It never ceases to amaze me how intelligence agency narratives never fail to trip over their own shoelaces.
Hi Steemians!
As my readers know, I tend to write monolithic pieces (understatement) and I am presently three months into researching a major piece of writing that is still a ways off yet. The last thing I intended to do was divert my attention to debunking a hot topic in the current news cycle instead.
But seeing this THE-DUTCH-FILMED-THE-RUSSIANS-HACKING-OUR-ELECTION nonsense all over Twitter, I couldn't help but stop what I was doing and throw a post together to show you guys just how transparently ridiculous the "huge story" is to anyone with the slightest technical know-how, before more innocent people are fooled by the fake news.
So here we go - my first ever time writing an article just for Steemit. I hope you enjoy it, and please pass it on :)
Love,
Suzie
10 Reasons The Dutch-Russia Hacking Story Is Fake News
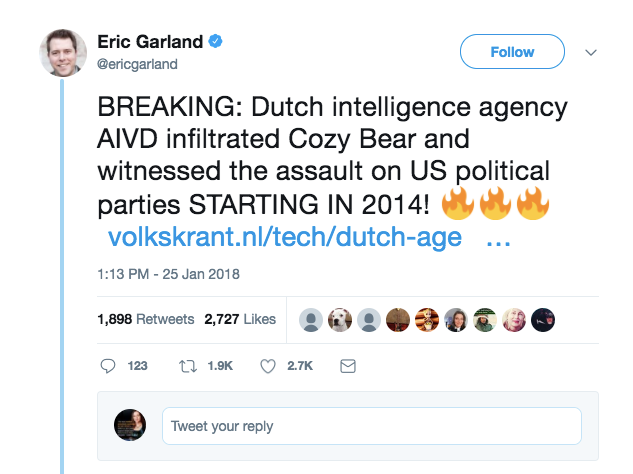
It was breathlessly announced today by that pillar of independent news sources, US intelligence contractor Eric Garland, that the Dutch possess incontrovertible proof that Russia indeed hacked the US election.
Citing an article in a Dutch publication, Garland let fly with a series of narrative tweets with screenshots of a translation of the article, to make his case.
His original tweet had already clocked over 1800 retweets by the time I happened across it.
A quick Twitter search on "Dutch Russia election" returned hundreds of results, showing that indeed the story was being seeded across social media and replicated thousands of times by both sock puppets and well-meaning believers alike.
By the time I started writing this response, none other than MotherJones had published a craft-less regurgitation that barely scratched a few hundred words, citing only the Dutch article as the basis for the claims.
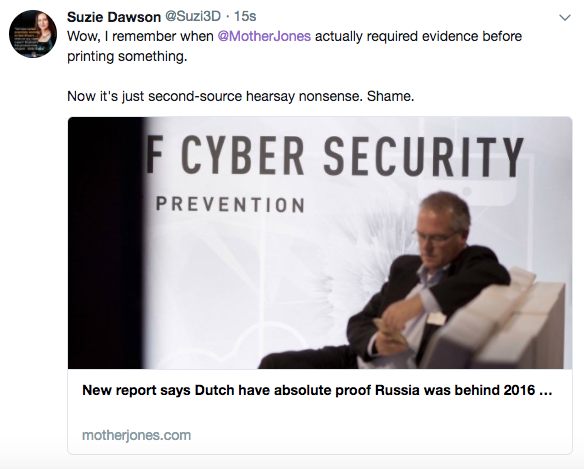
I am still nostalgic for the pre-Clara Jeffery days when MotherJones could be relied on for cutting edge investigative journalism that didn't simply push intelligence community talking points and false flags, however they appear to be long gone.
But back to the specifics of this particular con-job, let's dissect the story itself, and see why it is completely ludicrous for anyone to take what is being claimed at face value.
1. The Russian Hackers were hacking from a university building when they were identified by the Dutch.
The Dutch article states:
"*It is the summer of 2014. A hacker from the Dutch intelligence agency AIVD has penetrated the computer network of a university building next to the Red Square in Moscow, oblivious to the implications. But one year later, from the AIVD headquarters in Zoetermeer, he and his colleagues are witness to Russian hackers launching an attack on the Democratic Party in the United States. The AIVD hackers had not infiltrated just any building; they were in the computer network of the infamous Russian hacker group Cozy Bear. And unbeknownst to the Russians, they could see everything*."
It never ceases to amaze me how intelligence agency narratives never fail to trip over their own shoelaces. How soon they forget, that one of their biggest attempts to discredit NSA whistleblower Edward Snowden, was over revelations he made about the USA hacking a major Chinese university, that were published by the South China Morning Post in June, 2013.
