If you are new to my Cryptology Series or are having trouble with any of the terminology, I encourage you to go to my blog and check out parts 1,2,3,4 and 5. I will link to the other parts of the series at the bottom of this post. Now let's get started!

In Cryptology Series Parts 4 & 5 we discussed the two main methods of encryption systems, symmetric and asymmetric systems.
Symmetric Cryptography
Uses symmetric keys known as secret keys, sender and receiver use two instances of the same key
Benefit: much faster and less computationally intensive
Weakness: Secure key distribution
Asymmetric Cryptography
Two different asymmetric keys that are mathematically related
One public and one private key
Benefit: better key distribution
Weakness: slower
This post will focus on Asymmetric systems.
Types of Asymmetric Systems
RSA
Public key algorithm
Developed at MIT in 1978
Most popular asymmetric algorithm
Security comes from the difficulty of factoring large numbers into their original prime numbers
Often used for key exchange
Uses one way function
“RSA is one of the first practical public-key cryptosystems and is widely used for secure data transmission. In such a cryptosystem, the encryption key is public and differs from the decryption key which is kept secret. In RSA, this asymmetry is based on the practical difficulty of factoring the product of two large prime numbers, the factoring problem.”
One way function (Important Concept)
One way function- a mathematical function that is easier to compute in one direction than in the opposite direction (Broken glass) Trapdoor (How to put the glass back together)

Elliptic Curve Cryptosystems
Provides much of the same functionality as RSA: digital signatures, secure key distribution and encryption but is much more efficient Uses points on elliptic curve for values in the algorithm
"Elliptic curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields. ECC requires smaller keys compared to non-ECC cryptography (based on plain Galois fields) to provide equivalent security"
If you want to dig into the details of ECC check out this blog, which gives a very detailed primer on ECC,
http://andrea.corbellini.name/2015/05/17/elliptic-curve-cryptography-a-gentle-introduction/
Hashing
One way hash- a function that takes a variable length message and produces a fixed value to ensure it was not altered
"A hash function is any function that can be used to map data of arbitrary size to data of fixed size. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes."
Hashing Algorithms
MD2
MD4
MD5
SHA
HAVAL
TIGER
Tip: Hash functions are really important when dealing with digital forensics.They are used to ensure evidence was not tampered with or altered.
Important Crypto Terms To Know
Digital signature- ensuring the authenticity and integrity of a message through the use of hashing algorithms and asymmetric algorithms. The message digest is encrypted with the senders private key
Public key infrastructure (PKI)- is a set of hardware, software, people, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates.
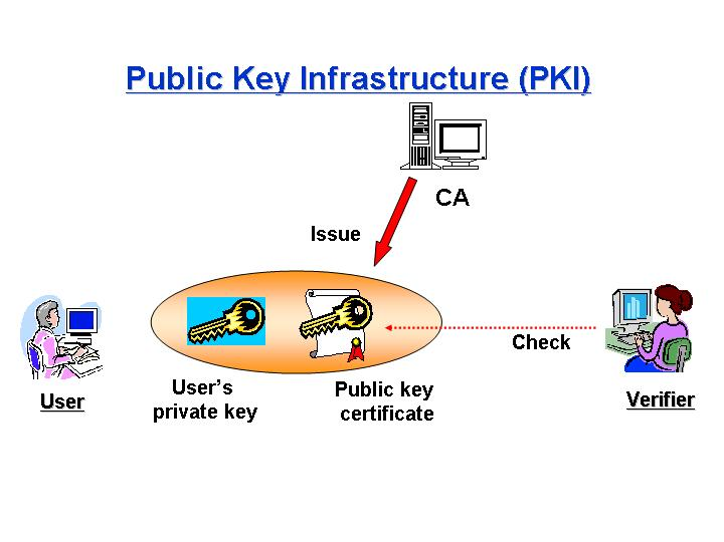
Certificate- is an electronic document that uses a digital signature to bind a public key with an identity
Certification authority (CA)- is an entity that issues digital certificates
These topics can get quite complex and this post is really only covering the fundamentals. If you have questions let me know, if you want more cryptology posts on certain topics let me know that too....I am considering doing a post specifically on cryptology used in cryptocurrency if people want that, let me know in the comments.

I am also hoping to have a new "Tales From The Crypto" out pretty soon, so stay tuned!
Sources
https://en.wikipedia.org/wiki/Hash_function
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Elliptic_curve_cryptography
http://andrea.corbellini.name/2015/05/17/elliptic-curve-cryptography-a-gentle-introduction/
https://www.youtube.com/channel/UCItMD0Mfb7kb4IiIhbg3fKQ
Thank you for reading Cryptology Series Part 6:Types of asymmetric Systems
If you had any trouble with terminology or the concepts involved check out the other parts of my series
Cryptology Series Part 1: Getting the Basics
Cryptology Series Part 2: History of Cryptography
Cryptology Series Part 3: Strength Of Cryptosystems
Cryptology Series Part 4: Methods of Encryption
Cryptology Series Part 5: Types of Symmetric Systems
Part 7 of my Cryptology Series will focus on Key Management
Follow my blog @digicrypt if you are interested in cryptocurrency, cryptology or blockchain.
DASH: XgQ9NBonMoCPKhF37agY4W8zk7gwQFnwGV
Ether: XE04RO3I0QA5UKB31OZK4O3CK3TOT03R4TM


