
Yesterday, in a post about decentralized trading, I alluded to the fact that the password you should choose to protect the #bitsquare application should be long and random.
Essentially the same tips that people have been giving regarding steemit passwords - and with very good reason.
Today I would like to delve deeper on the topic of securing your password manager.
Choice of software
For many years I have used KeePassX.
I do not like the latest versions so much, at least up to the last time I have evaluated them. I recommend you stick with the 0.4.x series.
My reasons for choosing this software are the code being open source, an intuitive and easy to use interface (in my opinion that changed in later versions, hence the recommendation for 0.4.x), and zero problems with it over the years.
There is also, to the best of my knowledge, no backdoor in the software.
Limitations of a Password Manager
Like most things in life, password managers are not silver bullets.
You will probably be better off by using one (provided you take care of backing up your data).
It should go without saying that if your computer security is compromised, then having a password manager installed represents a very, very attractive target.
For most non-technical users this alone is a big risk, but the fact of the matter is that in the event of a compromise, a keylogger would accomplish the same (obtaining all of your passwords), just over a longer timespan.
In my opinion you are still better off by managing most of your passwords with a password manager. The randomness (and thus strength) of your passwords will otherwise be subpar.
All of this to say, in my analysis the benefits of running a password manager outweigh the disadvantages.
But we can up the game (considerably).
Security overview
Here we will explore what you can do to help secure the keys to the kingdom.
First things first
I am putting this one up first because I figure (unfortunately) that it is the least likely to be implemented.
It is also the most important.
If you run Microsoft Windows, get rid of it.
Simply put, if you are interested in more than the illusion of having any resemblance of a secure (to say nothing about private) system, you must switch operating systems.
There is no meaningful way that Windows can truly ever be secured. I am not exaggerating.
In the grand scheme of things, if you cannot trust your operating system, none of your applications are safe.
By the same token, if the operating system cannot trust the hardware, neither the operating system nor the applications are safe .. but that is a story for another day.
You will greatly reduce your attack surface, improve your privacy, and improve your security, for simply ditching Windows.
Get a Mac if you must (more secure, easier to learn than other Unix-like systems, can be reasonably secured from snooping by Apple).
Or run a beginner-friendly GNU/Linux distro. Heck, even PC-BSD.
But ditch Windows - if you are serious about securing your computing.

Now that I have lost 95% of the audience, we continue ..
Isolate the Password Manager application from the Network

Your computer is connected to a global computer network.
On this network, many interesting things happen. Actually, most of it is cat videos ..
Anyway.
Automated computer systems continuously scan and identify targets on the network.
It is basically an historical accident that your computer is actually (most likely) not directly reachable from other machines on the Internet.
NAT was not intended as a security defense, but to a certain extent it does fulfill that role today.
Something that is not visible nor present cannot be attacked.
This is the same principle you should employ for your password manager - remove it from the network altogether.
The software should not be making connections to the Internet anyway, but since it is all of your passwords sitting there.. would you not like to make sure ?
There are two ways to go about this.
The easiest one is deploying a firewall that is capable of filtering traffic per application.
You simply remove network access from the password manager using the firewall.
The better and more complicated one (for a host of reasons) is to relegate the password manager to a virtual computer, and assign no network access to the virtual computer.
This is a more complete solution, but much like changing your operating system, will require that you significantly change your computer habits.
For that reason I will leave that thread open here, and write a series of articles about virtualization if there is enough demand - leave a comment if you would like to see it happen.
Encrypt your hard disk