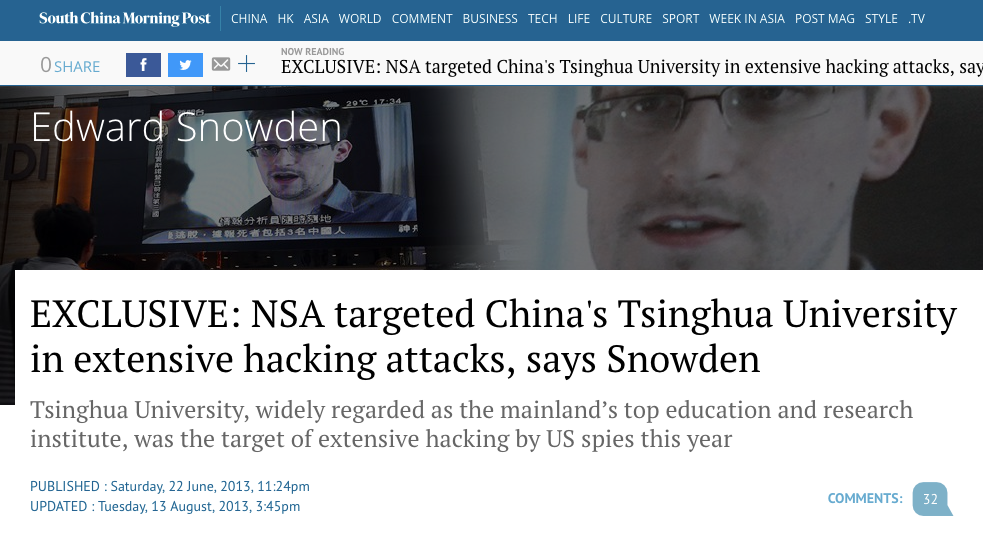
Yes, that's right, one of the first major scoops of the Snowden files was that the NSA was targeting the computer networks of major universities in enemy nations.
The US was so up in arms about the revelation that they tried to claim it was proof that Snowden was aiding and abetting China by releasing that information. I addressed this in my 2015 article titled "Debunking The Dinosaurs; Dismantling Snowden's Detractors".
Another US deep state apologist, Michael Cohen, had demanded to know why Snowden "leaked operational info to [a] Chinese newspaper" and suggested that Snowden may have directly leaked them docs that might have ended up in the hands of the Chinese government (an abject falsehood).
Quoting my article:
As with much of Cohen’s commentary, he fails to back up his accusations with references so this point has been particularly difficult to research. Many hours of reading South China Morning Post’s Snowden archive later, and the only ‘operational info’ I’ve been able to establish that Snowden discussed with them, was wholesale spying on Chinese university students and on the SMS messages of the general population. Unless he is referring to the mention of mass surveillance being undertaken at-cable, which is a worldwide phenomenon that has been reported consistently around the globe, in many regions..
Indeed, the SCMP revelations fit perfectly with the ongoing theme of Snowden’s leaks; where the public of various countries (most of the countries in the world in fact) are spied on by the U.S. in a wholesale fashion, without warrants or individual suspicion to justify the targeting.
Snowden’s releases have not been about military versus military – but military versus civilians: mass surveillance. To expect him to exclude Chinese civilians, or Russian civilians, or any other, just because the names of those countries are incendiary to the U.S. political mainstream, would be to expect him to discriminate on the basis of nationality, the way his government does. Yet Snowden has very much proved to be a global citizen, and clearly does not adhere to the inherently unjust principle of ‘American exceptionalism’. This does not detract from, but enhances his efficacy in the eyes of the global public.
So to put any credence in this Dutch-Russia-hacking story, you would have to believe that a year after the above Snowden revelations, the Russian government decided to run an elite hacking operation to compromise a foreign election out of a major university in the centre of Moscow, when it was already an established fact that the NSA targeted university networks.
Ridiculous.
2. The Dutch repeatedly notified the US about it.
The Dutch article continues:
"*That's how the AIVD becomes witness to the Russian hackers harassing and penetrating the leaders of the Democratic Party, transferring thousands of emails and documents. It won't be the last time they alert their American counterparts. And yet, it will be months before the United States realise what this warning means: that with this hacking the Russians have interfered with the American elections. And the AIVD hackers see it all happen*."
The idea that the US wasn't already monitoring the network traffic of a major Russian university smack in the middle of the capital Moscow, is unlikely enough but the idea that they didn't work out that Russia stealing emails and files from political leaders could amount to tampering in the US political process is even more far-fetched.
