operating on full sessions. Communications on the Internet, such as an email or webpage, are broken down into tiny pieces called packets when they are transmitted, allowing each small piece of data to take the fastest route possible to its destination.
When all the packets arrive at the destination, they are reassembled and made whole again. This reassembly, and grouping related email messages and webpages, is what the NSA refers to as “sessionized” data, since the data are full sessions rather than broken-down packets.
The massive extent of the NSA's spying, both foreign and domestic, was revealed to the public in a series of detailed disclosures of internal NSA documents beginning in June 2013.
Most of the disclosures were leaked by former NSA contractor Edward Snowden. On 4 September 2020, the NSA's surveillance program was ruled unlawful by the US Court of Appeals.
The court also added that the US intelligence leaders, who publicly defended it, were not telling the truth.
NSA's eavesdropping mission includes radio broadcasting, both from various organizations and individuals, the Internet, telephone calls, and other intercepted forms of communication. Its secure communications mission includes military, diplomatic, and all other sensitive, confidential or secret government communications.
According to a 2010 article in The Washington Post, "[e]very day, collection systems at the National Security Agency intercept and store 1.7 billion e-mails, phone calls and other types of communications. The NSA sorts a fraction of those into 70 separate databases."
Because of its listening task, NSA/CSS has been heavily involved in cryptanalytic research, continuing the work of predecessor agencies which had broken many World War II codes and ciphers like in Purple, Venona project, and JN-25).
Purple Dragon
Venona
VENONA
According to NSA dot gov news. . .
The U.S. Army's Signal Intelligence Service, the precursor to the National Security Agency, began a secret program in February 1943 later codenamed VENONA.
The mission of this small program was to examine and exploit Soviet diplomatic communications but after the program began, the message traffic included espionage efforts as well.
Although it took almost two years before American cryptologists were able to break the KGB encryption, the information gained through these transactions provided U.S. leadership insight into Soviet intentions and treasonous activities of government employees until the program was canceled in 1980.
The VENONA files are most famous for exposing Julius (code named LIBERAL) and Ethel Rosenberg and Reealing give indisputable evidence of their involvement with the Soviet spy ring.
The first of six public releases of translated VENONA messages was made in July 1995 and included 49 messages about the Soviets' efforts to gain information on the U.S. atomic bomb research and the Manhattan Project. Over the course of five more releases, all of the approximately 3,000 VENONA translations were made public.
JN-25
See more information involving Snowden inside of here with verified sources.
@artistiquejewels/the-corona-satellites-and-contact-tracers-remember-corona-means-crown-that-comes-into-play
Echelon was created in the incubator of the Cold War.
It is a legacy system, and several NSA stations are closing.
NSA/CSS, in combination with the equivalent agencies in the United Kingdom (Government Communications Headquarters), Canada [Communications Security Establishment], Australia [Australian Signals Directorate], and New Zealand [Government Communications Security Bureau], otherwise known as the UKUSA group, was reported to be in command of the operation of the so-called ECHELON system.
Its capabilities were suspected to include the ability to monitor a large proportion of the world's transmitted civilian telephone, fax and data traffic.
During the early 1970s, the first of what became more than eight large satellite communications dishes were installed at Menwith Hill. Investigative journalist Duncan Campbell reported in 1988 on the "ECHELON" surveillance program, an extension of the UKUSA Agreement on global signals intelligence SIGINT, and detailed how the eavesdropping operations worked. On November 3, 1999 the BBC reported that they had confirmation from the Australian Government of the existence of a powerful "global spying network" code-named Echelon, that could "eavesdrop on every single phone call, fax or e-mail, anywhere on the planet" with Britain and the United States as the chief protagonists. They confirmed that Menwith Hill was "linked directly to the headquarters of the US National Security Agency (NSA) at Fort Meade in Maryland".
Echelon
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the United States with the aid of four other signatory states to the UKUSA Security Agreement: Australia, Canada, New Zealand, and the United Kingdom, also known as the Five Eyes.
By the end of the 20th century, the system referred to as "ECHELON" had evolved beyond its military and diplomatic origins into "a global system for the interception of private and commercial communications" (mass surveillance and industrial espionage).
Former NSA employee Margaret Newsham claims that she worked on the configuration and installation of software that makes up the ECHELON system while employed at Lockheed Martin, from 1974 to 1984 in Sunnyvale, California, in the United States, and in Menwith Hill, England, in the UK.
At that time, according to Newsham, the code name ECHELON was NSA's term for the computer network itself. Lockheed called it P415. The software programs were called SILKWORTH and SIRE.
