All the governments just want to have more power when it comes to economic espionage, diplomatic manipulation & political influence.
Edward Snowden

DARPA's Memex, is attempting to index the dark web or search results from web pages that were intentionally designed to remain hidden.
Is governments wanting more power
just an attitude of self-preservation?
Or ,
Is the deep state,
unelected & unaccountable,
using its defense intelligence complex
to gather any information,
"that may be needed in the future."
Edward Snowden revealed Boundless Informant, BULLRUN & PRISM: the tools that the deep state developed which collect, slice & dice information on everyone & everything on the basis that it may be needed. DARPA is developing Memex to index the whole internet.
Snowden himself is in the vanguard of the baby steps to take back the internet from the deep state through the Introspection Engine.
Boundless Informant
Boundless Informant, an NSA datamining tool counts & categorizes metadata, rather than specific content.

Boundless Informant maps computer, telephone & telecommunication networks. Green represents areas least surveilled through yellow through orange through red most surveilled. 2007 refers to the document from where the map is classified; not the map.
Bull Run
BULLRUN penetrates target defenses unlocking encryption used to protecting email, banking & medical records by covertly inserting weaknesses into products. By its Pyrrhic victory over the use of ubiquitous encryption across the internet, the NSA has opened the door to any actor to hack any encrypted service. China, Russia, India, Al-Qaeda or ISIS have the potential to enter any door left ajar by the NSA.
By neutering encryption,
BULLRUN has shredded
the very fabric of the internet,
making the world unsafe
for everyone on the planet.