Them ignoring repeated warnings by an ally in and of itself would be entirely in character with their general ineptitude however Russia has been at the top tier of their target list in particular since Snowden was given asylum if not already prior. Such messages would not have been neglected given their level of interest in any activity of Russian origin post 2013.
This notion of the Dutch repeatedly alerting the Americans and the Americans doing nothing appears to be an attempt to explain the timeline of the leaks without overtly addressing it. The DNC emails span January 2015 until May 25th 2016. Therefore, to sell this nonsense story, they have to pretend the US ignored Dutch warnings, in order to explain how data could be allowed to be exfiltrated over such a long period of time.
3. Mueller's prime objective isn't Trump collusion, it's Russian hacking
Eric Garland's Twitter diatribe jumps from the above suppositions straight into the Mueller probe. His second screenshot of the article's translation begins: "After Trump's election in May 2017, this investigation was taken over by special prosecutor Robert Mueller. It also aims to uncover contacts between Trump's presidential campaign and the Russian government, but the prime objective is bringing to light the Russian interference with the elections."
Just as the news cycle has finally gotten to grips with the fact that even FBI agents working on the Mueller probe who hated Trump thought that there probably wasn't any evidence of Trump colluding with Russia, we are now to believe that the notion of Trump collusion, which was promised would bring down the President, was actually only ever secondary to establishing that Russian hacking occurred at all.
We are supposed to conveniently forget that the very first stipulation in the official terms for Mueller's probe was to establish if there were "any links and/or coordination between the Russian government and individuals associated with the campaign of President Donald Trump".
It's a classic bait and switch. Having failed at the 'collusion' narrative, they now wish us to believe it was always about Russian hacking, mmkay? Except that if it were, the FBI would have examined the DNC's servers immediately, which it famously did not.
Depending on who you believe, either the FBI didn't ask to examine the DNC servers, or the DNC didn't let the FBI examine the servers, or the DNC hired Crowdstrike to do it or the FBI hired Crowdstrike to do it:
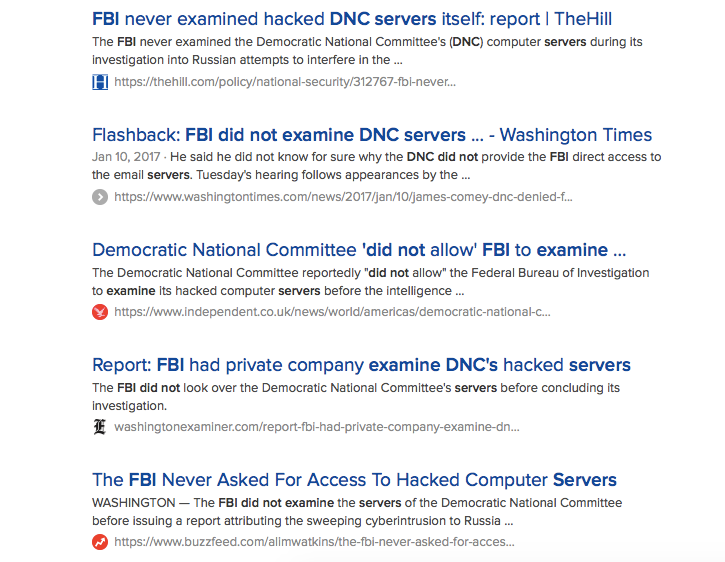
The utter confusion in the headlines of the mainstream media is indicative of the giant clusterfuck this Russian hacking story has been all along. No wonder people are bewildered by it all and so easily misled.
4. Anonymous sources, amnesiac author.
Glenn Greenwald has brilliantly demonstrated on more occasions than I can count, why claims such as those made in the Dutch story should never be taken at face value, especially when they come from anonymous sources at pivotal moments in time and just happen to serve the interests of the intelligence agencies.
As if the total lack of sourcing doesn't make this example dubious enough, the author of the article appears to be an amnesiac. Having claimed that repeated messages from the Dutch had been ignored by the Americans, the article soon does an about face:
"*Three American intelligence services state with 'high confidence' that the Kremlin was behind the attack on the Democratic Party. That certainty, sources say, is derived from the AIVD hackers having had access to the office-like space in the centre of Moscow for years. This is so exceptional that the directors of the foremost US intelligence services are all too happy to receive the Dutchmen, because not only do they provide technical evidence for the attack on the Democratic Party, it becomes apparent that they know a lot more*."
