Some of you have read William Gibson's cyberpunk novels and love their romantic view of technology. As more and more network accessible technology gets accumulated, his sci-fi world is slowly becoming a reality.
Imagine this: a planet full of old technology, laying around everywhere - from old network cameras at people's homes to abandoned military communications software, flying on a decaying orbit around Earth. And we are now in the future, holding on to cheap, powerful hardware, which can interface with any of these devices.

Image property of its respective owner. Hack the planet, Cereal Killer!
Following Sputnik's launch in 1957, there have been over 6600 (official) satellites launched in space. Currently there are 3600 still orbiting our planet, with approximately a thousand still operational. [1]
So, a thousands toys to play with, right? Not necessarily.
Most satellites, having completed their original mission, undergo a standard shutdown protocol. Mission Control instructs the satellite to position itself on a decaying orbit, empty its batteries and shut down permanently, thus preventing any misuse of the satellite and also providing more available space for future deployment. Then everyone moves on to their next project, assured that their now defunct satellite will eventually burn up on reentry. Indeed, there is at least one satellite reentering our atmosphere weekly.

Image property of its respective owner.
The availability of cheap radio hardware combined with people's intrinsic desire to exploit hardware, proved that this is not often the case. The forceful depletion of batteries, during the shutdown process of some satellites, would cause them to fuse together, in effect leaving the power circuit closed. While in the shadow of the planet, these satellites would remain nonoperational, but as soon as their solar arrays get a glimpse of the Sun, they would boot up and start transmitting data.
This means that a number of the officially defunct satellites are, in fact, still accessible. "Accessible" being the proper way to describe their simple, non-encrypted protocols, which were state of the art, several decades ago.
Weather satellites. There are a number of them, which can be easily accessed. More commonly, people prefer the NOAA weather satellites, because of their high resolution, but there are even Soviet era satellites, which you can tap into (for that Gibson feeling, right?!).
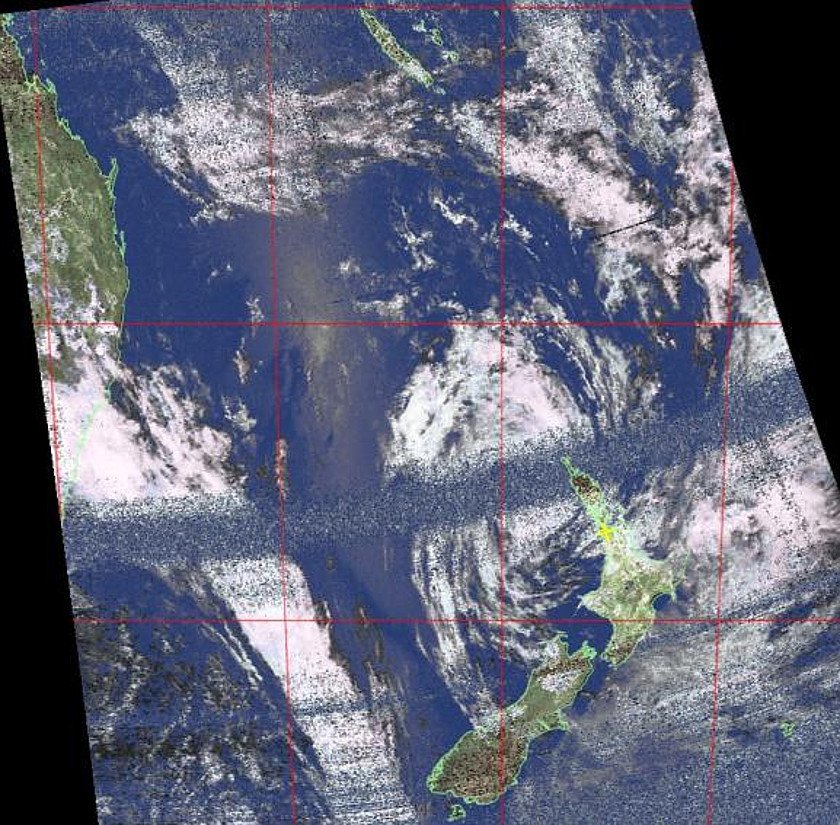
Image property of its respective owner. Image obtained from a NOAA satellite, using RTL-SDR.
You can find all that's required on the RTL-SDR website, but to summarize:
- An RTL-SDR dongle - basically the minimum hardware required for communication - the rest of the expensive hardware functionality has now been taken over by software. There is even better, more sensitive hardware out there, but at $20, you can't beat the price of this dongle. It's also very much useful for sniffing (and replaying!) communication of ubiquitous home appliances - wireless phones, car remotes, garage doors, etc. Yes, you can open your neighbor's garage door, if it's not the latest generation, featuring encryption, and drive him insane!
- Talking about software - SDRSharp.
- An antenna, for better reception.
Communication satellites. The Iridium network. A network of 66 satellites, spread out in 6 groups of 11 satellites, in effect covering the entire planet's surface. That's right, the huge phones with sticking antennas you see in movies, are connecting to the Iridium network.

Image property of its respective owner. A replica of an Iridium satellite.
Developed in 1987 and launched in 1998, it's no surprise that the technology used was already antiquated. In fact, most of the communication is sent in clear text. What is even more surprising is that the biggest client of the network, according to a WikiLeaks article, is the Pentagon. [2]
Relay satellites. Here we enter the danger zone. Globalstar satellites are simple relays - what you send on one end, arrives on the other. No actual need to hack the satellite, but tapping into the uplink means that you can alter the data being sent. This is exactly what a BlackHat participant succeeded in doing, by reverse engineering the protocol from the hardware given to customers to track their items. [3]
He hypothesized that this method can be used to alter the location of valuable items - vehicles, armored trucks and even planes, which the attacker may force to appear on a different location (or disappear) from their intended course. Patching this security hole may turn out to be impossible, as it probably requires physical access to the satellites.
Talking about disappearing planes reminds me of yet another functionality of the RTL-SDR. You can wreak havoc at your local airport control tower, by emulating non-existing aircraft on their radar. But I know you wouldn't.
Because that's not the Gibson way.

Image property of its respective owner. Crash and Burn, baby!
This is the first of a series of articles. Be sure to follow #dek-science for more!
Check out my latest articles:
- DEK Photography: Last Week's Photos in a Single Post!
- Poll: Steemit User Loyalty
- DEK Photography: Candle Light
I offer Professional Translation and Editing Services in exchange for Steem.
