Proposal
Hackers have been attempting to figure out how to change the recovery account on phished accounts for some time and finally succeeded. These accounts are being set to accounts owned by the hackers.
Once the recovery account is changed, the user cannot recover the account.
Solution
Changing the recovery account should be disabled for a period of 30 days following a password change.
ie. Password changed on day 1. Change recovery account possible after day 31. Day 1-30 no change permitted.
Benefits
This would prevent hackers from changing the recovery account and locking users out within the password recovery period (30 days) / recovery account change period (30 days).
Mockups / Examples
From source:
if ( account_to_recover.recovery_account.length() ) // Make sure recovery matches expected recovery account
FC_ASSERT( account_to_recover.recovery_account == o.recovery_account, "Cannot recover an account that does not have you as there recovery partner." );
else // Empty string recovery account defaults to top witness
FC_ASSERT( _db.get_index< witness_index >().indices().get< by_vote_name >().begin()->owner == o.recovery_account, "Top witness must recover an account with no recovery partner." );
steem assert exception:account_to_recover.recovery_account == o.recovery_account: cannot recover an account that does not have you as there recovery partner.
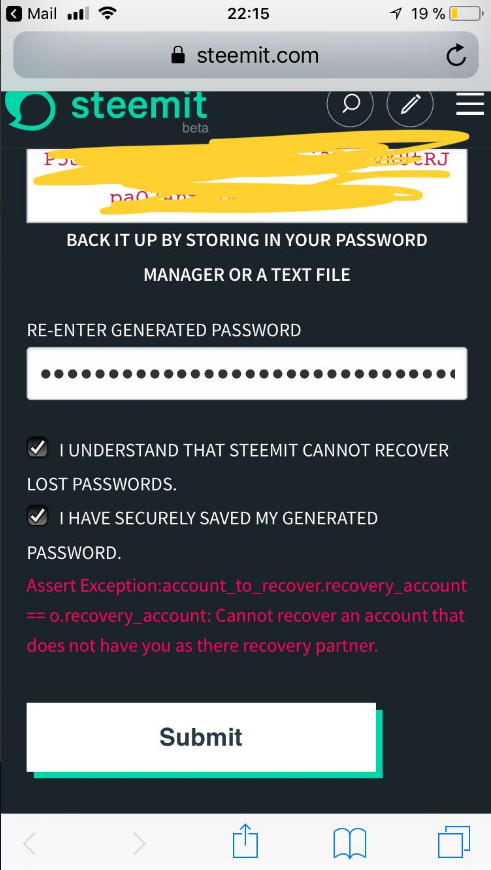
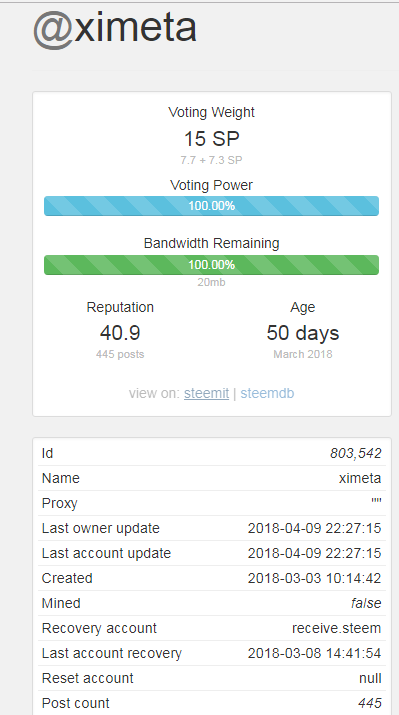
User @ximeta is a phishing victim whose account is now irretrievable. It's recovery account has been set to @receive.steem, the hacker.
 |
Like what we're doing? Support us as a Witness.Go to https://steemit.com/~witnessesAt the bottom, type in guiltypartiesClick VOTE |