Perhaps this is a slip; one of the most notable architectural flaws of the article is its inability to articulate and stick to a cohesive timeline. But the further we get into it, the more and more inaccurate, disjointed and farfetched it becomes. Eventually it devolves into outright, easily disprovable disinformation.
5. Techno-babble
It's always a sure sign of B.S. when an article fails to competently describe the basics of the technologies and tactics they are claiming have been utilised.
The article states:
"*It's somewhat of a 'fluke' that the AIVD hackers were able to acquire such useful information in 2014. The team uses CNA, which stands for Computer Network Attack. These hackers are permitted to perform offensive operations: to penetrate and attack hostile networks*."
As SchnierBlog aptly describes, a Computer Network Attack is a debilitating act of sabotage undertaken to damage or destroy an adversary's network or hardware. A famous example of this would be the Stuxnet virus used to cripple Iran's centrifuges. Computer Network Exploitation, however, such as that which Edward Snowden undertook on behalf of the NSA, is where a network or machine is exploited for the purpose of spying on.
In order for the Dutch to have lurked "for years" as earlier claimed, they would have had to employ the latter, rather than the former approach. The article has misrepresented what they actually did, either because the source for their article is somewhat clueless, or the author is.
But that's not all.
The article says:
"*[The Dutch] team is part of the Joint SIGINT Cyber Unit, a collaborative unit of the AIVD and the Dutch Military Intelligence and Security Service MIVD, of about 300 people. It is unknown exactly what information the hackers acquire about the Russians, but it is clear that it contains a clue as to the whereabouts of one of the most well-known hacker groups in the world: Cozy Bear, also referred to as APT29*."
For those who don't know me, after spending years writing about Snowden, WikiLeaks, Greenwald and associated topics, I finally decided to study all of the Snowden documents myself, eventually teaming up with Elizabeth Lea Vos from Disobedient Media and launching the #DecipherYou series to see what the files contain that no one had previously reported on. The answer was, a lot.
(Studying the files has completely changed my view of the leaks, the intelligence agencies, the United Nations, and in fact the entire world around us and how it really works behind the facade of politics and media. But it has also made me quite adept at being able to "read between the lies" as one of my friends would say.)
So when I see a new term I don't recognise, such as "Joint SIGINT Cyber Unit" my reflex action is to go to EdwardSnowden.com and do a document search on the term. I didn't find anything. So I typed in "Netherlands" instead and read all the returned results. Bingo.
