For those who don't know, Cryptography is the study and procedure of the techniques used to establish a secure communication between two parties by hiding the data from third party.
Passwords are kind of an applicaiton of Cryptography to secure sensitive data and information.
I won't dig deeper into the definition and introduction, let's come to the point.
How passwords are stored then?
When you sign up for a website, your password is stored in its database. What could be the possible way of storing passwords of all the users?
One way is to store, just the plain-text, like this:
| Usernames | Passwords |
|---|---|
| Alice | abcd123 |
| Bob | spookyspy |
If a hacker gets hold of this database, then all the passwords are compromised too.
That's why we always use hash tables for storing passwords.
What are Hash tables?
Hash tables are a data structure widely used in computer programming.
There are hash functions which are applied on the usernames or on the passwords to convert them into another set of characters which are completely non-decipherable for hackers.
Now let's store Alice and Bob's password using a hash function.
Hash function: I am taking the ASCII value of each character in the password and multiplying it with the position of that character and then adding all the values. Then take modulo of the result with any random prime number, let's say 89.
= 1892 mod 89
= 23.
Similary for other password:
= 5167 mod 89
= 5.
Now the passwords are hashed and can be stored like this:
| Usernames | Passwords |
|---|---|
| Alice | 23 |
| Bob | 5 |
If a hacker gets hold of this database and he knows the hash function, he still won't be able to find the actual password because hashing works one way only. Hacker can see the password 23 and 5 and if he applies hash function to these then he will get an entirely different result.
How the actual user gets his password verified, when he tries to login?
Alice will enter abcd123 and database has stored 23 for her. But they don't match.
What happens here is that, every attempted password along with the username "Alice" is hashed first with the above used hashed function and if the result matches the password(which is already hashed with the same hash function) stored in database, then only the user is allowed to login.
There is one other way; We can hash usernames with the same hashed function and get different indices for every user to store their password.
Alice = (65x1)+(108x2)+(105X3)+(99x4)+(101x5)
= 1497 mod 89
= 73
Bob = (66x1)+(111x2)+(98x3)
= 582 mod 89
= 48
| Usernames | Passwords |
|---|---|
| 0 | |
| 1 | |
| .. | |
| 48 | spookyspy |
| .. | |
| 73 | abcd123 |
If a hacker get holds of this type of database then he won't know who is 48 and who is 73. Knowing hash function won't help much until he also knows which username's password he wants.
To make it more secure, passwords should be hashed too like discussed before this.
Every secure internet service or website save your passwords with this technique.
But hackers are also in the game with us. They use rainbow tables (precomputed tables to reverse the hash funcitons) to crack the passwords. Acutually rainbow tables were contructed by the companies as a backdoor, in case of forgotten passwords or other emergencies.
To resolve this issue we add salt to the hash. Salt is any random set of characters attached to the hashed password to make it more secure. Till now rainbow tables can't decipher the Salts because they are already taking too much storage and adding Salts would increase the combinations exponentially again.
By now, you must have realised that we are just making it diffiult for the hackers to crack the passwords, we are not making it impossible.
Brute Force can still be used for cracking, that is checking every possible combination of the password in rainbow tables. Addition of Salts have fetched us some time till Quantum Computers are in function. Because Salts too merely increase the possibilities as mentioned, which are hard to compute for classical computers. When Quantum Computers will actually come, then it will be a matter of seconds to break codes.
Till then you can have a good nights sleep.
Encryption
Apart from securing our personal data, we want secure communication as well. An encrypted communication, to be more precise. I have discussed below the types:
- Assymetric
- Symmetric
Assymetric Encryption:
Assymetric Encryption which involves with public and privat keys can be best explained by this famous padlock analogy:
Alice and Bob, both have padlocks and their keys. Alice wants to send a message to Bob. She will ask for Bob's padlock. On the way, the unlocked padlock could be locked by anyone but it doesn't matter. When the unlocked padlock reaches Alice, she locks the message with Bob's padlock and send him back. Now own the way, nobody can unlock that padlock because only Bob has its key. When Bob will get the message, securely locked with his padlock then he can open it with his key.Public key was the padlock and private key was the key itself. Both are linked to each other. If one get holds of a public key, he has to derive private key as well to unveil the message.
RSA algorithm is used to implement such procedure.
Symmetric Encryption:
The simplest explanation would be; when both the parties have the same key to encrypt or decrypt messages.
It is faster than Assymetric Encryption but it has a drawback; the distribution of the key. Unless both parties have met in person and decided upon a shared key. Otherwise, to send the key on internet would again make it vulnerable to hackers.
AES algorithm is used to implement it.
Let's take an example of Whatsapp which is said to use both techniques taking benefit from the speciality of both.
Alice and Bob are in modern world now. Alice wants to send a message to Bob on whatsapp.
Now according to ethics, as a one-to-one conversation, there shouldn't be any third person reading that message. Not even the Whatsapp company. Doesn't matter, what is the nature of that message, nobody wants their personal chats to be read by anyone.
