A new vulnerability has been discovered on Cisco devices. It is possible to access Cisco Routers and Switches without any form of authentication.

Smart Install
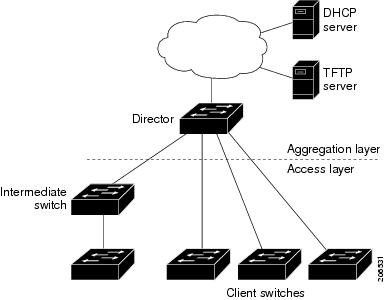
Smart (SMI) install is a feature that is used on Cisco Networking devices. The Protocol can be used for the automated (zero-touch) remote configuration of Cisco Networking devices.
The feature is often used if staging the network devices on site is not an option and remote access is the only way to configure the device.
The downside
SMI doesn't use authentication or authorization protocols and because of this anyone with access to the protocol can gain access to the configuration of the networking device. This person will be able to to edit the configuration and rewrite it. Furthermore it is also possible to execute commands on the network device using the command line. This means that the entire network can be hacked. Unauthorized persons could disable, tap or take control of the network.
Why it matters
The Smart install feature is "on" by default. That means that when installing the network devices that you actually have to turn it off if you are not planning on using this feature. Chances are most people, even IT technicians are not aware that this protocol is enabled on their network.
The countermeasures
Cisco does not consider this a vulnerability but a feature included on their network devices. That's why they are not planning on releasing a fix. Their advice is to turn off the Smart install if you are not using the protocol.
To check if your network devices (primarily switches) are vulnerable, input the following command in the command line (IOS or IOS XE):
switch#show vstack config | inc Role
If the output is:
Role: Client (SmartInstall enabled)
Then your devices are vulnerable to the exploit.
To disable the Smart Install feature use the following configuration command:
no vstack
When you are making use of the Smart install feature and don't want to turn it off than it is advisable to split your network into sub-networks (network segmentation) this way the protocol will only be active in parts of your network. This will prevent hackers of taking over your entire network.
Sources
Source of the exploit and detailed how-to
Cisco's response to the misuse of the feature
More info about the exploit

If you like my posts then click on the image to follow

The Lowdown on Emulators
The Best Thing For Steemians to do Now is....
My Favorite Mega Drive/Genesis Games
Why the New Dutch Wiretap Law Matters to you
The Future of Gaming Consoles
Highly Recommended!-Quality vs Quantity on Steemit

