Eclipse of 2016 二零一六的月蚀
Update: @sallybeth23 and @birudanak are victims of the scam. It's possible the other names listed are also victims. It means the scam is not new. It already exists for at least one month.
更新: sallybeth23和birudanak都是钓鱼骗局的受害者。估计其他人也都是受害者。看来这个骗局至少持续了一个月了。
Recently, @twinkledrop's account was phishing attached by @cheetoh. I searched the memo of the bittrex transfers and found that following accounts might be related to @cheetoh:
@sallybeth23, @birjudanak, @steemmatt, @angrysage, @albertbongers used the same memo of 612036a11c5c4b2ead6 before. 612036a11c5c4b2ead6 is the memo that @cheetoh to transfer @twinkledrop's money to @bittrex.
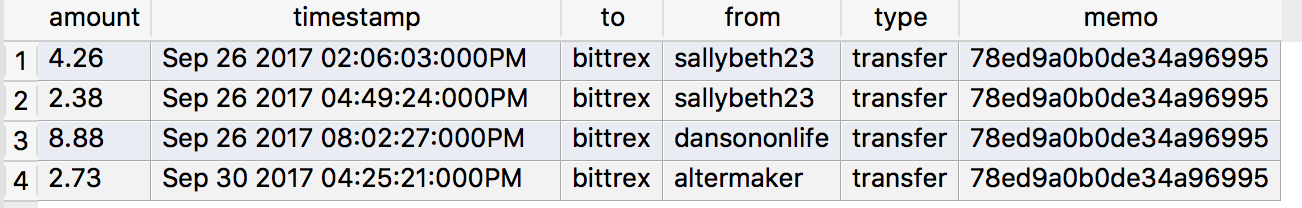
Furthermore, @sallybeth23 used 78ed9a0b0de34a96995 before. The same memo was also used by @dansononlife and @altermaker.
@birjudanak also used memos of bd4b4f58f6424813b39 and 6c433485aac646ae931. The first memo never used by other account. They second memo used by @albertbongers before.
Therefore, these accounts might be related. Today I don't have time to do more research. If any of you are interested, you may want to start from there.
最近 @twinklesong的账号 @twinkledrop遭受假猎豹的钓鱼袭击被盗号盗款。一个叫做 @cheetoh伪装成 @cheetah,在受害者帖子里留言中加入恶意链接并伪装成Steemit页面。受害者输入密码后,袭击者修改密码并把存款转入bittrex。
通过SteemSQL,可以看到骗子把受害者的六百多SBD转移到 @bittrex,memo是612036a11c5c4b2ead6。查询这个memo,可以找到以下记录:
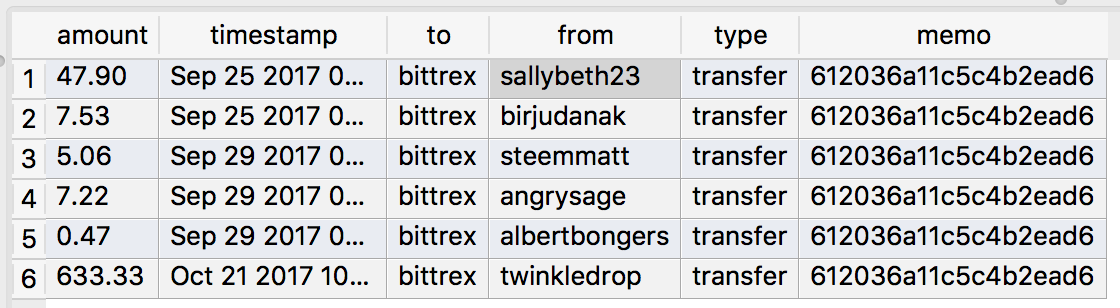
记录显示, @sallybeth23, @birjudanak, @steemmatt, @angrysage, @albertbongers都使用过同一个memo转款到 @bittrex。
查询一下 @sallybeth23转款到 @bittrex发现此号还用过另外一个memo:78ed9a0b0de34a96995。查询这个memo发现还有两个账号使用过这个memo: @dansononlife, @altermaker
查询 @birjudanak,发现它还使用过 bd4b4f58f6424813b39和6c433485aac646ae931。其中第一个memo其他人没有使用过,第二个memo @albertbongers使用过。
所以跟 @cheetoh相关的账号可能有:
我今天没有时间继续研究。大家谁有兴趣可以继续挖。
加勒比海系列
- Wild East of Aruba 阿鲁巴的洪荒东岸
- Palm Island of Aruba 阿鲁巴的游乐岛
- One Happy Island, Aruba 快活岛-阿鲁巴
- Rainforest of Puerto Rico 波多黎各的热带雨林
- San Juan, Puerto Rico 波多黎各的圣胡安
- Stingray City, Grand Cayman 开曼群岛的鳐鱼城🔥
- Don't Worry, Be Happy, Jamaica 无忧无虑之牙买加
- Cozumel 墨西哥小岛科苏梅尔
- Caribbean Sea 加勒比海上
- Half Moon Cay 半月洲
- USVI 美属维京群岛🔥
- Saint Lucia 圣卢西亚🔥
- Barbados 巴巴多斯岛
- Saint Martin 圣马丁岛🔥
- Saint Kitts and Nevis 圣基茨和尼维斯
- Cuba on the Horizon 遥望古巴
- Submarine of Aruba 阿鲁巴的潜水艇
- 邮轮攻略
更多系列游记
数据、观察、分析系列
- Observation and Analysis - The Dark Hand of Steemit 观察与分析 Steemit的黑手🔥
- How to Attract 200 Users per Day Under the Nose of Steemcleaners 如何放心地发垃圾评论
- Observation and Analysis - Firepower of Spamming 观察与分析之奇葩列传🔥
- Observation and Analysis - Heroes and Villains 观察与分析之侠客英雄传
- Observation and Analysis 20171004 观察与分析之雪花飘
- Observation and Analysis - Blocktrades 观察与分析Blocktrades
- Observation and Analysis 观察与分析 20171002
- 2017年9月下旬中文区大鲸点赞统计
- Observation and Analysis 观察与分析 20171001
- Upvote Analysis of CN Whales CN区大鲸点赞分析
- Upvote Analysis of CN Whales II CN区大鲸点赞分析之二
- Reflections on Steemit 有关Steemit的杂想
- 魑魅魍魉
- 聊聊聊斋
技术系列
- 手把手教你做机器人
- Use MacBook to Access SteemSQL and Find Delegator 用Mac搜索SteemSQL查询SP代理
- Show Rank of Reputation with SteemSQL 用SteemSQL显示声望排名
- The Posts with Top Payout 史上收入最高的帖子
- 教大家一点SteemSQL黑科技
- SteemitSQL继续教大家学坏
- How to Use Voting Power Efficiently? 如何点赞最实惠?
© Copyright 所有照片与文字皆为 @nationalpark原创。All photos taken by @nationalpark. All rights reserved.
