Cryptology Series Part 2: History of Cryptography
Hello,I am digicrypt and thank you for checking out Part 2 of my “Cryptology Series”! If you haven’t done so already, go to my #introduceyourself post here. The post will give you a bit of my background and help explain what I plan to do with this blog.
You can also view Cryptology Series Part 1:Getting the Basics here
Thanks now let’s get started!

Cryptology Series Part 2: History of Cryptography
This post will highlight several cryptography methods and devices spanning nearly 4,000 years of history. These devices mark milestones of achievement, but they are by no means the only methods used. The most recent method covered is from the 1980s, more "modern" methods such as DES, AES and RSA will be covered in another post which will go into greater detail about function and type. I will also be covering elliptical and quantum cryptography later on.
First encryption methods date back 4,000 years ago.
Around 2000 BC in Egypt hieroglyphics were used to decorate tombs, some hidden meanings were included but mostly for decoration and to add to the mystery of life.
Encryption methods evolved from decoration to being used to hide information for practical use
Atbash
A Hebrew cryptographic method known as Atbash required the alphabet to be flipped so each letter in the original alphabet was mapped to a different letter in the flipped alphabet.

Scytale Cipher
Around 400 BC the Spartans wrote messages on papyrus wrapped around a wooden staff.
In order to read the message, the receiver would have to wrap the papyrus around a same size staff, otherwise the letters would appear jumbled.

Caesar Cipher
100-44 BC Julius Caesar developed a simple method of shifting the alphabet
The alphabet was shifted by 3 positions
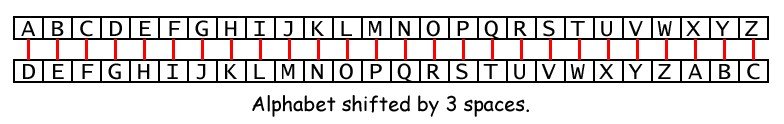
For example the word Steemit would become Vwhhplw
This method although now seemingly primitive proved effective at the time and was even modified to be used again in the 1980s on message boards with ROT13.
For more detail on the Caesar Cipher
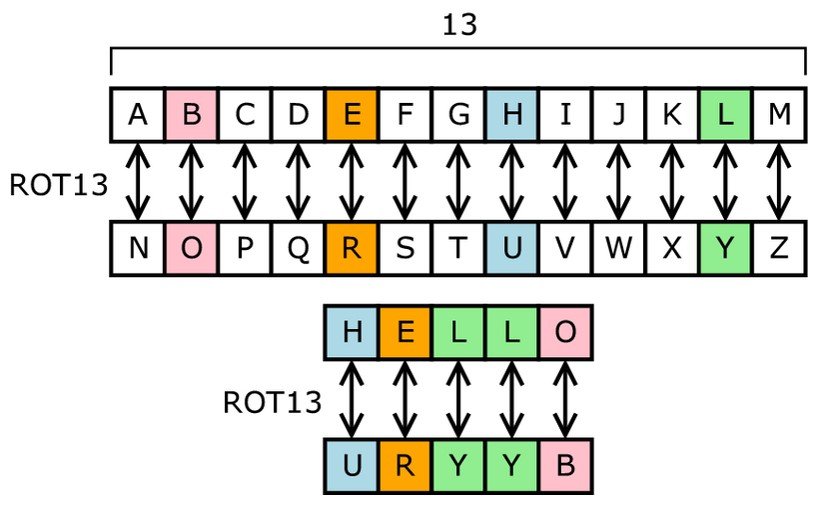
Rot 13
ROT 13 was used in the 1980s, like the Caesar cipher it shifted the alphabet, this time 13 spaces.
Wasn’t used to protect data, instead it was used on message boards for inappropriate material.
Those who wish to view it simply add 13, those who don’t want to view the material don’t and just see gibberish.
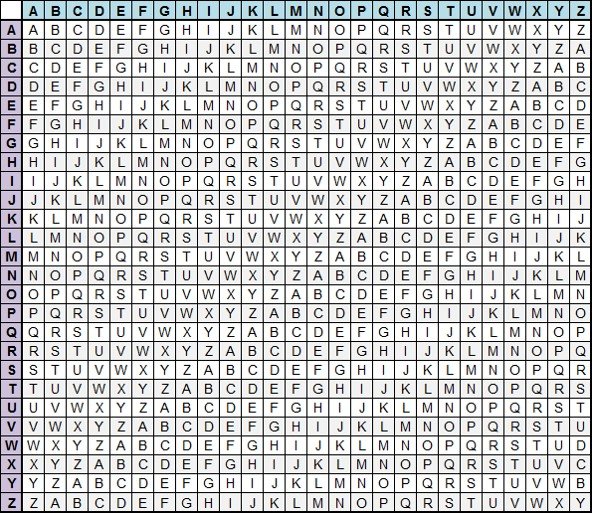
Vigenere Table
In the 16th century Blaise de Vigenere developed a polyalphabetic substitution cipher for Henry III
27 different alphabets
"The Vigenère cipher is a method of encrypting alphabetic text by using a series of interwoven Caesar ciphers based on the letters of a keyword."
"Though the cipher is easy to understand and implement, for three centuries it resisted all attempts to break it; this earned it the description le chiffre indéchiffrable (French for 'the indecipherable cipher'). "
Jeffersonian Wheel Cipher
While serving as George Washington's secretary of state (1790-1793), Thomas Jefferson devised an ingenious and secure method to encode and decode messages: the wheel cipher.
Jefferson's wheel cipher consisted of thirty-six cylindrical wooden pieces, each threaded onto an iron spindle.
spells the message out and then looks to any other line of text -- possibly the one directly above, copies the rest of the letters from that line into the correspondence.
For more information on the Jeffersonian Wheel Cipher

M-94
The US Army used a cryptography device designated as M-94, nearly identical to Jefferson's design that had yet to be discovered. The M-94 was used from 1922 to 1945.

Enigma Machine
By the late 1800s cryptography was common practice for militaries.
During WWII the Germans developed one of the most infamous cipher machines of all time the Enigma Machine.
Enigma machine was a rotor cipher which substitutes letters using different rotors and settings.

The operator would move the rotors a predetermined number of times to substitute letters. The rotors would be reset for every letter.

The Enigma Machine was very advanced for it's time and caused huge problems for the allies during the war. The Enigma machine was eventually cracked and is considered one of the reasons the allies were able to win the war. Alan Turing receives most of the credit for this achievement.
" Turing played a pivotal role in cracking intercepted coded messages that enabled the Allies to defeat the Nazis in many crucial engagements, including the Battle of the Atlantic; it has been estimated that this work shortened the war in Europe by more than two years and saved over fourteen million lives. "
Although there is much more to the story...If you are interested I will do a post about what really happened and some heroes who rarely get credit.
I hope you learned something new and I hope you will stick with me for Part 3 of my Cryptology Series. If you want more detail on some of these methods check my old posts which are linked in the article. If there is a method that you would like to see me cover or cover in greater detail leave a comment and let me know.
Your feedback is really important to me, please comment and let me know if you liked this post or have questions.
Please upvote and resteem if you found this post interesting!
Follow my blog @digicrypt if you want to learn more!
If you would like to donate so I can post more and host more complex cryptography challenges with bigger prizes, below is my DASH address.
DASH: XgQ9NBonMoCPKhF37agY4W8zk7gwQFnwGV
Digicrypt,
Signing Off