There are solutions for Windows, Mac and GNU/Linux.
The benefits of encrypting your storage go much further beyond than securing your password manager, especially if you do your computing from a portable device (laptops, etc).
If your laptop is ever lost or stolen, provided that you have chosen a strong password to encrypt the storage, there is little to worry about - in most cases.
You should know that unless specifically configured, your encryption passphrase will remain in memory if you suspend (not hibernate or shut-down) your computer.
Specialized procedures can be used to recover the key from memory in that case.
At least for Linux and Mac, it is possible to flush the key from memory when the computer is suspended, but you will have to input it again when waking the computer up.
Whether that is worth the hassle or not depends on your personal situation.
Uninstall as much crap as possible
Without wanting to go too deep into the flawed security models of modern operating systems when it comes to what amounts to single-user usage of a multi-user system, let's just say that any other programs you have running are prime candidates to steal all those very safe and long passwords that you have been busy saving in KeePassX.
It is not the security of KeePassX that is broken, so do not let the above stop you from using it .. particularly if you isolate the program on its own virtual machine with no network access.
Securing the Password Manager Application
Up to this point we have been discussing how to create as safe an environment as possible for the application to live.
Now it is time to focus on the password manager itself.
There are several settings that you should adjust in order to properly secure the application.
Use a strong (but not random) password AND a keyfile to encrypt the application

Your KeePassX password is more than just a password. It will also encrypt the contents of the database (all of your passwords) when storing data.
This means that if you lose your device (and failed to encrypt your hard disk), or if through some exploit an attacker is able to get a hold of your keepass database, it does not automatically follow that he would get access to your passwords.
If your password(+keyfile, see below) was good enough, it is infeasible to brute-force it.
You can further improve the situation by making use of a key file.
The way it works is that you will be creating a strong (but memorable) password, and make use of a special file that will also be necessary to unlock the database.
You have two choices here regarding where to place the keyfile.
The more secure, more inconvenient one is to place it in a USB pen.

The advantage is that the keyfile is not directly accessible from your computer, and the disadvantage is .. pretty much the same -- this means you will need to plug in a USB pen whenever you want to unlock the database.
Or you can simply choose a file that you know will never change (for instance, a picture from a holiday many years ago, just make sure to not edit it :-)) and always have it (inconspicuously) accessible on your computer.
Since both keyfile and password will be necessary to unlock the database, if someone else gains access to the keyfile, it is not the end of the world - though it should still be avoided..
If you have decided to continue running Microsoft Windows, I recommend that the keyfile (which, by the way, can be any file you want, just keep it under 1 megabyte.. up to about that, the bigger, the better) remain outside of the computer (usb pen).
And remember -- if you ever lose the keyfile OR the password, there is NO WAY to recover your passwords - backup accordingly !
Configure sensible settings

It is important to not remember the location of the keyfile, in order to not provide unnecessary clues to a would-be attacker.
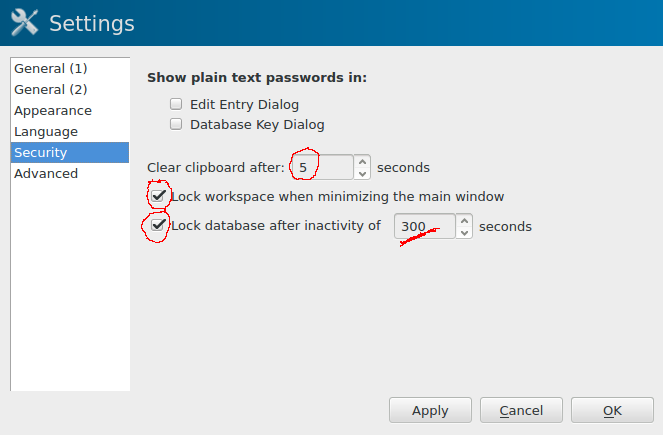
We make sure that the clipboard is cleared fairly quickly - you do not want to have a password available on the clipboard for longer than it is necessary (clipboard is when you copy/paste)
We also configure the program to lock itself if you close the main window (it will remain in the system tray), as well as locking the database (and expunging the encryption keys from memory) after a certain timeout - in this example, 300 seconds (5 minutes).
General usage principles
Make sure no one is around you when typing the password for unlocking keepass.
If you know you will not be needing to copy/paste another password, lock the database immediately. The less time the database is open, with keys available in memory, the best.
Remove the USB pen, if you chose that route, as soon as you lock the database and you know you will not be needing to access it.
Only one more thing to worry about

can't help much with that ..