A satellite named VORTEX intercepted communications. An image available on the internet of a fragment apparently torn from a job description shows Echelon listed along with several other code names.
Britain's The Guardian newspaper summarized the capabilities of the ECHELON system as follows:
A global network of electronic spy stations that can eavesdrop on telephones, faxes and computers. It can even track bank accounts. This information is stored in Echelon computers, which can keep millions of records on individuals. Officially, however, Echelon doesn't exist.
Former NSA analyst Perry Fellwock, under pseudonym Winslow Peck, first blew the whistle on ECHELON to Ramparts in 1972, where he gave commentary revealing a global network of listening posts and his experiences working there. He also included revelations such as the existence of nuclear weapons in Israel in 1972, the widespread involvement of CIA and NSA personnel in drugs and human smuggling, and CIA operatives leading Nationalist Chinese (Taiwan) commandos in burning villages inside PRC borders.
In 1982, James Bamford, investigative journalist and author wrote The Puzzle Palace, an in-depth look inside the workings of the NSA, then a super-secret agency, and the massive eavesdropping operation under the codename "SHAMROCK". The NSA has used many codenames, and SHAMROCK was the codename used for ECHELON prior to 1975.
In 1988, Margaret Newsham, a Lockheed employee under NSA contract, disclosed the ECHELON surveillance system to members of congress. Newsham told a member of the US Congress that the telephone calls of Strom Thurmond, a Republican US senator, were being collected by the NSA. Congressional investigators determined that "targeting of US political figures would not occur by accident, but was designed into the system from the start.
Also in 1988, an article titled "Somebody's Listening", written by investigative journalist Duncan Campbell in the New Statesman, described the signals intelligence gathering activities of a program code-named "ECHELON".
James Bamford describes the system as the software controlling the collection and distribution of civilian telecommunications traffic conveyed using communication satellites, with the collection being undertaken by ground stations located in the footprint of the downlink leg.
A detailed description of ECHELON was provided by the New Zealand journalist Nicky Hager in his 1996 book Secret Power: New Zealand's Role in the International Spy Network.
Two years later, Hager's book was cited by the European Parliament in a report titled "An Appraisal of the Technology of Political Control"
In March 1999, for the first time in history, the Australian government admitted that news reports about the top secret UKUSA Agreement were true. Martin Brady, the director of Australia's Defence Signals Directorate (DSD, now known as Australian Signals Directorate, or ASD) told the Australian broadcasting channel Nine Network that the DSD "does co-operate with counterpart signals intelligence organisations overseas under the UKUSA relationship.
In 2000, James Woolsey, the former Director of the US Central Intelligence Agency, confirmed that US intelligence uses interception systems and keyword searches to monitor European businesses.
Lawmakers in the United States feared that the ECHELON system could be used to monitor US citizens. According to The New York Times, the ECHELON system has been "shrouded in such secrecy that its very existence has been difficult to prove." Critics said the ECHELON system emerged from the Cold War as a "Big Brother without a cause".
They poke you in the eye with shows like Big Brother in their "reality" series.
In July 2000, the Temporary Committee on the ECHELON Interception System was established by the European parliament to investigate the surveillance network. It was chaired by the Portuguese politician Carlos Coelho, who was in charge of supervising investigations throughout 2000 and 2001.
In May 2001, as the committee finalized its report on the ECHELON system, a delegation travelled to Washington, D.C. to attend meetings with US officials from the following agencies and departments:
US Central Intelligence Agency (CIA)
US Department of Commerce (DOC)
US National Security Agency (NSA)
All meetings were cancelled by the US government and the committee was forced to end its trip prematurely. According to a BBC correspondent in May 2001, "The US Government still refuses to admit that Echelon even exists."
On 5 September 2001, the European parliament voted to accept the report.
The European Parliament stated in its report that the term ECHELON is used in a number of contexts, but that the evidence presented indicates that it was the name for a signals intelligence collection system.
The report concludes that, on the basis of information presented, ECHELON was capable of
- interception and content inspection of telephone calls
- fax, e-mail and other data traffic globally through the interception of communication bearers including
- satellite transmission
- public switched telephone networks (which once carried most Internet traffic)
- microwave links
Two internal NSA newsletters from January 2011 and July 2012, published as part of the Snowden-revelations by the website The Intercept on 3 August 2015, for the first time confirmed that NSA used the code word ECHELON and provided some details about the scope of the program: ECHELON was part of an umbrella program with the code name FROSTING, which was established by the NSA in 1966 to collect and process data from communications satellites. FROSTING had two sub-programs
TRANSIENT: for intercepting Soviet satellite transmissions
ECHELON: for intercepting Intelsat satellite transmissions
The UKUSA intelligence community was assessed by the European Parliament (EP) in 2000 to include the signals intelligence agencies of each of the member states:
the Government Communications Headquarters of the United Kingdom,
the National Security Agency of the United States,
the Communications Security Establishment of Canada,
the Australian Signals Directorate of Australia, and
the Government Communications Security Bureau of New Zealand.
