
A number of smartphones today use a biometric security system in allowing users to scan their fingerprint in order to access their phone. And researchers suggest that this security method might not be as reliable as some people think.
The researchers at NYU Tandon School of Engineering sought to investigate the ease with which they could create a MasterPrint that would allow them access.
While it is widely believed that no two individuals have identical full fingerprints, researchers insist that there are partial similarities and those similarities are common enough that biometric security systems which rely on partial fingerprint data for access, might be vulnerable to being misused.
The vulnerability rests within the fingerprint-based authentication system which features small senors that store partial fingerprint data. And researchers say that the more partial fingerprint data that is stored on the Smartphone, the more vulnerable it is going to be to possibly getting matched up with this sort of MasterPrint.
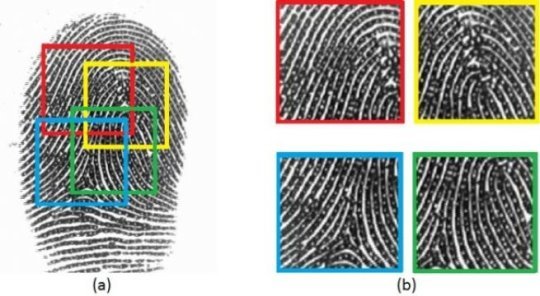
The researchers analyzed thousands of partial fingerprints and with the help of fingerprint verification software they were able to find an average of potential MasterPrints that might be able to be created. They suggest that there could be roughly 92 MasterPrints for every sample of about 800 prints.
They define a 'MasterPrint' as one that matches at least 4 percent of those in a random sample.
When it comes to using full-fingerprint data, there were fewer MasterPrints. With 800 full prints for example, they only found one possible MasterPrint. It is clear that there is more success in trying to match a partial than there would be in trying to match a full print.
The researchers built an algorithm that would create synthetic partial MasterPrints and they were able to successfully match between 26-65 percent of users.
This isn't the first time that security concerns have been pointed out with phones that use fingerprint data to allow someone to gain access. In some cases, individuals have allegedly been able to crack the fingerprint security by using simple items like dental mold and play-dough; along with repeated attempts at swiping.
The researchers of the recent study suggest that the resolution of senors needs to be greatly improved, to capture more detailed additional print features.

Pics:
Pixabay
NYU Tandon School of Engineering
phandroid
Sources:
https://www.sciencedaily.com/releases/2017/04/170411104603.htm
http://www.theverge.com/2016/5/2/11540962/iphone-samsung-fingerprint-duplicate-hack-security
https://www.theguardian.com/technology/2015/dec/27/2015-fingerprint-sensor-smartphone-security-biometrics-data#img-1
http://findbiometrics.com/acuity-biometric-smartphones-are-officially-mainstream-302125/
