I am a network engineer. I decided to write about it from that perspective since I personally have to interact with hacking attempts frequently. Overall, I will say that any statement of "definitive" proof is bullshit when it comes to the internet unless they have raided a house in Russia, or the place a Russian is staying in the United States and confiscated the persons computer or caught them in the act "physically".

Looking at the servers you will get IP addresses where the activity and connections to the computers you are inspecting came from these are going to come in the form of either Internet Protocol 4 (aka IPv4) or Internet Protocol 6 (aka IPv6). Most activity still occurs in IPv4 though it has been running out of IP addresses for awhile.
If you have the address that the activity is coming from you can perform a WHOIS look up on it to find out whom that address is currently owned by. This will not go down to a specific person. It will instead tell you that it is part of a block owned by some place such as Comcast, AT&T, Verizon, etc. It will also tell you an address for the company office. It is with this information that you can determine if the address the "hack" is coming from is Russian, Chinese, United States, etc.
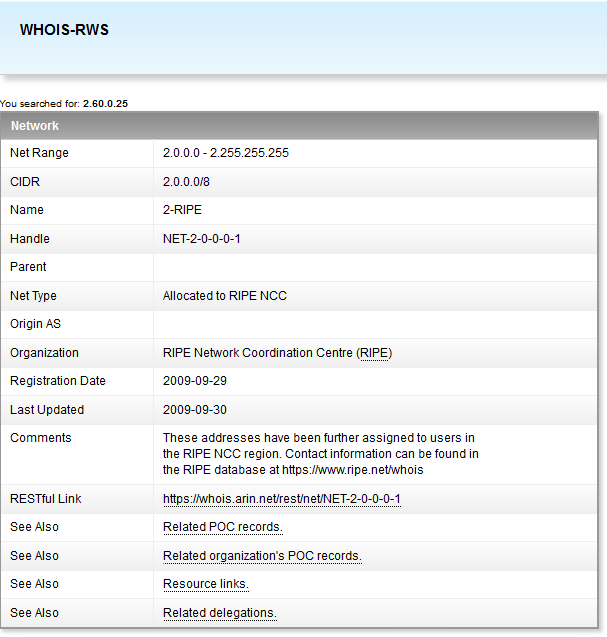
Or can you?
In reality you can determine that the last IP before the machine being hacked came from that. You cannot actually determine that the hack originated from the country of that IP without getting to that machine and also inspecting it.
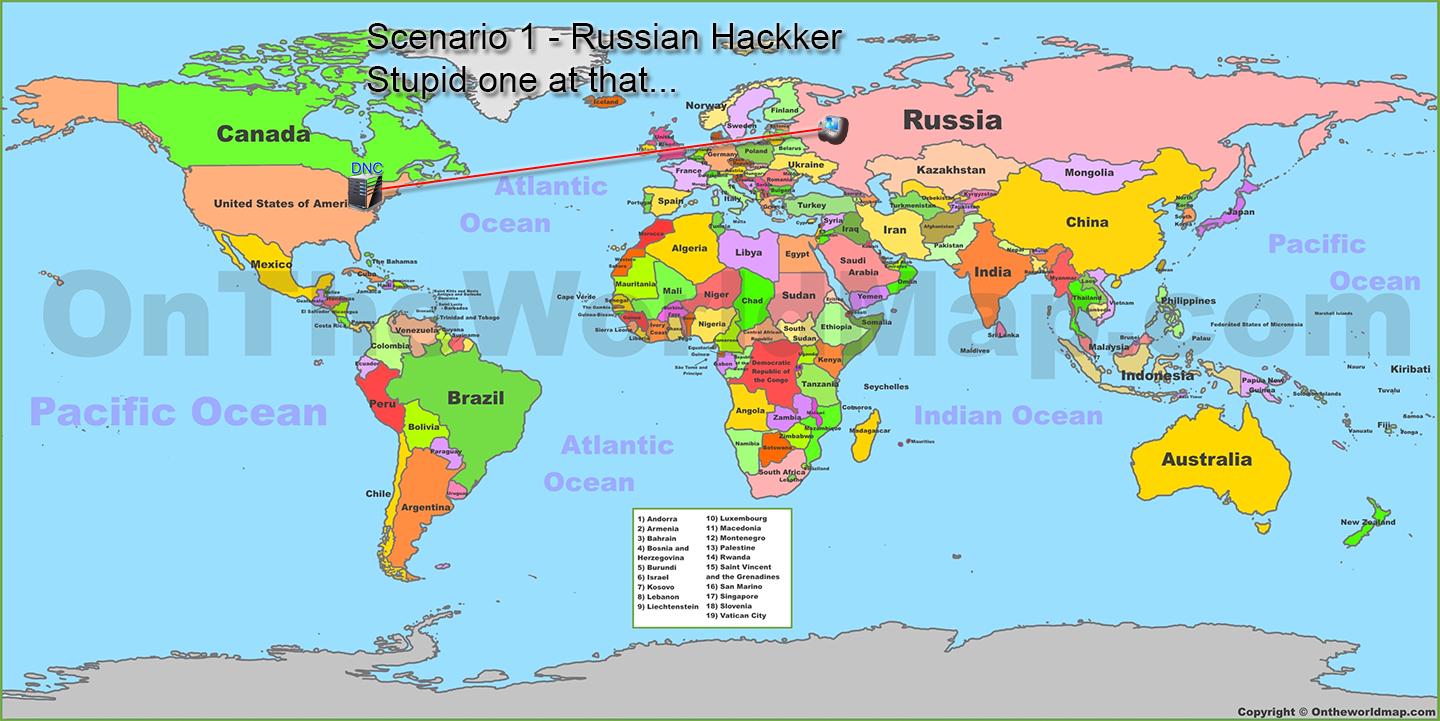
NOTE: sorry about the extra K in hacker. I didn't notice it until I'd already created and uploaded the image
Why is that?
Any hacker that knows much will not hack from their machine directly. They will jump to another machine in another country that they have previously hacked. From that machine they will jump to another, and then at some point when they feel there are enough hops between them and their target they will jump to their target.
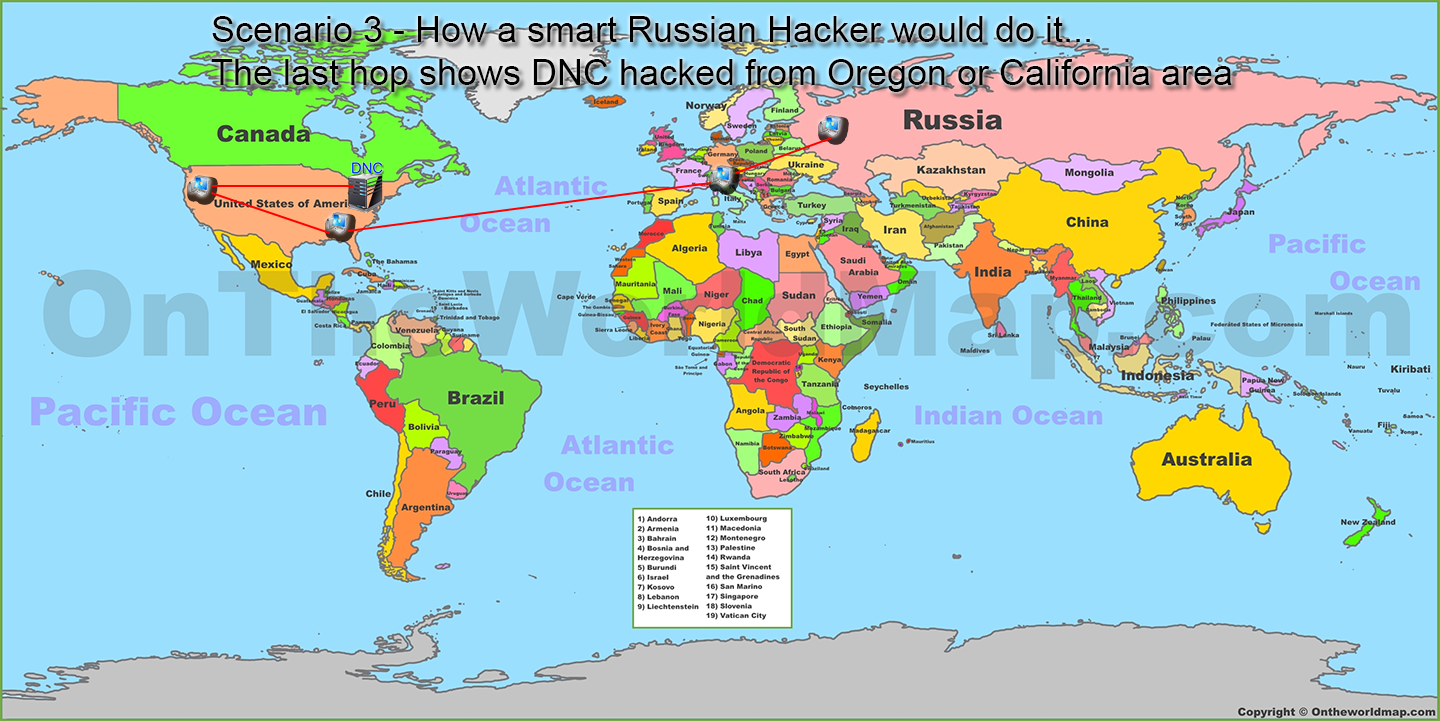
The fact of the matter is sitting right here in Colorado if I were a hacker I likely would have built up a collection of machines I had compromised all over the world by now.