The EP report concluded that it seemed likely that ECHELON is a method of sorting captured signal traffic, rather than a comprehensive analysis tool.
In 2001, the EP report (p. 54 ff) listed the following ground stations as likely to have, or to have had, a role in intercepting transmissions from telecommunications satellites:
Hong Kong (since closed)
Australian Defence Satellite Communications Station (Geraldton, Western Australia)
RAF Menwith Hill (Yorkshire, UK) Map (reportedly the largest Echelon facility)
Misawa Air Base (Japan) Map
GCHQ Bude, formerly known as GCHQ CSO Morwenstow (Cornwall, UK) Map
Pine Gap (Northern Territory, Australia – close to Alice Springs) Map
Sugar Grove (West Virginia, US) Map (since closed)
Yakima Training Center (Washington, US) Map (since closed)
GCSB Waihopai (New Zealand)
GCSB Tangimoana (New Zealand
CFS Leitrim (Ontario, Canada)
Teufelsberg (Berlin, Germany) (closed 1992) – listening in to the Eastern Bloc
**Historical Comms((
The ability to intercept communications depends on the medium used, be it radio, satellite, microwave, cellular or fiber-optic. During World War II and through the 1950s, high-frequency ("short-wave") radio was widely used for military and diplomatic communication and could be intercepted at great distances. The rise of geostationary communications satellites in the 1960s presented new possibilities for intercepting international communications.
In 1964, plans for the establishment of the ECHELON network took off after dozens of countries agreed to establish the International Telecommunications Satellite Organisation (Intelsat), which would own and operate a global constellation of communications satellites.
In 1966, the first Intelsat satellite was launched into orbit. From 1970 to 1971, the Government Communications Headquarters (GCHQ) of Britain began to operate a secret signal station at Morwenstow, near Bude in Cornwall, England. The station intercepted satellite communications over the Atlantic and Indian Oceans. Soon afterwards, the US National Security Agency (NSA) built a second signal station at Yakima, near Seattle, for the interception of satellite communications over the Pacific Ocean.
In 1981, GCHQ and the NSA started the construction of the first global wide area network (WAN). Soon after Australia, Canada, and New Zealand joined the ECHELON system. The report to the European Parliament of 2001 states: "If UKUSA states operate listening stations in the relevant regions of the earth, in principle they can intercept all telephone, fax, and data traffic transmitted via such satellites.
Testimony before the European Parliament indicated that separate but similar UKUSA systems are in place to monitor communication through undersea cables, microwave transmissions, and other lines.
The role of satellites in point-to-point voice and data communications has largely been supplanted by fiber optics. In 2006, 99% of the world's long-distance voice and data traffic was carried over optical-fiber. The proportion of international communications accounted for by satellite links is said to have decreased substantially to an amount between 0.4% and 5% in Central Europe. Even in less-developed parts of the world, communications satellites are used largely for point-to-multipoint applications, such as video. Thus, the majority of communications can no longer be intercepted by earth stations; they can only be collected by tapping cables and intercepting line-of-sight microwave signals
Sources and connecting articles/reports
https://www.archives.gov/research/guide-fed-records/groups/457.html
https://www.nsa.gov/news-features/declassified-documents/cryptologic-histories/
https://web.archive.org/web/20120220104120/http://auscannzukus.net/
Random Curves: Journeys of a Mathematician. Springer-Verlag.
https://www.bartleby.com/topics/nsa-warrantless-surveillance-controversy
https://lawaspect.com/nsa-warrantless-surveillance-and-rights-of-privacy/
https://robert.sesek.com/2014/9/unraveling_nsa_s_turbulence_programs.html
https://www.submarinecablemap.com/
https://apps.dtic.mil/dtic/tr/fulltext/u2/a561426.pdf
https://theintercept.com/2019/05/29/nsa-sidtoday-surveillance-intelligence/
https://www.nsa.gov/news-features/declassified-documents/venona/
https://www.nsa.gov/about/cryptologic-heritage/center-cryptologic-history/pearl-harbor-review/jn25/
https://theintercept.com/document/2015/02/19/dapino-gamma-cne-presence-wiki/
https://www.duncancampbell.org/content/echelon
https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-explained
https://www.saturdayeveningpost.com/2014/04/a-brief-history-of-the-nsa/