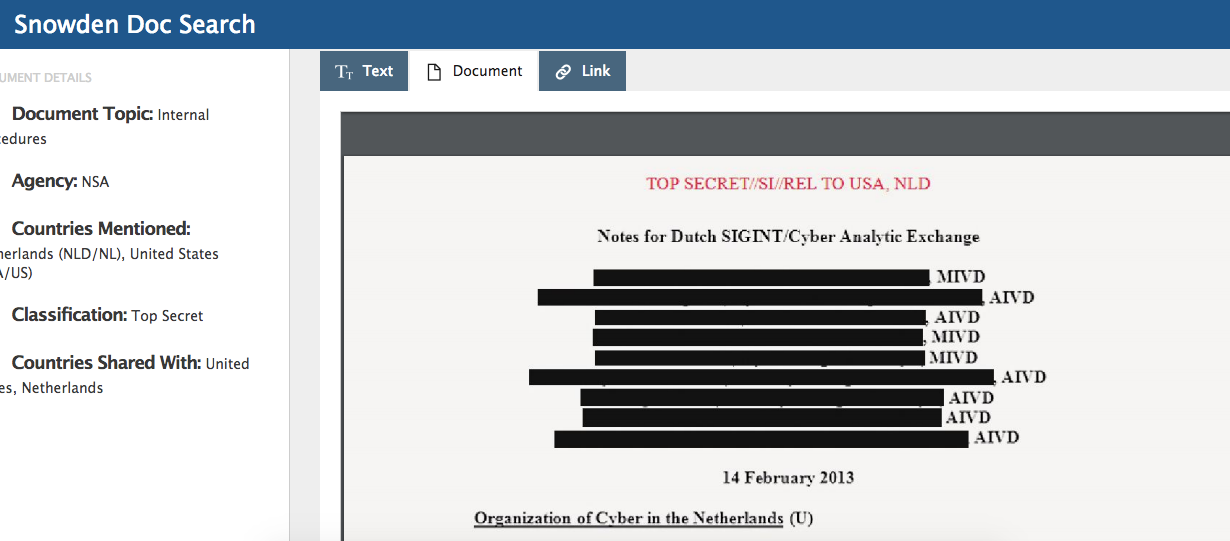
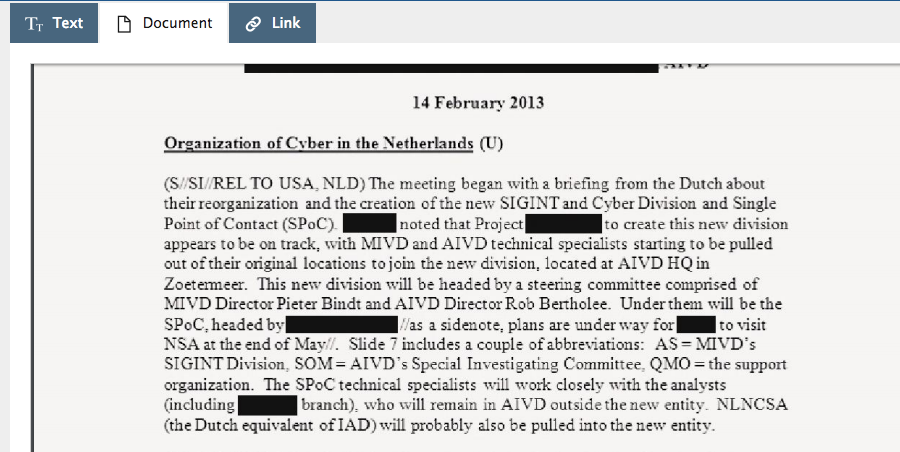
Significance:
a) A full year prior to supposedly penetrating the Russian network, the Dutch were creating a "Single Point of Contact" for all their domestic and military cyber agencies
b) They were already engaged in Cyberanalytic exchanges with the NSA
c) They had site visits at NSA headquarters
d) They were not yet mass surveilling their own population through cable-taps (where the entire net traffic of the country is bulk collected, a practice that has been pioneered in the West and turned against their own populations and the data funnelled back to NSA through 'partnership' agreements) but had plans to do so, which would have been of extreme interest to NSA, whose goal is to literally collect the entire world's internet traffic wholesale (known as the "collect it all" strategy)
e) The document lists no less than six direct NSA contacts at AIVD as of 2013, probably more (due to the redactions it is unclear which names are duplicated or not later in the document)
f) The document indicates several reasons to believe that the capabilities of the NSA significantly outstrip that of the Dutch
The above points indicate a level of closeness and accessibility that is in stark contrast to that described by the Dutch-Russia-hacking article, which attempts to depict the Dutch hacking team as independent and at arm's length from NSA, rather than the reality: AIVD is a full-fledged NSA second-tier Third Party partner, who divulges every detail of its organisational structure, capabilities, networks, systems and personnel to the NSA in return for advanced analytical capabilities, enhancements and technological support.
6. It is all based on alleged evidence that we will never get to see
Just as with the infamous, debunked Steele dossier, we are once again sold lies on the promise of the existence of video footage that we will never see.
But we have to believe it exists. Just like we have to take an anonymous source's word for it, even though they won't provide any of the evidence they claim to have seen.
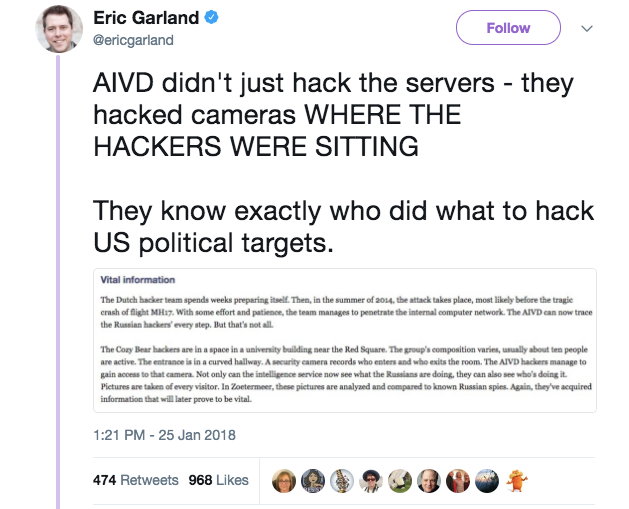
Contrary to the erroneous claim in the above tweet of the hackers being filmed where they were sitting, caught in the act, which had led me in turn to respond with this, the article doesn't actually state that the hackers were filmed where they were sitting, but instead that they were filmed passing in and out of a "curved hallway".
While Garland boisterously expounds "They know exactly who did what.." and the article states that the supposed images from the camera were "analyzed and compared to known Russian spies", in a country of 145 million people, they simply do not. Which is why the article tries to clean this discrepancy up with a promise of future value: "Again, they've acquired information that will later prove to be vital."
