What makes a Cryptosystem Strong?
Hello,I am digicrypt and thank you for checking out Part 3 of my “Cryptology Series” where we attempt to answer this question. If you are interested in learning more about Cryptology be sure to check out parts 1 and 2 of my series below. If you have any questions about the terminology used refer to Cryptology Series Part 1: Getting the Basics or leave a comment below.
Cryptology Series Part 1: Getting the Basics
Cryptology Series Part 2: History of Cryptography
Let's get started!

Cryptology Series Part 3: Strength Of Cryptosystems
Understanding the basic elements that provide strength to cryptosystems is really helpful if you have any interest in cryptocurrency. These principles will give you an understanding of why cryptocurrency involve certain aspects.
Kerckhoffs Principle
The only secrecy involved with a cryptography system should be the key.
Making an algorithm public allows more people to test the source code and discover any weaknesses.
This practice is still considered controversial.
"Kerckhoffs's principle is one of the basic principles of modern cryptography. It was formulated in the end of the nineteenth century by Dutch cryptographer Auguste Kerckhoffs. The principle goes as follows: A cryptographic system should be secure even if everything about the system, except the key, is public knowledge."
Strength of Cryptosystems
Strength comes from....
- The algorithm
- Secrecy of the key
- Length of the key
- And how they all work together
"Kerckhoffs's principle is applied in virtually all contemporary encryption algorithms (DES, AES, etc.). These algorithms are considered to be secure and thoroughly investigated. The security of the encrypted message depends solely on the security of the secret encryption key (its quality)."
Work Factor
Work factor- is another name for cryptography strength, which is an estimate of the effort and resources it would take an attacker to penetrate a cryptosystem.
Cryptosystem Strength
Cryptosystem Strength should provide…
- Confidentiality- data is unreadable to unauthorized users
- Integrity- data has not been altered
- Authentication- verifies identity of user
- Authorization- once identity is proven user is provided with access
- Non-repudiation- sender cannot deny the message
"Unbreakable Cryptosystem"
One-time pad- is considered unbreakable if implemented properly.
Invented by Gilbert Vernam 1917
The cipher works by using random binary values and performing a binary mathematic function known as the exclusive or (XOR)
"In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a one-time pre-shared key the same size as the message being sent. In this technique, a plaintext is paired with a random secret key (also referred to as a one-time pad). Then, each bit or character of the plaintext is encrypted by combining it with the corresponding bit or character from the pad using modular addition. If the key is truly random, is at least as long as the plaintext, is never reused in whole or in part, and is kept completely secret, then the resulting ciphertext will be impossible to decrypt or break."
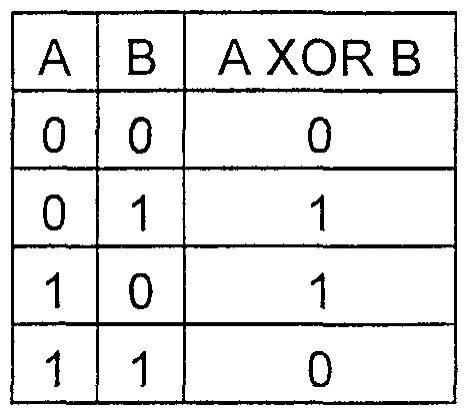
Message stream 1001010111
Key stream 0011101010
Cipher text 1010111101
Extremely hard to break because it is at the bit level.
Requirements
- Pad may only be used once, otherwise patterns may emerge
- The pad must be as long as the message
- The pad must be securely distributed and protected at its destination
- The pad must be made up of truly random values
- Computers cannot make truly random numbers only pseudo-random numbers
I hope you enjoyed Cryptology Series Part 3: Strength Of Cryptosystems! I will be working on Part 4 but in the meantime stay tuned for another Cryptography Challenge! If you are interested in sponsoring a challenge, send 25 STEEM with the message "Sponsor Crypto" to my account. I will list you as the sponsor and do a brief write up advertising your blog! Thanks!
Sources
http://www.crypto-it.net/eng/theory/kerckhoffs.html
https://en.wikipedia.org/wiki/One-time_pad
The CIISP Exam Guide Sixth Edition ISBN:978-0-07-178174-9
Please upvote and resteem if you found this post interesting!
Follow my blog @digicrypt if you want to learn more!
If you would like to show my blog further you can use either of the addresses below
DASH: XgQ9NBonMoCPKhF37agY4W8zk7gwQFnwGV
Ether: XE04RO3I0QA5UKB31OZK4O3CK3TOT03R4TM

Logo via https://logomakr.com/
