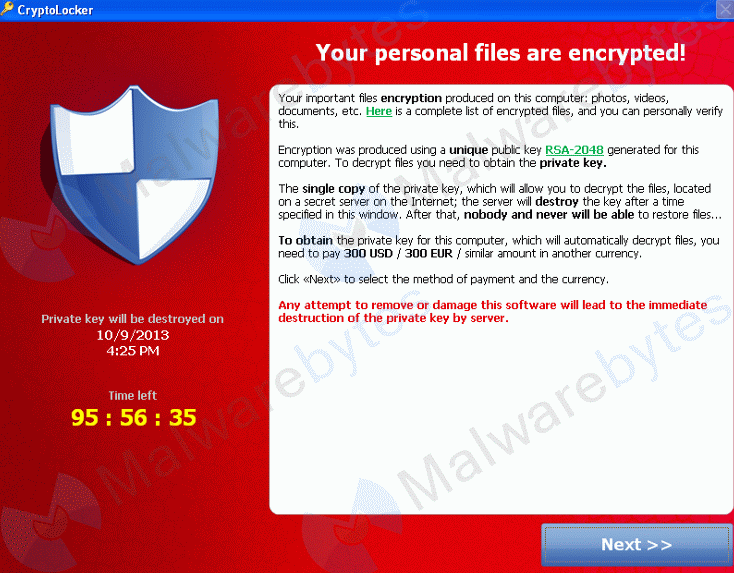
What is Locky Ransomware ?
The name of this ransomware is LOCKY. What is Locky ? it actually denotes one of the today’s prevalent ransomware families. It was discovered in the mid-February 2016. This file-encrypting epidemic proved to be sophisticated enough to fly under the radar of conventional anti-malware defense. However, Locky is one of the most preferred malicious software used by hackers.
Who Discovered ?
Bart Blaze, a very well known reputed security researcher first discovered this type of ransomware attack which is being conducted via Facebook Messenger. Later, Peter Kurse, another security researcher with extensive experience in investigating cyber-crimes confirmed the news to reporters.
Bart Blaze wrote in his personal blog :
“As always, be wary when someone sends you just an ‘image’ – especially when it is not how he or she would usually behave”.
And Facebook has released the following statement in response to the discovery:
“We maintain a number of automated systems to help stop harmful links and files from appearing on Facebook, and we are already blocking these ones from our platform. In our investigation, we determined that these were not, in fact, installing Locky malware—rather, they were associated with Chrome extensions. We have reported the bad browser extensions to the appropriate parties”.

How does it spread ?
To spread Locky ransomware hackers are using a downloader software called Nemucod. This downloader is being used by hackers to help the ransomware bypass Facebook security by pretending to be a .svg image file. Hackers is now delivering this downloader software Nemucod through Facebook Messenger.
What is .svg image file ? How hackers spread ransomware through it ? SVG extension file is scalable vector graphics file. It’s based on XML (Extensible Markup Language). So, it’s very easy to implement a set of codes of any harmful programs in it.
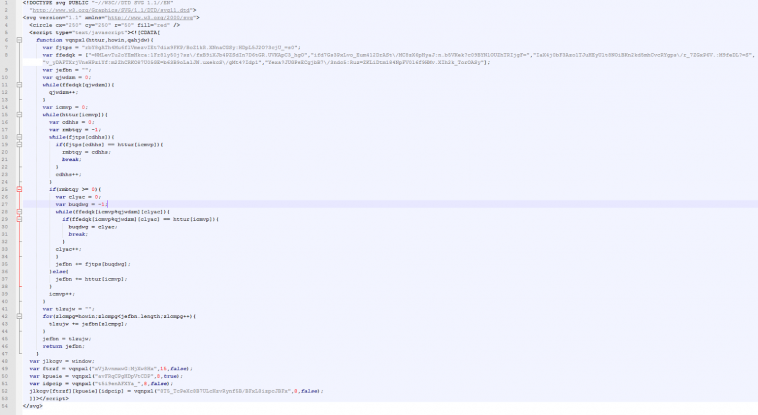
However, in this case hackers has embedded JavaScript. When you access this infected vector image file (SVG) then this java-script directs you to a site that seems to be YouTube’s landing page. But, actually it is not real Youtube’s homepage. It’s a clone site developed by hackers. If you look in the url then you will find that it’s 100% different.