7. The Dog Whistle
This is the screenshot from Garland's tweet:
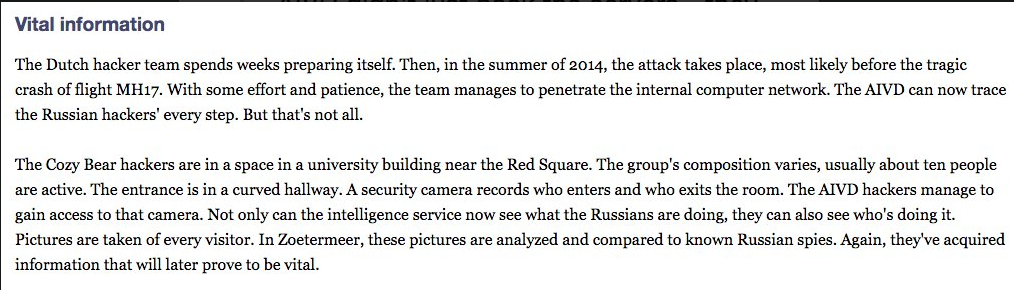
The strange reference to MH17 sticks out like a sore thumb. Nowhere else is there any mention of the incident whatsoever, or any qualifier for the out-of-the-blue assertion that the hack must have occurred before MH17 was downed.
This singular, bizarre reference screams dog whistle.
By invoking this previous bone of Dutch-Russia contention, they are surreptitiously transmitting to both their allies and their competitors, the rationale for the Dutch involvement in this media psy-op. It is a calling card.
8. Star Wars and Further Timeline Violations
After a grand, epic battle between the foes, the good guys were victorious. Or so goes the fairy tale being painted for us by the Dutch.
Despite having tried to explain away the years of US inaction by them having missed messages from the Dutch, somehow the NSA are back in the picture in 2014 fighting a real-time cyberwar alongside the Dutch against these nefarious Russian hackers.
There are so many lies in this one screenshot it is almost worth an article in and of itself:
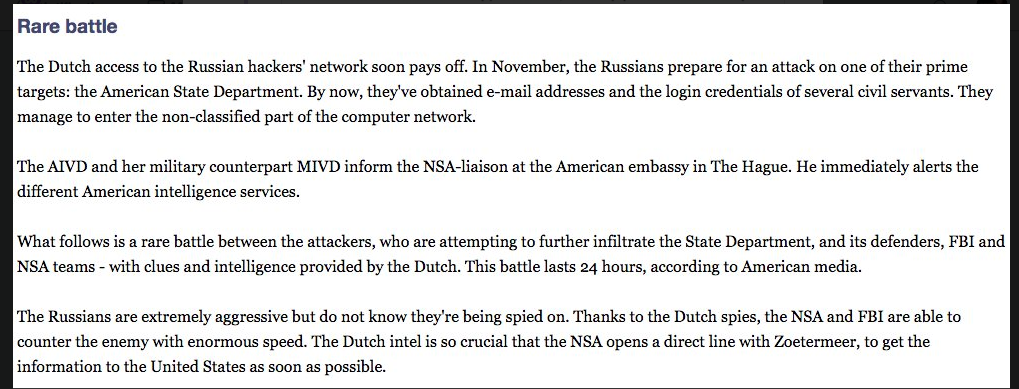
Let's take the four feel-good paragraphs one by one. Firstly, they claim that the Russian hackers only ever got into "the non-classified part of the network." In other words, nothing to fear, dear public, our secrets were safe all along.
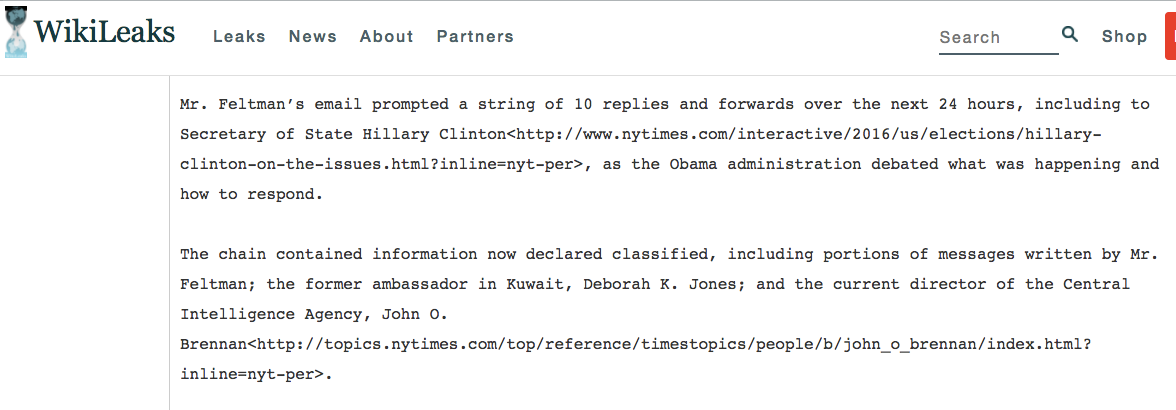
Except meanwhile back in reality, the USA is so lax with its data handling practices that even communications between Hillary Clinton when Secretary of State and the DIRECTOR OF THE CIA were caught up in forwarded and re-fowarded email chains on unclassified servers. How do I know this? Hilariously, from the DNC Leaks!
