Every Fortress Can Be Undermined
The weakness of oligarchy/corruptocracy/kakistocracy as an organizational method is that it is centralized. While not every action committed by an underling at the operational level is specifically ordered by a person at the command level, the actions of the underlings has to be within a range determined from above. If not, the efforts of the command level would be consumed by putting out fires caused by low level blunders. While low level blunders do occur, they are punished within the means of the corruptocracy, if not always from the nominal legal system.
This means that oligarchies (etc) are subject to decapitation strategy. While decapitation strategy is usually assumed to mean that "the head of the snake is cut off", in normal operations against criminal and terrorist organizations, the strategy is used against mid-level operatives; local leaders, bagmen, organizers, etc. In the Marine Corps, we called the NCOs the layer of organization where "the rubber met the road", meaning that is where things got done.
While I do have a post on decapitation strategy in the works, I did want to point it out now to contrast the strength in decentralization in opposition to corruptocracies. It is very hard to cripple an organization if there is no central leader or centralized chain of command. This is why underground cells have been effective in counter government operations when they have been properly set up.
I'm not here to talk about organizing cells, however. I'm here to talk about the decentralized tools you can use in your own, self-directed operations.

Bennett, Chattanooga Times Free Press
There is a counter-message in this image ;>
Decentralization
Decentralization is a current buzzword; perhaps the wave of the future. Obviously, if you are here on Steem, you have had some exposure to the potential of decentralization. I won't get into an argument here about whether every human activity can or should be decentralized. I will argue that decentralized tools are going to be very effective in the Information War against the Deep State and their like, which is one reason why there has been some major resistance to ideas like Bitcoin from the establishment.
So what kinds of decentralized tools are available?
TOR/TAILS

https://tails.boum.org/
I pointed out in the very first post (see series index) the crucial part this system and it's analogues have in fighting the Information War. What this system does is to move to move your net communications from one node to another, "wrapping" them in a crypto cover from one node to another, before your end communication is sent to the destination, and then repeats the process on your messages return. There are other systems that are similarMesh Nets
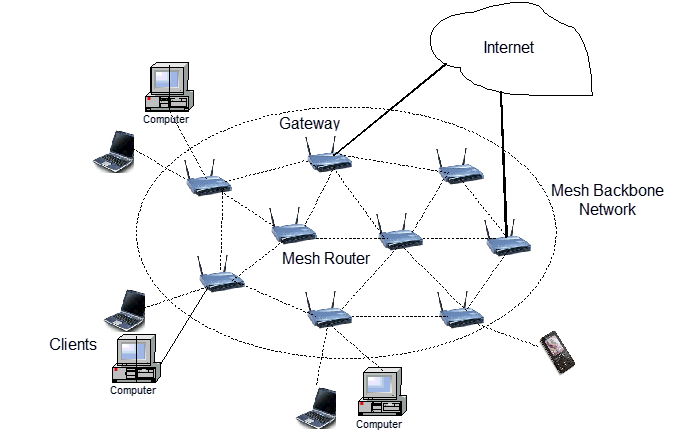
What is a mesh net? From Wired
An ad hoc network infrastructure that can be set up by anyone, mesh networks wirelessly connect computers and devices directly to each other without passing through any central authority or centralized organization (like a phone company or an ISP). They can automatically reconfigure themselves according to the availability and proximity of bandwidth, storage, and so on; this is what makes them resistant to disaster and other interference.
Mesh nets are criminally underappreciated by the public as a whole: as stated, they are resistant to disaster...what makes them infinitely more appealing is that they are "resistant" to some one agency turning off the router at the "home office".
Compared to more centralized network architectures, the only way to shut down a mesh network is to shut down every single node in the network.
One issue in establishing mesh net networks is that many participants are required in order to provide both range and resilience.
Some mesh net resources:
Anonymous/Semi-Anonymous currencies
Bitcoin is the big name; although BTC transactions can be traced to some accuracy, especially if you buy them under your own ID, their semi-anonymous nature can be made fully anonymous by understanding how the transactions work, and the appropriate measures taken to conceal them. I haven't had time to look at fully anonymous cryptocurrencies yet (I welcome suggestion and discussion in the comments on this point!). Financing operations and supporting oneself during operations are key considerations in Information War. There is a method of terrorist financing we can compare to; Hawala, the prevalent method of money transmission for Islamic terrorists (this was the method that the New York Times was so eager to expose our penetration of, btw). However, Hawala is semi-decentralized, and such networks are built on personal trust levels and face to face contacts, making them easier to spy on.
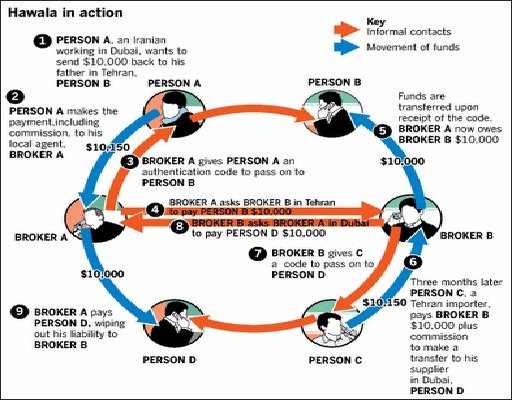
The problems of anonymity