A session should be established first. For that Alice will request the server, for Bob' public keys which she will get on the insecure channel. But that doesn't matter, alone public key won't do good to anybody.
Now that she has his public key and hers too, she will now generate a private message key using those keys and send it back to Bob encrypted with his public key.
Both have safely got a private message key via Assymetric Encryption.
Now they can send messages to each other encrypted with the same private message key.
This is symmetric encryption now in work which is faster as well.
How to check the connection is secure on Whatsapp?
The above mentioned proceudre was a behind the scene process.
To make sure, Alice and Bob has secure channel for conversation, they can check their mobile phones too.
In the chat window with Bob , Alice opens the option panel at the top right corner and clicks "view contact".
There she taps, "Encryption" and can see a 60-digit long number and a QR code.
She can send Bob that number and if it matches the number written at Bob's end on the similar window then that means they have a secure connection.
Or if they are sitting together, either can scan the QR code of the other and if it shows the Green Tick that means the connection is secure or encrypted.
Hole in Whatsapp Group Chat Security
I am sure, you know how the Whatsapp group chat feature works. When a group member adds or removes members, everyone gets notified. But the drawback is that this modification in group chat is not end-to-end encrypted (only users can read messages, not even server). If a whatsapp server gets compromised, hacker can easily add himself in the group and forge messages and modifications in the group.
The researchers have proposed a solution to that problem. That the power of adding and removing members should soley remain with the admin, not even to the whatsapp server. The hacker would need to get verified by the group admin to invade, which would be impossible then.
But Whatsapp hasn't resolved this issue still.
Is there any threat to Current Encryption Techniques?
Algorithms like AES (Advanced Encryption Standard) ) and RSA are used to generate keys for current encryption methods. These keys are way to large to be guessed by today's computers.
Yeah, I'm talking the same thing again. Quantum Computers will be able to guess the correct keys in just seconds.
Again the whole Crypto world would collapse.
Quantum Cryptography
Quantum Computing has given us enough tough time before actually coming into our lives. But it also provides us a solution to our issues.
Yeah, I am talking about Quantum Cryptography.
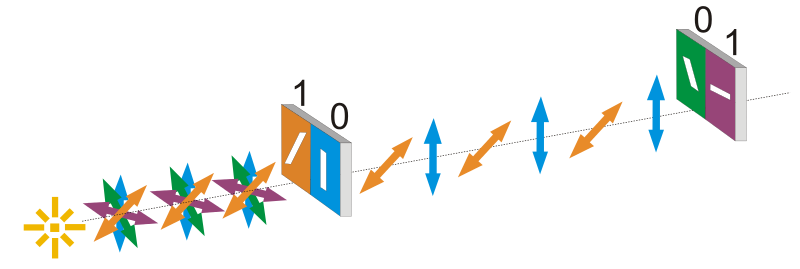
Quantum Key Distribution helps to create a key using the principles of quantum mechanics. This has already been explained by some great contributors, I am giving a simplified version of the picture for who haven't read it before.
- Alice sends photons to Bob through a light source.
- Single photon can be represented by a qubit.
- She has four sets of polarizers i.e, Horizontal or Vertical and Diagonal.
Horizontal H is assigned value 0.
Vertical V is assigneld value 1.
Diagonal DL at 45o left is 0.
Diagonal DR at 45o right is 1.
On the other end, Bob has two beam spiltters (horizontal or vertical and diagonal) and two photon detectors.
If horizontally polarized photon is sent by Alice, passes through Horizontal beams splitter, it remains horizontal. Same happens with others.
Now Bob will randomly choose beam splitter for each photon and will later tell Alice, in which order he used the splitters.
Alice will then tell him which photons he guessed correctly.
The correct photons which are represnting a number, will now be the encryption key.
| Alice | H , 0 | DL, 0 | DR, 1 | V, 1 |
|---|---|---|---|---|
| Bob | H | V | DR | DL |
| Bob's Measurement | 0 | 0 | 1 | 0 |
| Key | 0 | - | 1 | - |
Hackers interference would be easily detected in this phenomenon, because qubits will change, when hackers will try to measure the values. But in an experiment, hackers have managed to eavesdrop with minimum turbulance in qubits which wasn't detected easily.
That issue was resolved too by using the concepts of quantum entanglement. (I will explain it another post soon.)
Another limitation was the constraint on distance. This technique couldn't work at larger distances.
But a recent breakthrough related to the discovery of space photons has solved this issue too. The idea behind is that secure keys can now be generated using photons, between users thousands of miles apart with the help of satellites.
I am stopping here now because this will generate another discussion and we have already discussed too many concepts in this post.
References and Further Reading
1. Whatsapp Security White paper
2. Cryptography in Banking Industry White Paper
3. End-to-End Security of Group Chats
4. Quantum Computing taking over Today's Encryption
5. Space Photons for Quantum Cryptography
6. Hash Tables and Passwords
Note: I have left some questions and details unanswered on purpose in the end, that to be discussed in next post.