The second paragraph assures us of the timely relaying of messages from the Dutch to the Americans, and the Americans leaping to action stations to notify their counterparts and neutralise the foreign threat.
The third paragraph oddly cites "American media" as the source for the information about this "rare battle" between the agencies, despite the fact that this is supposed to be a giddy exclusive of new information provided by the all-knowing Dutch source.
The fourth paragraph is difficult not to splutter one's coffee over. The Russians are oblivious to the counteraction - the FBI, NSA and the "crucial" Dutch move with "enormous speed". The Dutch and the Americans established a "direct line... to get the information to the United States as soon as possible", according to the article, even though in actuality the NSA has a multitude of direct real-time communications mechanisms with all of its partners, 24/7. So yup, they made a conference call. Gripping stuff.
Could it get any more overblown and dramatic? It's as good as reality TV, folks. Starring Louise Mensch.
But they aren't done yet. First we must literally extoll the historical alliances of global warfare, in order to drum up sufficient levels of emotion to render the cognitive abilities of the reader moot.
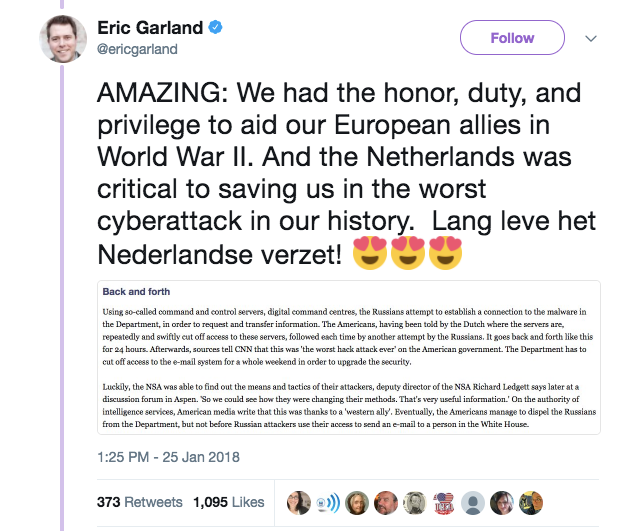
Funnily enough, you'd think the "worst cyberattack in history" would have been when the Russians attacked the US energy grid. Except, whoops, it turns out that never happened.
Or maybe it was that time they hacked the German elections. Except, whoops, that never happened either.
How many Russian hacks have to turn out to have not happened before we stop listening to the idiots who keep telling us they did?
9. They lie about the methods of both attack and defence
The situation was so dire, the article claims, that "the Department had to cut off access to the e-mail system for a whole weekend in order to upgrade the security."
OK, let's get something straight. We know from the Snowden documents that the War on Terror was literally fought on Dell workstations with Oracle Databases and Microsoft Exchange Server. The Snowden document discussed earlier, about the Netherlands Cryptanalytic Partnership with the NSA? Read the small print and you see this:
"*80 percent of NSA tools used to find malware are commercial, while 100 percent of Dutch tools are*."
The idea that upgrading the State Department mail server would keep out a team of supposed elite Russian hackers acting on the order of or with the resources of a President is laughable.
But we knew this in June 2017, when the last ridiculous NSA report came out. Elite hackers simply don't behave the way that these foolish media psy-ops keep trying to portray them as.