How would I do this?
I'd write a very simple program (or use ones already out there, no programming required) to go through IP addresses one at a time looking for open ports. These ports signify what type of services I can find. I am particularly interested in ones that give me a login prompt. Once I have a login prompt I can send another program to keep trying to login with username and password combinations. Some of them will have security protocols that blacklist my IP after too many failed attempts, and I can simply move on. More on the BLACKLISTING an IP issue in a few minutes.
Some such as John Podesta's email would be the easiest in the world since his password was supposedly "password". There are also people who forget to change the default username and password that many devices ship with. It can be pretty easy to compromise these.
It is important to note that a compromised machine is not always about stealing your information. Compromised machines can become hops in that trail the hacker uses to conceal where they are actually at. They are also used for emailing spam email, and performing coordinated DDOS attacks.
So what this means is right now I could work on compromising a Russian average citizens internet connected computer. Odds are I would eventually manage to get one. I could then turn around and from there connect to other computers. To those computers I connect to it would look like I came from Russia.
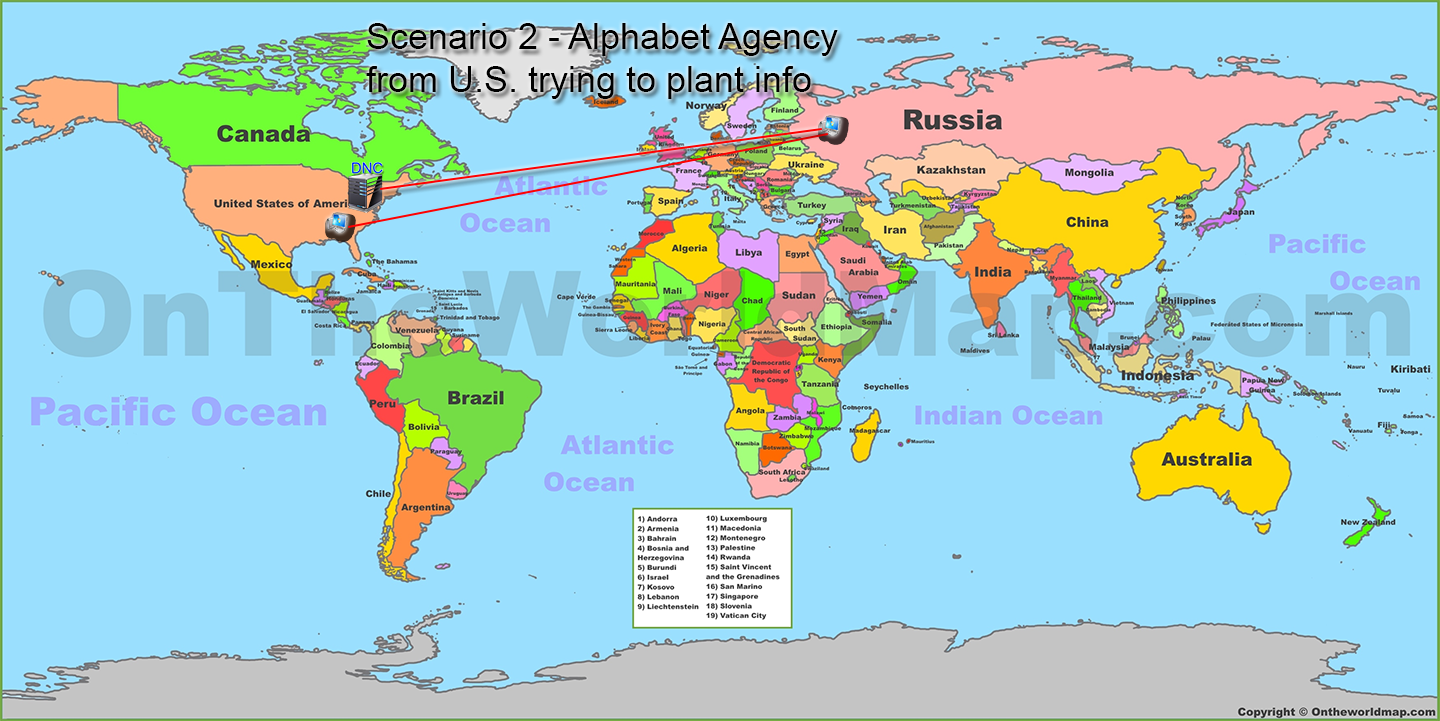
This means that the IP address alone is only proof that a HOP in the hacking chain was in a specified country. It is not proof the hacker actually came from that country.
Furthermore unless the WHOIS IP block comes back registered to a government office rather than a hosting service or ISP there is no proof it was done by a Government sanctioned actor.
The fact of the matter in Russia as I understand it is that they don't care who their citizens attempt to hack as long as they don't hack Russia. This means to the average citizen trying to poke around in other nations is fair game. I am of course basing this off of a documentary TV series called Cyberwar where I watched an episode specifically about Russian hackers and they went and interviewed and talked to them.
So when it comes to saying "Russian Hacker" that could be equivalent to calling a guy that works at McDonalds in the United States and then goes home at night and hacks a "United States Hacker". The IP address alone is not proof of State sanctioned hacking.