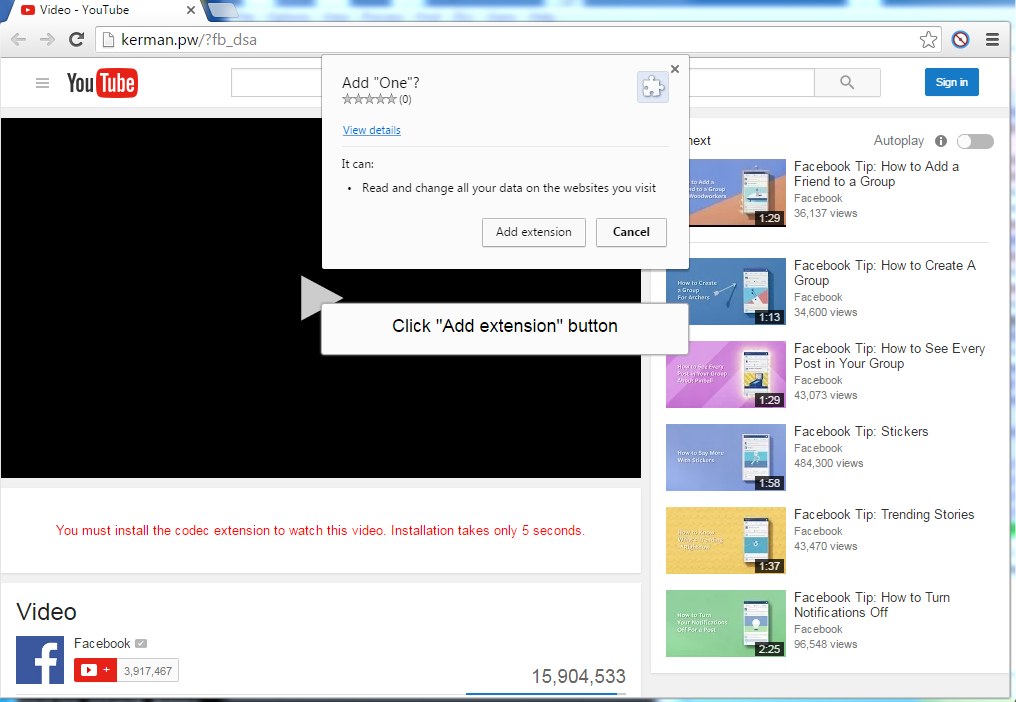
However, after loading the fishing site you’ll be requested to download & install a codec so that the desired video could be played. This codec is presented in Chrome extension. If you install this codec chrome extension then the attack shall be distributed to other friends of you via Facebook Messenger. And at the same time this chrome extension will install Nemucod downloader, and instantly Locky will be installed into your system via Nemucod downloader. After that your all personal files on PC will be encrypted (locked) by Locky & it’ll demand some money via Bitcoin to decrypt them.
How to keep safe yourself from Locky ransomware infections?
To protect yourself from Locky take some preventive precautions to avoid any trouble in the future. Following these rules strictly may decrease the chances of hijacking by Locky -
1. Do not connect your pc, laptop, tablet etc. to a public WiFi hot spot.
2. Do not open any attachments in email or chatbox from unknown or, suspicious senders.
3. Do not click any links in emails or chats from unknown senders.
4. Do not download any files attached in email or chat from unknown or, suspicious senders.
5. Try to avoid visiting malicious sites.
6. Do not download or, update software/apps from a third-party website, or store.
7. Do not use any out-dated or, pirated software.
8. Install WOT (web of trust) extension, and visit only reputed websites shows by WOT.
9. Keep your antivirus & windows up to date always.
10. You may use Kaspersky anti-ransomware tool, or, Bitdefender anti-ransomware tool for extra security.
11. Disable SMB v1, SMB v2, SMB v3 on windows via registry editing. How to disable it ? Read below.
12. Periodically set restore point. After attack you may able to use System Restore to get back to a known-clean state.13. Most Important : Always keep offline backup your data, or, do cloud backups.
references :
http://thehackernews.com/2016/11/facebook-locky-ransomware.html
http://securityaffairs.co/wordpress/53650/malware/svg-images-locky.html
https://www.hackread.com/facebook-messenger-images-drop-locky-ransomware/
https://arstechnica.com/security/2016/11/locky-ransomware-decoy-image-files-boobytrap-facebook-linkedin/
http://www.csoonline.com/article/3143173/security/malicious-images-on-facebook-lead-to-locky-ransomware.html
follow me on steemit  AND resteem it
AND resteem it 






>>Thanks to @elyaque for designing my badges :)<<
MY STATS
REPUTATION SCORE : 68.5 | TOTAL FOLLOWERS : 507
TOTAL BLOG POSTS : 513 | TOTAL LIKES : 32394
TOTAL EARNINGS : $4294.75