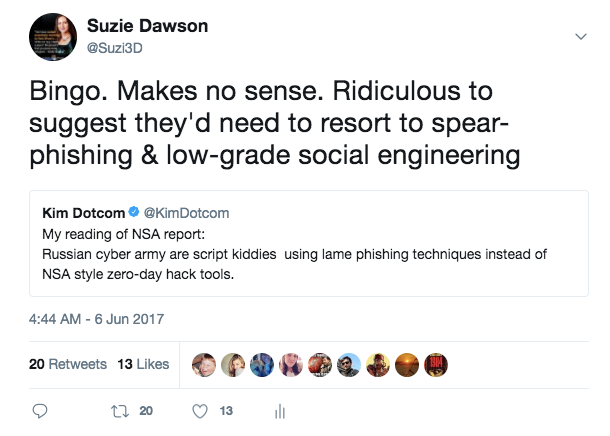
But then, the NSA doesn't want us to know how elite hackers really behave. The only people giving us information about that have been Edward Snowden (TAO, JTRIG) and WikiLeaks (Vault 7, Vault 8). Both of whom, the NSA subsequently despise with a passion.
10. They avoid the obvious credible narrative like the plague
The only credible narrative in this whole shit-show is that every intelligence agency tries to undermine every other intelligence agency, whenever or however they can, during elections and not during them. The U.S., for example, deployed teams of spies from partner countries to infiltrate all the political parties in the French election. They literally wielded teams of human intelligence assets, on the ground in France, to their own ends. This is established fact, with ACTUAL EVIDENCE: the dispatch orders from the CIA.
That is what evidence of election meddling looks like, and it wasn't even against a supposed adversary - it was against an ally, and they used other allies to do it. But in this backwards, Orwellian world, we aren't allowed to tell the true story.
Instead we are spoon-fed nonsense like this Dutch tripe by comfortable pseudo-journalists and wealthy spin doctors dressed up as "security experts", while the few remaining truth tellers are screaming warnings to their dying breaths.
Then of course, there's these small (sarcasm) factors, supplied to me by a conscientious reader:
Changes the picture just a little, huh?
In Conclusion
The saddest part of all is that I could change the title of this piece to "20 Reasons The Dutch-Russia Hacking Story Is Fake News" and continue with ease. There is another three screens in Garland's original diatribe, all chock full of Christopher Steele/GCHQ-grade nonsense and each one is even more fanciful than the last.
His story would have been as credible if his first tweet started with "Once upon a time" and his last tweet finished with "and they all lived happily ever after."
So instead, I'm going to do something different. I'm going to finish by telling you some truths about these agencies, and about the world and how it really works. Truths from the Snowden documents, that you haven't heard about yet, because the mainstream media would probably be fired if they reported on findings from #DecipherYou.
So here's my top 10 findings from that series, in no particular order:
- Internal NSA resistance to 9/11 Commission and Senate Intelligence Committees oversight
- All Osama bin Laden had to do to be undetectable by the NSA was use .PDF
- "It takes a village to spy on the UN" - State Department, NSA and CIA to name a few
- The US considers the UN to be an arm of US foreign policy
- NSA literally planning a system of global control - want their spying network to cover the entire globe
- Proof that NSA started handing over entire databases of data to their "customers" - not just reports
- Internally, NSA claimed credit for both Bush and Powell's bullshit Iraq War speeches at the UN
- NSA wants to take its battlefield targeting alert system used to kill people in Iraq and in war zones, and implement it globally
- NSA has access to and control over the satellites/hardware of partner nations
- It is a total myth that the CIA and NSA are in competition with each other, or that Snowden didn't leak info about the CIA/DIA etc. The documents paint the true picture.
Now, given all the above. The weight of which sits on my shoulders daily.
Tell me again how the biggest story in the world is whether Russia hacked the Democrats.
By Suzie Dawson
Twitter: @Suzi3D
Official Website: Suzi3d.com

Journalists who write truth pay a high price to do so. If you respect and value this work, please consider supporting Suzie’s efforts via credit card or Bitcoin donation at this link. Thank you!
Read, Upvote and Share Suzie's Other Steemit Posts!
- Suzie's Introduction On Steemit
- Glenn Greenwald and the Irrelevance of Electoral Politics
- FVEY vs Kim Dotcom
- Understanding World War III
- Just As Intended: The U.S. Election Is Tearing Us To Shreds
- Someone Is Lying To Seth Rich's Family About Kim Dotcom
- Diary of a Person of Interest - Full Documentary on dTube by NSA/FBI target Suzie Dawson
- The Agenda To Destabilize Europe
- Finding hidden gems in the Snowden files: DecipherYou Episode 1
- Finding hidden gems in the Snowden files: DecipherYou Episode 2
- Finding hidden gems in the Snowden files: DecipherYou Episode 3
- Finding hidden gems in the Snowden files: Decipher You Episode 4
- Finding hidden gems in the Snowden files: Decipher You Episode 5
- In Plain Sight: Why WikiLeaks Is Clearly Not In Bed With Russia