With or without the co-operation of ISPs, the NSA inserts backdoors or trapdoors into commercial encryption making them vulnerable to hacking. In addition, the NSA plays a role in creation of the encryption standards & has the resources to summon the computing power necessary for massive brute force attacks.
PRISM
While BULLRUN tracks metadata, PRISM is NSA's tool to scoop up content.
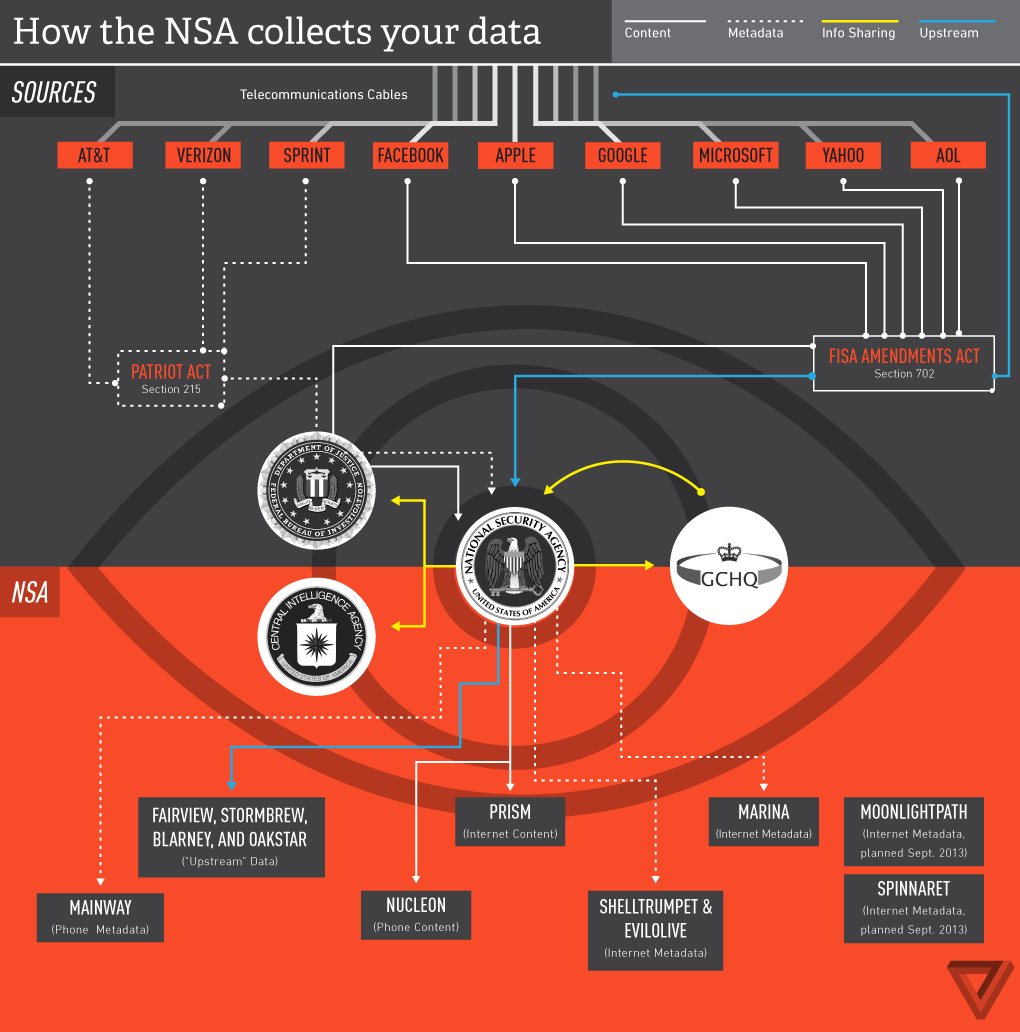
NSA's SIGAD US-984XN, code named PRISM is known to collect internet content from at least 9 US internet companies.
PRISM
Personal Record Information System Methodology.
PRISM integrates Personally Identifiable Information,
including name & address,
with data records accessed from
emails, text messages & telephone conversations.
On the radar
In the guise of fighting nefarious crypto actors, blockchain is on the radar. Chainalysis is creating the plumbing to mitigate national security concerns in virtual currencies.
What restraints are in place for Sixgill's probes of the dark web to identify & predict patterns of criminal activity?
What stops the continuous mass surveillance of the dark web to try & spot criminal activity, hacks or leaks before they occur, from being used for state control?
Anyone who influences or controls the internet influences or controls the world. The dark web was the citadel of refuge for privacy & anonymity.
With more than 900 billion pages, the dark web is 15 times larger than the surface web. DARPA estimates that there are 30K to 40K Hidden Service Onion sites that Memex could index. For how long will TOR remain an onion?
What vulnerabilities in Internet of Things sensors are ripe to be exploited?
Privacy : ideas :: evolution : biology. Is the anonymous internet indispensable for the marketplace of ideas? Do some things deserve to stay in the dark? Should everything be in the light? Who should decide what stays in the dark? Who are the decision-makers accountable to?
My personal battle was not to burn down the NSA or the CIA.
Edward Snowden
Introspection Engine
Edward Snowden & Andrew “bunnie” Huang have prototyped an iPhone add-on: the Introspection Engine to detect whether an iPhone is secretly transmitting, even in airplane mode. A baby step to help an individuals take back the internet.

Snowden making a phone go black.
As Apple ramps up production of the iPhone X & iPhone 8, journalists & activists covering repressive regimes are at risk in countries that can hack smartphones.
It is commonly believed that airplane mode immunizes a smartphone from surveillance. Introspection Engine even verifies that mobiles in airplane mode, are not transmitting or receiving signals. As open source hardware, Inspection Engine is an in an iPhone’s battery case displaying whenever the iPhone uses its Wi-Fi, cellphone, Bluetooth, or GPS.
Today,
TOR : deep web :: surface internet : deep state
Is there hope that
Tomorrow,
Internet : freedom :: privacy : ideas?

You may also be interested in:
In a sermon, who is the hero?
President Trump at the United Nations. Is Hurricance Trump likely to make landfall?
Are you ready for God to propel you to your next level?
What if there is a 10g Gold Cube waiting for you? Your chance to win more gold from Goldmoney!
Your first name, last name & phone number is enough to hack your Coinbase wallet
He never abandons those who trust & call on Him
Holy Spirit must come down. And Africa will be saved
Could a 24K Gold Cross Pendant Necklace be yours?
My soul magnifies the Lord & my spirit rejoices in God my Savior.
I Exalt Thee