In other words, them stating they have definitive proof of hacking our elections is HIGHLY UNLIKELY to be definitive. They may have some Russian IPs but that is not definitive. In addition, if they don't release the proof then this essentially just become propaganda and justification for the hostile actions our nation is taking against Russia.
They are taking advantage of the fact most people have no clue how the internet actually works.
What I Have Seen
As a network engineer who deploys devices, servers, etc all over the United States and some in Canada, I see Hacking regularly. Furthermore, I work for a PBX company. PBX companies are really popular to try to hack so people can try to make international calls for free, or make VOIP based calls without being registered as to who they are.
I have several times deployed a new Adtran device and am in the process of locking it down and several times within less than an hour of hooking it to the internet I already have someone trying to log into it.
We typically lock our Adtrans down to only being able to be logged remotely in from very specific IP addresses. This can be a pain if a technician wants to access it from a hotel, yet in those cases we use this HOP technique I told you about intentionally. They use a VPN to connect to our data center, then connect to the adtran from a data center IP address.
The interesting stuff actually happens at the data center.
We will see hacks come in and probes against our servers. We will blacklist those IP addresses. Yet usually if the hacker knows their stuff they'll soon be coming in from another IP. In such cases we blacklist an entire block of IP addresses owned by whatever company/registrant they have obviously compromised.
I have actually NEVER seen a Russian IP address come into our systems. That doesn't mean some of them are not in fact in Russia. It simply means that last hop to us was not.
China has been the most common over the years. Yet lately I've seen Turkey, Palestine, Saudi Arabia, Vietnam, and the occasional sporadic European nation. Seeing those addresses though does not mean that is where those probes actually originated. They just as easily could have been a neighbor sitting down the street in the United States using machines in those countries as a hop.
So I ask you... how can we have definitive proof of Russian Hacking in our elections? If it is an IP address then that is incredibly SLOPPY when it comes to hacking, and does not seem to fit the Russian hackers unless they WANT to be caught. Seeing an IP address from Russia I'd think it more likely someone hopped through Russia because they wanted it to look like Russia. Since they won't release the actual evidence though all I can do is speculate.

Steem On!