I keep noting anonymity as a benefit of decentralization. Activists must be able to protect themselves from retribution from corruptocrat operatives and agencies. Let's look at the dangers of such methods (which is one reason I am not providing a lot of detail in their use).
- Evil Intent
These methods can be used by criminals and terrorists. This is the prime reason I don't go into procedural tutorials ;> In fact, were our security agencies to DO THEIR DAMN JOB AND PROTECT THE CITIZENRY, I would not be discussing these methods at all. But here we are. - Cross Purposes
Because we are in an Information War, it is easy to get a target wrong; to be incorrect in assessment; to strike at the innocent; to sabotage an ally; or even to support the enemy. Anonymity protects us from the unjust, but it shields us from accountability in our own mistakes.
Conclusion
There tools you can use to build decentralized networks, and to use such networks to shield your own actions. You need to do your utmost to keep your action on target both in facts, and in morality. If used correctly, the only person that can punish you is you.
The tag

The tag #informationwar, and posts that would be classified under that tag include methods of Information War, Propaganda, and Disinformation. The discussion would include governmental doctrine, historical application, Information War on the spectrum of warfare modes, recognition of fakenews, public OSINT, the concept of a Deep State and reaction to it, and critical thinking in analyzing these concepts.
By necessity, conspiracy theory can be discussed under this tag as they often address what many view as Deep State disinformation; this means that discussion of PizzaGate could fall under this discussion.
The ultimate purpose of my focus on InformationWar is to provide you with the tools to defend liberty within this mode of war.
This series index:
So you want to be an InformationWar Activist? - Part One (UPDATED)
How to be an InformationWar Activist - Part Two, Morality (UPDATED)
How to be an InformationWar Activist, Part Three: Is the Information War Winnable?(UPDATED)
How to be an InformationWar Activist - Part Four: What the heck IS Information War? (UPDATED)
How to be an InformationWar Activist - Part Five: The American Deep State (RESTEEMED)
How to be an InformationWar Activist - Part Six: The Personal Price (UPDATED)
How to be an InformationWar Activist - Part Seven: Who Might The Players be?(Updated)
How to be an InformationWar Activist - Part Eight: Making Sense of Multiple Levels of Corruption(Updated)
How to be an InformationWar Activist, Part Nine: The Power of Decentralization As A Tool (Updated)
How to be an InformationWar Activist - Part Ten: Committees of Correspondence, The first American Information War?
How to be an InformationWar Activist - Part Eleven: Your Health and Information War
Steemit writers contributing to understanding Information War
@dragon40 - Civil War Diary
@lifeworship
@phibetaiota - Information War, OSINT
@fortified
@krnel - Critical Thinking/Cognitive Bias
@richq11 - Political Science
@dwinblood - Critical Thinking
@rebelskum - http://pizzagate.wiki, Din's Fire
@ausbitbank
@titusfrost
@canadian-coconut
@cupidzero - Subversion of the educational system
@ozmaga - counter-propaganda
@odinthelibrarian - OSINT, infosec
@newsagg
Study Resources
- Some Resources for Studying Propaganda
- Index of Critical Thinking and Fighting the Information War
- Journal of Information Warfare
- INFORMATION WARFARE AND INFORMATION OPERATIONS (IW/IO): A BIBLIOGRAPHY
- https://www.zotero.org/stevedisme/items
Database focused on subjects like COINTELPRO, domestic security/intelligence, the security vs liberty balance, Constitutional (American) law re:security, leftism, islamism, propaganda, police intelligence, morality, neoconservatism, globalism, Information War, propaganda, and the Deep State
